A
virtual private network (VPN) is the extension of a private network
that encompasses links across shared or public networks like the
Internet. A VPN allows data to be sent between two computers across the
Internet in a manner that emulates a point-to-point private link. With a
virtual private network, illustrated in Figure 1,
a private link is created between the client and the VPN server by
encrypting the data for confidentiality; data packets that are
intercepted while traveling through the Internet are unreadable without
the proper encryption keys.
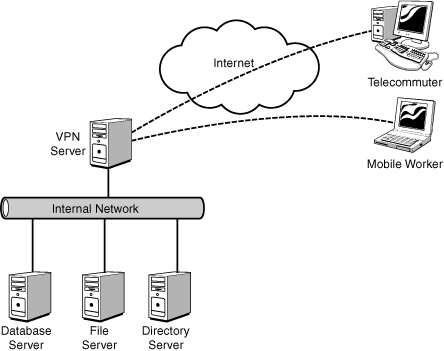
VPN technology provides
corporations with a scalable and low-cost solution for remote access to
corporate resources, such as database, file, and directory servers. VPN
connections allow remote users to securely connect to their corporate
networks across the Internet. Remote users would access resources as if they were physically connected to the corporate local area network (LAN).
Note
A
new technology introduced with Windows Server 2008 R2 called
DirectAccess is discussed. Microsoft has positioned DirectAccess as
being different from a traditional VPN. This positioning is based mainly
on the automated nature of DirectAccess, rather than on technical or
architectural differences. DirectAccess is technically a VPN.
Windows Server 2008 R2 RRAS Features and Services
Windows Server 2008 R2
builds on the Routing and Remote Access features that were provided by
Windows NT 4.0, Windows 2000 Server, Windows Server 2003, and Windows
Server 2008. Routing and Remote Access in Windows Server 2008 R2
includes all of the VPN features and services from previous versions of
the Windows Server product and adds several key features.
The following VPN features were provided by Windows NT 4.0:
The following additional VPN features were provided by Windows 2000 Server:
Layer 2 Tunneling
Protocol (L2TP) over Internet Protocol Security (IPSec) support for
router-to-router VPN connections and remote access.
Demand-dial
routing that can route IP and Internetwork Packet Exchange (IPX) over
on-demand or persistent wide area network (WAN) links, such as analog
phone lines, Integrated Services Digital Network (ISDN), or over VPN
connections that use either PPTP or L2TP over IPSec.
RRAS integration that provides the capability to integrate a firewall with RRAS and Network Address Translation (NAT) functions.
Windows Server 2003
continued the evolution of RRAS by adding some new features. Some of the
Routing and Remote Access Service for Windows Server 2003 features
included the following:
Windows Server 2008 added
new VPN functionality and improved on some of the existing
functionality. The features new in Windows Server 2008 included the
following:
Network Policy
Server (NPS) to provide access control and to assess, validate, and
remediate the health of clients; this replaces the Windows Server 2003
Quarantine Policy Check.
Secure
Socket Tunneling Protocol (SSTP) to provide for HTTPS VPN tunnels over
port 443 to seamlessly provide connectivity over firewalls, NAT, and web
proxies.
Point-to-Point
Protocol (PPP), which now supports the use of Protected EAP (PEAP) with
PEAP-MS-CHAP v2 and PEAP-TLS for better security.
Full IPv6 support in addition to IPv4 support, both of which coexist completely.
New Connection Manager Administration Kit (CMAK) features, such as multiple language support.
Connection Manager, which now supports Dynamic DNS client registration.
Network
Diagnostics Framework Client-based connections to support basic
diagnostics capabilities with the Network Diagnostics Framework.
New
cryptographic L2TP/IPSec-based VPN connections, which now support the
Advanced Encryption Standard (AES) with 128- and 256-bit keys.
Windows Server 2008 R2 shows evolutionary progress in the area of remote access.
VPN
Reconnect enables users to transparently reconnect to traditional VPN
connections even when roaming or changing networks, which is made
possible through the implementation the IKEv2 mobility function, MOBIKE.
Components Needed to Create a Traditional VPN Connection
A
point-to-point link, or tunnel, is created by encapsulating or wrapping
the data with a header that provides routing information that allows
the data to travel through the Internet. A virtual private network
connection requires a VPN client and a VPN server or infrastructure. A
secured connection is created between the client and server through
encryption that establishes the tunnel, as shown in Figure 2.
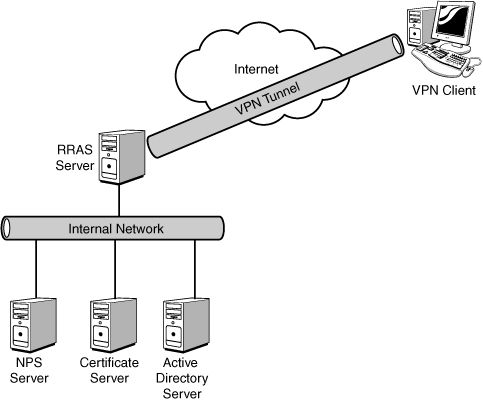
The tunnel is the portion
of the connection in which data is encapsulated. The VPN connection is
the portion of the connection where the data is encrypted. The data
encapsulation, along with the encryption, provides a secure VPN
connection.
Note
A tunnel that is created
without the encryption is not a VPN connection because the private data
is sent across the Internet unencrypted and can be easily read. This
violates the “P” for Private in a Virtual Private Network (VPN).
The figure also depicts the
roles in a typical Windows 2008 VPN infrastructure. The roles in
Windows Server 2008 R2 consist of the following:
These roles work together to provide the VPN functionality.
A shared or public
internetwork is required to establish a VPN connection. For Windows
Server 2008 R2, the transit internetwork is always an IP-based network
that includes the Internet as well as a corporation’s private IP-based
intranet.
The VPN Client
A VPN client is a
computer that initiates a VPN connection to a VPN server. Microsoft
clients, including Windows NT 4.0, Windows 9x, Windows 2000, Windows XP,
Windows Vista, and Windows 7, can create a remote access VPN connection
to a Windows Server 2008 R2 system.
VPN clients can also be any non-Microsoft PPTP client or L2TP client using IPSec.
The RRAS Server
An RRAS server is a Windows
Server 2008 R2 server with the Network Policy and Access Services role
installed and the Routing and Remote Access Service role services
installed. This is the server that accepts VPN connections from VPN
clients. The RRAS server name or IP address must be resolvable as well
as accessible through corporate firewalls, which could be by either
having a network interface connected to the demilitarized zone (DMZ) or
by providing the appropriate access rule on the firewall.
The NPS System
The Network Policy
Server (NPS) provides the authentication, authorization, auditing, and
accounting for the VPN clients. The NPS system has the Network Policy
and Access Services role installed with the Network Policy Server role
service installed. In Windows Server 2008, NPS was an English-only
solution. In Windows Server 2008 R2, support is added for non-English
character sets.
The Network Policy Server
(NPS) is used to enforce network access policies for client health,
client authentication, and client authorization. NPS works with Network
Access Protection (NAP), which is a technology to manage, enforce, and
remediate client health. The NPS service provides the policies for NAP
to validate against. NPS also has multiple templates for larger-scale
deployments or configuring multiple NPS servers identically.
In NAP, System Health Agents
(SHAs) are used to inspect and assess the health of clients according to
policies. System Health Validators (SHVs) are the policies that the
agents validate against.
The Windows Security
Health Agent is the SHA in Windows 7 and the Windows Security Health
Validator is the SHA in Windows Server 2008 R2. These provide the
following features in their SHVs:
Firewall software installed and enabled
Antivirus software installed and running
Current antivirus updates installed
Antispyware installed and running
Current antispyware updates installed
Microsoft Update Service enabled
These are configured in the
client health policies or SHVs on the NPS. When a client attempts a
connection, the client SHA will send a Statement of Health (SoH) to the
NPS system. The SoH is compared with the health policy, resulting in a
pass or a fail. Based on that result, the NPS does one of four actions.
In the case of a pass (that is, the client is healthy), it just allows
the client to connect. In the case where the SoH fails the policy
comparison (that is, the client is unhealthy), the NPS can prevent the
client from connecting, connect the client to a restricted network, or
even allow the client to connect even though it is unhealthy, as shown
in Table 1.
Table 1. NPS Actions
| SoH Versus Policy | NPS Action |
|---|
| Passes | Client is allowed to connect. |
| Fails | Client
is not allowed to connect; client is connected to a restricted network;
or client is allowed to connect even if it is deemed unhealthy. |
When a client fails and is
not allowed to connect, that is straightforward. When the client fails
and is connected to a restricted network, this allows the client to
connect to secured remediation servers to download software, patches,
and/or updates to be remediated. The SHA can even conduct remediation
automatically and then allow the client to connect. Interestingly, in
some cases, the client might fail and yet the policy still allows it to
connect. This might be for reporting purposes.
Additionally, third-party SHVs and SHAs can be written that access the NAP application programming interface (API).
Remediation server groups can be
configured to restrict noncompliant VPN clients to just those servers
where software and updates are stored. After the appropriate software
and updates are applied that bring the client into compliance, the NPS will allow the clients full access to the network.
This server handles VPN client
authentication requests for the RRAS server and validates those requests
against its policies. This allows for a centralized policy and access
control, while allowing the RRAS server role to be scaled out as needed.
Certificate Server
The certificate server is a
Certificate Authority (CA) that issues certificates for the servers and
clients to use in the authentication and encryption of tunnels. In
Windows Server 2008 R2, this is a Windows Server 2008 R2 server with the
Active Directory Certificate Services role installed with the
Certification Authority and the Certification Authority Web Enrollment
role services installed. These roles also require some other supporting
roles to be installed, such as the Web Server (IIS) role and the File
Services role.
Using Windows Server
2008 R2 allows the administrator to issue and control certificates for
the VPN infrastructure. This could also be handled by a third-party CA
such as VeriSign, thereby not requiring a server albeit at an annual
cost.
Although not a requirement for
all configurations of the VPN infrastructure, certificates are
considered a best practice to enhance the security of the VPN
infrastructure. An AD certificate server is always required for
DirectAccess deployment.
Active Directory Server
The Active Directory server
provides the authentication database for the VPN client users. In
Windows Server 2008 R2, this is a server with the Active Directory
Domain Services role installed.