Exploring DNS Server Properties Tabs
The DNS server
properties dialog box allows you to configure settings that apply to the
DNS server and all its hosted zones. You can access this dialog box in
the DNS console tree by right-clicking the DNS server you want to
configure and then selecting Properties, as shown in Figure 1.
The DNS server properties dialog box contains eight tabs, which are introduced next.
Interfaces Tab
The
Interfaces tab allows you to specify which of the local computer’s IP
addresses the DNS server should listen to for DNS requests. For example,
if your server is multihomed and has one IP address for the local
network and another IP address connected to the Internet, you can
prevent the DNS server from servicing DNS queries from outside the local
network. To perform this task, specify that the DNS server listen only
on the computer’s internal IP address, as shown in Figure 2.
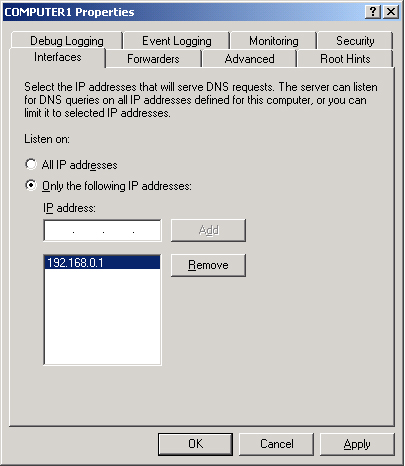
By default, the setting
on this tab specifies that the DNS server listens on all IP addresses
associated with the local computer.
Forwarders Tab
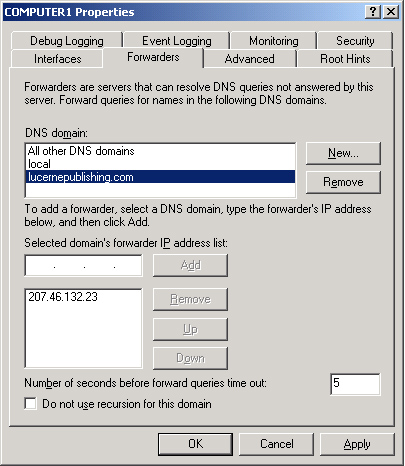
The Forwarders tab allows you to forward DNS queries received by the local DNS server to upstream DNS servers, called forwarders.
Using this tab, you can specify the IP addresses of the upstream
forwarders, and you can specify the domain names of queries that should
be forwarded. For example, in Figure 3,
all queries received for the domain lucernepublishing.com will be
forwarded to the DNS server 207.46.132.23. When, after receiving and
forwarding a query from an internal client, the local forwarding server
receives a query response back from 207.46.132.23, the local forwarding
server then passes this query response back to the original querying
client. The process of forwarding selected queries in this way is known
as conditional forwarding.
In
all cases, a DNS server configured for forwarding uses forwarders only
after it has determined that it cannot resolve a query using its
authoritative data (primary or secondary zone data) or cached data.
Tip
To
specify how long the forwarding server should wait for a response from a
forwarder before timing out, on the Forwarders tab, enter a value in
the Number Of Seconds Before Forward Queries Time Out text box. The
default setting is 5. |
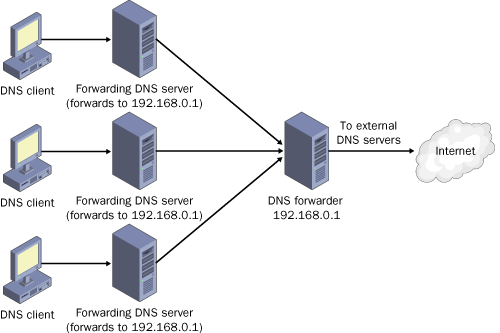
When to Use Forwarders
In some cases,
network administrators might not want DNS servers to communicate
directly with external servers. For example, if your organization is
connected to the Internet by means of a slow wide area link, you can
optimize name resolution performance by channeling all DNS queries
through one forwarder, as shown in Figure 4.
Through this method, the server cache of the DNS forwarder has the
maximum potential to grow and reduce the need for external queries.
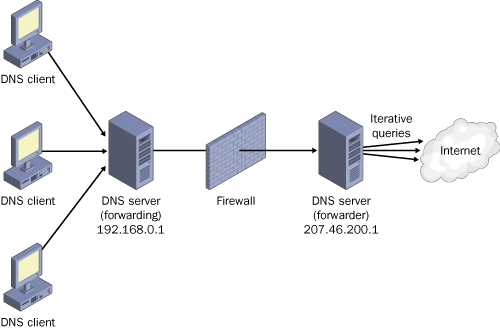
Another
common use of forwarding is to allow DNS clients and servers inside a
firewall to resolve external names securely. When an internal DNS server
or client communicates with external DNS servers by making iterative
queries, normally the ports used for DNS communication with all external
servers must be left open to the outside world through the firewall.
However, by configuring a DNS server inside a firewall to forward
external queries to a single DNS forwarder outside your firewall, and by
then opening ports only to this one forwarder, you can resolve names
without exposing your network to outside servers. Figure 5 illustrates this arrangement.
Disabling Recursion
The
Forwarders tab allows you to disable recursion on any queries,
specified by domain, that have been configured to be forwarded to an
upstream server. When recursion is not disabled (the default), the local
DNS server attempts to resolve a fully qualified domain name (FQDN)
after a forwarder has failed to do so. This condition is preferable if
you want to optimize settings for fault tolerance: if the upstream
forwarder is down, name resolution can fall back to the local DNS
server.
However, when under
this default setting the forwarder receives the forwarded query and
still fails to resolve it, the subsequent fallback recursion that occurs
at the local DNS server is usually redundant and delays an inevitable
query failure message response. Disabling recursion on queries for which
forwarding has been configured thus optimizes the speed of negative
query responses at the expense of fault tolerance.
When forwarders are configured this way in combination with disabling recursion, the local DNS server is known as a slave server because in these cases, it is completely dependent on the forwarder for queries that it cannot resolve locally.
Note
Do not confuse the use of the term slave server with the term slave zone,
which is used in some implementations of DNS. In some non-Microsoft DNS
servers, such as Berkeley Internet Name Domain (BIND), primary zones
are called master zones and secondary zones are called slave zones. |
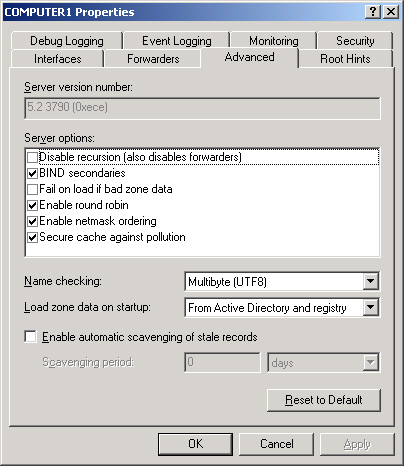
Advanced Tab
The Advanced tab, shown in Figure 6,
allows you to enable, disable, and configure certain DNS server options
and features such as recursion, round robin, automatic scavenging, and
netmask ordering.
Note
Whereas
the Forwarders tab allows you to disable recursion on selected queries
for domains used with forwarders, the Advanced tab allows you to disable
recursion for all queries received by the local DNS server. |
Note
If
you disable recursion on a DNS server using the Advanced tab, you
cannot use forwarders on the same server, and the Forwarders tab becomes
inactive. |
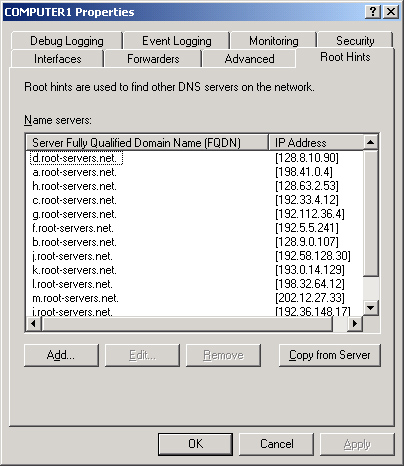
Root Hints Tab
The
Root Hints tab contains a copy of the information found in the WINDOWS\
System32\Dns\Cache.dns file. For DNS servers answering queries for
Internet names, this information does not need to be modified. However,
when you are configuring a root DNS server (named “.”) for a private
network, you should delete the entire Cache.dns file. (When your DNS
server is hosting a root server, the Root Hints tab itself is
unavailable.)
In addition, if you
are configuring a DNS server within a large private namespace, you can
use this tab to delete the Internet root servers and specify the root
servers in your network instead.
Note
Every
few years, the list of root servers on the Internet is slightly
modified. Because the Cache.dns file already contains so many possible
root servers to contact, it is not necessary to modify the root hints
file as soon as these changes occur. However, if you do learn of the
availability of new root servers, you can choose to modify your root
hints accordingly. As of this writing, the last update to the root
servers list was made on November 5, 2002. You can download the latest
version of the named cache file from InterNIC at ftp://rs.internic.net /domain/named.cache. |
Figure 7 shows the Root Hints tab.
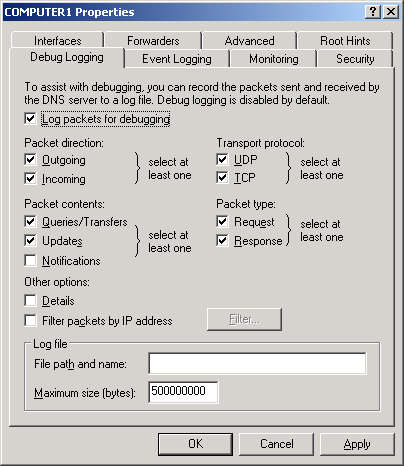
Debug Logging Tab
The Debug Logging tab
allows you to troubleshoot the DNS server by logging the packets it
sends and receives. Because logging all packets is resource-intensive,
this tab allows you to restrict which packets to log, as specified by
transport protocol, source IP address, packet direction, packet type,
and packet contents.
Figure 8 shows the Debug Logging tab.
Event Logging Tab
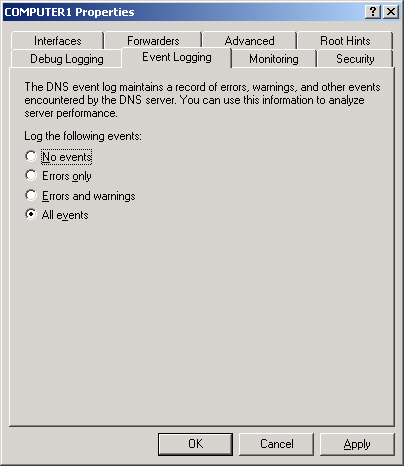
You can access the DNS Events log through the Event Viewer node in the DNS console.
The Event Logging tab, shown in Figure 9,
allows you to restrict the events written to the DNS Events log file to
only errors or to only errors and warnings. It also allows you to
disable DNS logging. For more powerful features related to the filtering
of DNS events, use the Filtering tab of the DNS Events Properties
dialog box. You can open this dialog box by selecting Event Viewer in
the left pane of the DNS console, right-clicking DNS Events in the right
pane, and selecting Properties.
Monitoring Tab
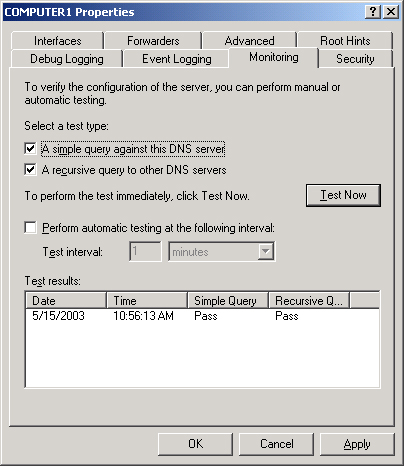
The
Monitoring tab allows you to test basic DNS functionality with two
simple tests. The first test is a simple query against the local DNS
server. To perform the first test successfully, the server must be able
to answer forward and reverse queries targeted at itself.
The second test is a
recursive query to the root DNS servers. To perform this second test
successfully, the DNS server computer must be able to connect to the
root servers specified on the Root Hints tab.
The Monitoring tab, shown in Figure 10,
also allows you to schedule these tests to be conducted at regular
intervals. The results of the tests, whether performed manually or
automatically, are shown in the Test Results area of the tab.
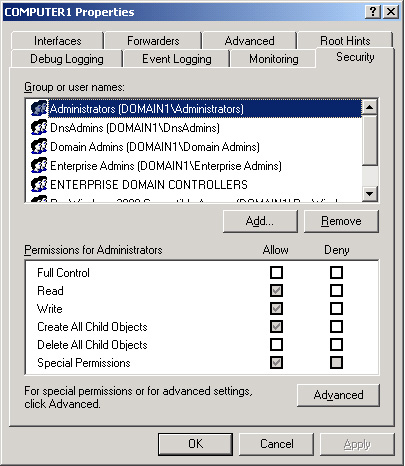
Security Tab
The Security tab is
available only when the DNS server is also a domain controller. This tab
allows you to control which users are granted permissions to view,
configure, and modify the DNS server and its zones. By clicking the
Advanced button, you can further refine settings related to DNS server
permissions.
Figure 11 shows the Security tab.