Configuring Remote Access Authentication
After the dial-up client
calls the remote access server and the necessary IP addresses are
assigned, the credentials submitted with the connection must be
authenticated. Authentication
is the process of validating—through verification of a password or of
alternative credentials such as a certificate or smart card—that the
user is in fact the person he or she claims to be. Remote access
authentication precedes domain logon authentication; if a dial-up user
is attempting to log on to a domain remotely, the dial-up connection
must be authenticated, authorized, and established before normal domain
logon occurs.
Note
Whereas authentication refers to the process of validating user credentials, authorization
refers to the process of allowing users access to resources. After
remote access authentication occurs, the remote access connection is
authorized only if the proper permissions are configured both on the
dial-up properties of the user account and in the remote access policy
that applies to the connection.
|
To log on to a domain through
a dial-up connection, select the Log On Using Dial-Up Connection check
box in the Log On To Windows dialog box. Then, after you type in your
user name and password and click OK, a Network Connections dialog box
appears. In the Choose A Network Connection drop-down list box, select
the network connection you have configured for dial-up remote access,
and then click Connect. The dial-up connection is then attempted; remote
access authentication and authorization follow. Typically, the user
name, domain, and password configured for the connection match those you
submit for domain logon, but these two sets of credentials are
configured and authenticated separately.
If the credentials of the
dial-up connection are successfully authenticated, and if the remote
access connection is authorized, a remote access connection is
established. Normal domain logon follows; the credentials you enter in
the Log On To Windows dialog box are submitted to a domain controller
for domain authentication.
Note
If
a user is dialing in to a stand-alone remote access server that is not a
member of a domain, the user must first log on to his or her local
computer or local domain before attempting to connect to the remote
server. In this case, the remote computer’s verification of the
credentials sent with the dial-up connection is the only authentication
that needs to occur before the connection is authorized and established.
These credentials must be stored in the answering server’s local
Security Accounts Manager (SAM) before the user connects. |
Performing Authentication Through RADIUS
You can configure remote
access authentication to be performed through Windows authentication or
through a Remote Authentication Dial-In User Service (RADIUS) server.
Through Windows authentication, when the remote user attempts to dial up
to a workgroup computer, the NAS authenticates the connection by
verifying the user name and password in the server’s own local security
database. When the remote user attempts to dial in to a domain, the NAS
forwards the authentication request to the domain controller. However,
when you configure a RADIUS server to authenticate remote access
connections, the NAS passes both the authentication and authorization
responsibility to a central server running IAS.
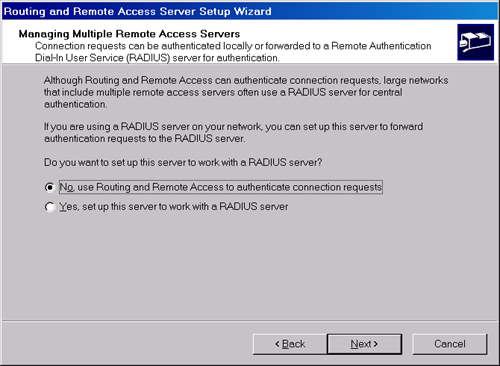
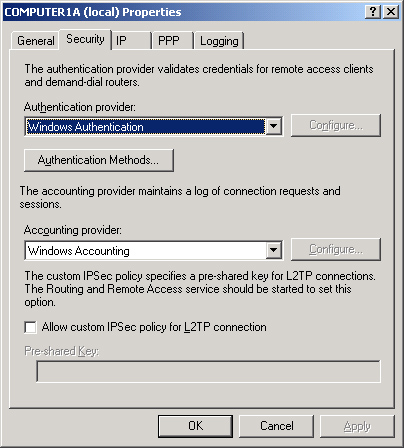
You
choose this authentication method in one of two places: on the Managing
Multiple Remote Access Servers page of the Routing And Remote Access
Server Setup Wizard, as shown in Figure 5, or on the Security tab of the server properties dialog box in the Routing And Remote Access console, as shown in Figure 6.
Note that in the wizard, if you want to use Windows authentication
instead of a RADIUS server, you should select the option No, Use Routing
And Remote Access To Authenticate Connection Requests.
Choosing Authentication Protocols
To
authenticate the credentials submitted by the dial-up connection, the
remote access server must first negotiate a common authentication
protocol with the remote access client. Most authentication protocols
offer some measure of security so that user credentials cannot be
intercepted, and authentication protocols in Windows clients and servers
are assigned a priority based on this security level.
The authentication
protocol chosen for a remote access connection is always the most secure
of those enabled in the client connection properties, the remote access
server properties, and the remote access policy applied to the
connection. For all remote access clients and servers running either
Microsoft Windows 2000, Microsoft Windows XP, or the Microsoft Windows
Server 2003 family, by default, that protocol is Microsoft Challenge
Handshake Authentication Protocol version 2 (MS-CHAP v2).
The following is a
complete list of the authentication protocols supported by Routing And
Remote Access in Windows Server 2003 (listed in order from most secure
to least secure):
Extensible Authentication Protocol-Transport Level Security (EAP-TLS) A certificate-based authentication based on EAP,
an extensible framework that supports new authentication methods.
Typically used in conjunction with smart cards. Supports encryption of
both authentication data and connection data. Note that EAP-TLS is not
supported on stand-alone servers; the remote access server running
Windows Server 2003 must be a member of a domain.
MS-CHAP v2
A mutual authentication method offering encryption of both
authentication data and connection data. New cryptographic key is used
for each connection and each direction of transmission. Enabled by
default in Windows 2000, Windows XP, and Windows Server 2003.
MS-CHAP v1
A one-way authentication method offering encryption of both
authentication data and connection data. Same cryptographic key is used
in all connections. Supports older Windows clients such as Microsoft
Windows 95 and Microsoft Windows 98. (See Table 10-2 for a complete list of operating system compatibility.)
Extensible Authentication Protocol-Message Digest 5 Challenge Handshake Authentication Protocol (EAP-MD5 CHAP)
A version of CHAP (see next bullet) ported to the EAP framework.
Supports encryption of authentication data through the industry-standard
MD5 hashing scheme. Provides compatibility with non-Microsoft clients,
such as those running Mac OSX. Does not support encryption of connection
data.
Challenge Handshake Authentication Protocol (CHAP) A
generic authentication method offering encryption of authentication
data through the MD5 hashing scheme. Provides compatibility with
non-Microsoft clients. The group policy applied to accounts using this
authentication method must be configured to store passwords using
reversible encryption. (Passwords must be reset after this new policy is
applied.) Does not support encryption of connection data.
Shiva Password Authentication Protocol (SPAP)
A weakly encrypted authentication protocol offering interoperability
with Shiva remote networking products. Does not support encryption of
connection data.
Password Authentication Protocol (PAP)
A generic authentication method that does not encrypt authentication
data. User credentials are sent over the network in plaintext. Does not
support encryption of connection data.
Unauthenticated access
Not an authentication protocol but a configuration option which—when
set on the network access server and remote access policy applied to the
connection—allows remote access connections to connect without
submitting credentials. Can be used to troubleshoot or test remote
access connectivity. Does not support encryption of connection data.
Table 1 provides information to help you map your requirements to the appropriate protocol.
Table 1. Authentication Protocol Features
| Requirement | Select |
|---|
| Encrypted
authentication support for Windows 95, Windows 98, Microsoft Windows
Millennium Edition (Me), or Microsoft Windows NT 4 remote access clients
(native support) | MS-CHAP v1 |
| Encrypted
authentication support for Windows 95, Windows 98, Windows Me, or
Windows NT 4 remote access clients (with the latest Dial-Up Networking
upgrade) | MS-CHAP v2 (VPN only for Windows 95) |
| Encrypted
authentication support for certificate-based Public Key Infrastructure
(PKI), such as those used with smart cards (when the remote access
server is a member of a Windows 2000 Server or Windows Server 2003
domain) | EAP-TLS |
| Encrypted authentication support for other Windows 2000, Windows XP, and Windows Server 2003 remote access clients | MS-CHAP v2 |
| Mutual authentication (client and server always authenticate each other) | EAP-TLS, MS-CHAP v2 |
| Support for encryption of connection data | MS-CHAP v1, MS-CHAP v2, EAP-TLS |
| Encrypted authentication support for remote access clients that use other operating systems | CHAP, EAP-MD5 CHAP |
| Encrypted authentication support for remote access clients running Shiva LAN Rover software | SPAP |
| Unencrypted authentication when the remote access clients support no other protocol | PAP |
| Authentication credentials not supplied by the remote access client | Unauthenticated access |
Authentication Protocols: Operating System Support
Table 2 summarizes the authentication protocols supported in various versions of Windows.
Table 2. Authentication Protocol Support
| Dial-Up Networking Client | Supported Authentication Protocol | Unsupported Authentication Protocol |
|---|
| Windows Server 2003, Windows XP, Windows 2000 | MS-CHAP, CHAP, SPAP, PAP, MS-CHAP v2, and EAP |
| Windows NT version 4 | MS-CHAP, CHAP, SPAP, PAP, and MS-CHAP v2 (with Windows NT 4.0 Service Pack 4 and later) | EAP |
| Windows NT version 3.5 and version 3.51 | MS-CHAP, CHAP, SPAP, and PAP | MS-CHAP v2, and EAP |
| Windows Me, Windows 98 | MS-CHAP, CHAP, SPAP, PAP, and MS-CHAP v2 (with Windows 98 Service Pack 1 and later) | EAP |
| Windows 95 | MS-CHAP,
CHAP, SPAP, and PAP (with the Windows Dial-Up Networking 1.3
Performance & Security Upgrade for Windows 95 and later) | MS-CHAP v2 and EAP |
Configuring Authentication Protocols: Client Side
To view or modify the
authentication protocols enabled for a dial-up connection on the remote
access client, open the properties dialog box of the dial-up connection
on the client, and click the Security tab.
Figure 7
shows the default settings on the Security tab: the Typical
(Recommended Settings) option is selected, and the Allow Unsecured
Password setting is selected. If you click the Advanced (Custom
Settings) option and then click the Settings button, the Advanced
Security Settings dialog box opens. This dialog box, also shown in Figure 7,
reveals the specific authentication protocols enabled by the current
setting. Notice that the unencrypted authentication protocol PAP is
enabled. The authentication protocol SPAP is also enabled. Although it
encrypts authentication data, SPAP is not considered secure because it
always sends each password over the network in the same reversibly
encrypted form. Thus, the protocol is susceptible to replay attacks.

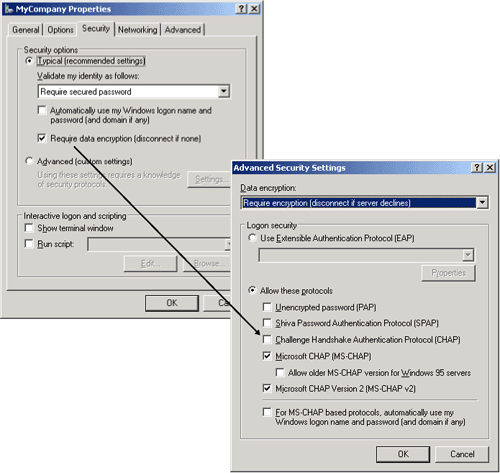
When you select the Require Secured Password setting on the Security tab, as shown in Figure 8,
the Advanced Security Settings dialog box reveals a different set of
enabled authentication protocols. Specifically, only CHAP, MS-CHAP v1,
and MS-CHAP v2 are enabled. The less secure PAP and SPAP are no longer
available.

When you select the Require Data Encryption (Disconnect If None) check box, as shown in Figure 9,
the list of enabled authentication protocols is further restricted.
Specifically, only MS-CHAP v1 and MS-CHAP v2 are enabled, and CHAP is no
longer available. For all authentication protocols except PAP,
authentication data (user name and password) is encrypted. However, the
MS-CHAP protocols also support encryption of PPP connection data through
Microsoft Point-to-Point Encryption (MPPE). For the connection data to
be successfully encrypted, the remote access policy applied to the
connection must require data encryption. (Remote access policies do
require data encryption by default.)
Note
The
EAP-TLS authentication protocol also allows for encryption of PPP
connection data. However, this protocol requires configuration and is
not automatically enabled by the Require Data Encryption (Disconnect If
None) setting on the Security tab of the connection. |
Finally, when you select the Use Smart Card setting, as shown in Figure 10,
only the EAP-TLS authentication protocol is enabled. On the client, the
EAP-TLS protocol is designated by the Smart Card Or Other Certificate
(Encryption Enabled) selection under the Use Extensible Authentication
Protocol (EAP) option.

Configuring Authentication Protocols: Server Side
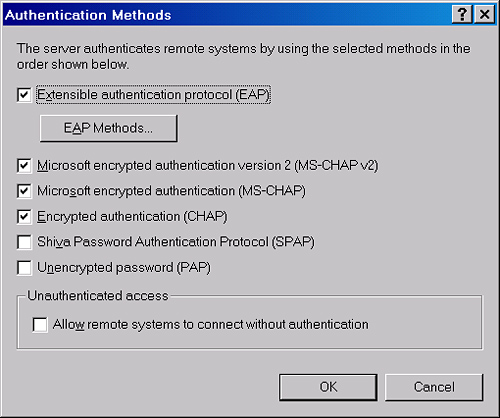
To
view or modify the authentication protocols enabled on the remote
access server, right-click the server icon in the Routing And Remote
Access console and then click Properties. In the server properties
dialog box, select the Security tab. On the Security tab, click the
Authentication Methods button to open the Authentication Methods dialog
box, shown with its default settings in Figure 11.
Finally,
to view or modify the authentication protocols allowed by a remote
access policy, select the Remote Access Policies node in the Routing And
Remote Access console, double-click the appropriate policy, and then
click the Edit Profile button in the policy properties dialog box. In
the Edit Dial-In Profile dialog box, select the Authentication tab. Figure 12 shows the default settings of this tab. Note that by default, no EAP methods are enabled.
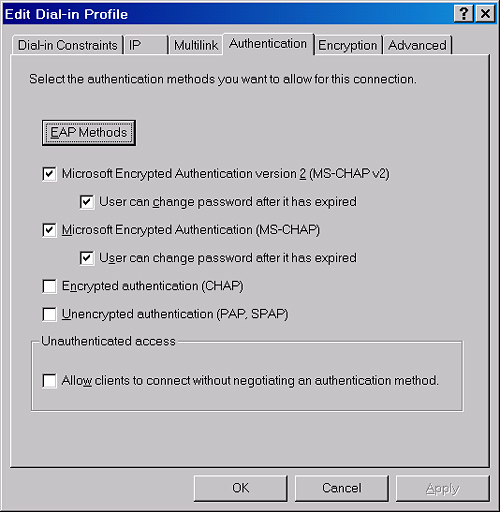
To configure authentication settings in a remote access policy, complete the following steps:
1. | Perform one of the following tasks:
Open the Routing And Remote Access console and, if necessary, double-click Routing And Remote Access and the server name. Open the Internet Authentication Service console and, if necessary, double-click Internet Authentication Service.
|
2. | In the console tree, click Remote Access Policies.
|
3. | In the details pane, double-click the policy that you want to configure.
|
4. | Click Edit Profile.
|
5. | On the Authentication tab, specify any required settings.
|
6. | Click OK. |