Once a baseline security configuration for your
servers is in place, you can consider the special needs of the servers
performing particular roles in your enterprise. Domain controllers,
infrastructure servers, file and print servers, and application servers
all are vulnerable to unique threats, and their security requirements
can be quite different. By combining the policy settings in a
role-specific GPO with those in your baseline configuration, you can
create a secure environment for each server role without much
duplication of effort.
Securing Domain Controllers
On a Windows Server
2003 network that uses Active Directory, no servers are more vital than
the domain controllers. Because domain controllers provide
authentication services for most network operations and store and
distribute group policies, their failure or compromise can be a
catastrophe for network productivity.
Tip
Be
sure to understand the operational differences between the various
server roles, including domain controllers, infrastructure servers,
application servers, and file and print servers. |
Isolating Domain Controllers
Because of the
importance of domain controllers, your security measures should minimize
the threats to the computers in every possible way. Physically, domain
controllers should always be in a secured location, such as a server
closet or a data center, which is accessible only to administrative
personnel who have reason to be there. Secure the console with a complex
password, so that even people who are in the room for other reasons are
not able to access the server.
In addition to
limiting physical access to your domain controller, you should limit the
access provided by the network connection. This means reducing the
number of open ports on the computer by minimizing the number of
applications and services it runs.
Many
domain controllers running Windows Server 2003 also run the DNS Server
service, because DNS is intimately associated with Active Directory, but
you should avoid running services and applications that are unnecessary
to the domain controller role.
Setting Audit and Event Log Policies
When you install Active
Directory on a computer running Windows Server 2003 and create a new
domain, the system puts the domain controller’s computer object in an
organizational unit called Domain Controllers and creates a GPO that is
linked to that organizational unit. The Domain Controllers container’s
GPO provides some additional security settings beyond the default
settings in the domain’s GPO, but you might want to augment or modify
them.
For
example, the Domain Controllers container’s GPO enables the following
audit policies, but configures them to audit only successes:
Depending on the
policy settings you use in your baseline security configuration, you
might want to modify these settings to audit failures as well as
successes, or to define additional policies such as Audit Object Access
and Audit Process Tracking. If you decide to implement additional audit
policies, be sure to consider the Event Log policies as well, because
you might have to specify a larger maximum size for the security log to
hold all the entries that these policies create.
Assigning User Rights
The
default domain GPO created by Windows Server 2003 contains no user
rights assignments, but the default Domain Controllers container’s GPO
does. Most of the user rights that the GPO assigns using these policies
are intended to give administrators the access they need to manage the
domain controller, while granting users only the minimum rights they
need to use the domain controller’s services. For the most part, the
settings for the User Rights Assignment policy in the default Domain
Controllers container’s GPO are acceptable, and you should use them on
your domain controllers. However, there are a few changes that you might
want to make.
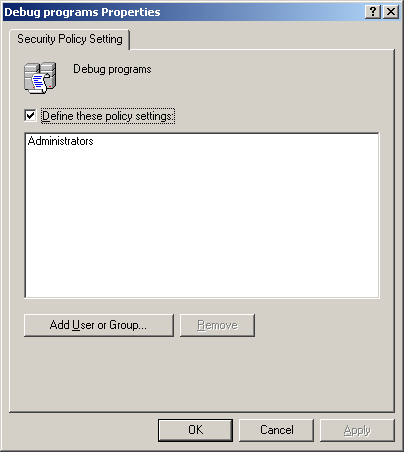
Debug Programs
The Debug Programs user right enables you to use a debugging tool to
access any process running on the computer or even the operating system
kernel itself. Software developers use these tools to debug applications
that they are in the process of creating. This user right provides
access to sensitive areas of the operating system that a potential
intruder might be able to abuse. By default, the GPO linked to the
Domain Controllers organizational unit grants this right to the
Administrators group (see Figure 1).
However, if no one in your organization is developing or debugging
software, you can revoke the Debug Programs user right from the
Administrators group and close what could be a serious security breach.
Add Workstations To Domain
By default, all authenticated users have the right to add up to ten
computer accounts to an Active Directory domain. Adding an account
creates a new computer object in the Computers container. Computer
accounts are full security principals in Windows Server 2003, able to
authenticate and access domain resources. This right can allow any
authenticated user to create unauthorized domain workstations that an
intruder could use when the computer account is idle.
Many large network
installations rely on IT support personnel to install new workstations
and manually create new computer objects. In this case, you can revoke
the Authenticated Users group’s Add Workstations To Domain right without
causing problems.
Allow Log On Locally The
Allow Log On Locally user right enables specified users and groups to
log on to the computer interactively from the console. Obviously, users
with this right have access to many important operating system elements,
and could cause a great deal of damage, either accidentally or
deliberately. It is therefore important to grant this right only to
users and groups that absolutely need it.
Tip
Users
who connect to a domain controller using Terminal Services also require
the Allow Log On Locally user right. Be sure to account for these users
when modifying the default user rights assignments. |
The default Domain Controllers container’s GPO grants the Allow Log On Locally user right to the following built-in groups:
Account Operators
Administrators
Backup Operators
Print Operators
Server Operators
How (or whether) you
use the built-in groups is your decision, but, based on their intended
use, the Account Operators and Print Operators groups typically do not
need to perform their tasks from a domain controller console, so you can
usually revoke these two groups’ Allow Log On Locally right.
Shut Down The System
You should control the ability to shut down a domain controller very
carefully, because shutting down a domain controller can affect systems
all over the network. The default Domain Controllers container’s GPO
grants this user right to the following groups:
Administrators
Backup Operators
Print Operators
Server Operators
In most
environments, members of the Backup Operators and Print Operators groups
should not need to shut down a domain controller, so you can revoke
their right to do this.
Important
For
the restrictions imposed by your assignments of Shut Down The System
user right to be meaningful, you must also revoke the Security Options
policy, Shutdown: Allow System To Be Shut Down Without Having To Log On.
If you enable this option, any user can shut down the computer without
authentication, which means that they are not subject to user rights
restrictions. |
Configuring Services
Domain controllers require the following additional services, which you
should enable in the System Services container of your Domain
Controllers container’s GPO, using the Automatic startup type: