3. How to Configure Event Forwarding in Workgroup Environments
Typically, event forwarding is required only in large environments that use AD DS domains.
However, you can also configure event forwarding in workgroup environments. The process is very similar to that used in AD DS
environments, with the following exceptions:
You must add a Windows Firewall exception for Remote Event Log Management on each
forwarding computer. You must add an account with administrator privileges to the Event Log Readers local
group on each forwarding computer. You must specify this account in the Configure Advanced
Subscription Settings dialog box when creating a subscription on the collector
computer. On each collecting computer, run the following command to allow the forwarding computers
to use NTLM authentication: winrm set winrm/config/client
@{TrustedHosts="<forwarding_computers>"}. Provide a comma-separated list of forwarding computers for the <forwarding
computers> value in the previous example. Alternatively, you can provide a wildcard,
such as msft*.
Tip:
For the exam, remember that you must configure the
TrustedHosts
parameter on the collecting computer, not the forwarding computer. This
is counterintuitive and might be hard to remember.
4. How to Troubleshoot Event Forwarding
If event forwarding doesn't seem to function properly, follow these steps to troubleshoot
the problem:
Verify that you have waited long enough for the event to be forwarded. Forwarding events
using the Normal setting can take up to 15 minutes. The delay might be longer if either the
forwarding or the collection computer has restarted recently because the Windows Remote
Management service is set to start automatically, but with a delay so that it doesn't affect
startup performance. The 15-minute counter doesn't start until after the Windows Remote
Management service has started. Check the Applications And Services
Logs\Microsoft\Windows\Eventlog-ForwardPlugin\Operational event log and verify that the
subscription was created successfully. Event ID 100 indicates a new subscription, whereas
Event ID 103 indicates a subscription has been unsubscribed. Check the Security event log to verify that the forwarding and collecting computers are
authenticating correctly.
Verify that the subscription is Active. On the collecting computer, browse to Event
Viewer\Subscriptions. The subscription status should be Active. If it is not, right-click the
subscription and then click Runtime Status. Event Viewer displays the Subscription Runtime
Status dialog box with an error code. Verify that the forwarding computer has the Windows Remote Management listener properly
configured. From an elevated command prompt, run the following command: winrm
enumerate winrm/config/Listener. If the Windows Remote Management listener isn't configured, there is no output. If the
Windows Remote Management listener is configured properly for HTTP, the output resembles the
following: Listener
Address = *
Transport = HTTP
Port = 80
Hostname
Enabled = true
URLPrefix = wsman
CertificateThumbprint
ListeningOn = 127.0.0.1, 192.168.1.214, ::1, fe80::100:7f:ffe%9,
fe80::5efe:192.168.1.214%10
If the Windows Remote Management listener is configured properly for HTTPS, the output
resembles the following (note that the host name must match the name the event collector uses
to identify the computer): Listener
Address = *
Transport = HTTPS
Port = 443
Hostname = win7.nwtraders.msft
Enabled = true
URLPrefix = wsman
CertificateThumbprint = 52 31 db a8 45 50 1f 29 d9 3e 16 f0 da 82 ae
94 18 8f 61 5e
ListeningOn = 127.0.0.1, 192.168.1.214, ::1, fe80::100:7f:ffe%9,
fe80::5efe:192.168.1.214%10
Verify that the collecting computer can connect to Windows Remote Management on the
forwarding computer. From an elevated command prompt on the collecting computer, run the
following command: winrm id
-remote:<computer_name>.<domain_name>. For example, if the forwarding computer is named win7.nwtraders.msft, you would run the
following command: winrm id -remote:win7.nwtraders.msft. The result would be as follows: IdentifyResponse
ProtocolVersion = http://schemas.dmtf.org/wbem/wsman/1/wsman.xsd
ProductVender = Microsoft Corporation
ProductVersion = OS: 6.0.6000 SP: 0.0 Stack: 1.0
If you receive the message "WS-Management could not connect to the specified
destination," verify that the Windows Remote Management service is started on the forwarding
computer and that no firewall is blocking connections between the two computers. Verify that the user account you configured the subscription to use has privileges on
the forwarding computer. If necessary, enable failure security auditing on the remote
computer , wait for events to be forwarded, and
then examine the Security event log for logon failures. In addition, you can configure the
subscription temporarily to use a Domain Admin account—if the subscription works
with the Domain Admin account, the source of your problem is definitely related to
authentication. Troubleshoot the authentication problem and reconfigure the subscription to
use the original user account. If the subscription is configured to use Machine Account authentication, verify that the
collecting computer's account is a member of the forwarding computer's Event Log Readers
local group. If the subscription is configured to use a different user account, that account
must be in the forwarding computer's Event Log Readers local group. Verify that the following services are started on the forwarding computer: Verify that the Windows Event Collector service is started on the collecting
computer. Verify Windows Firewall settings on the forwarding computer as follows: Verify that the Windows Remote Management (HTTP-In) firewall exception is
enabled. If you are using HTTPS instead of HTTP, verify that you have created and enabled a
custom firewall exception for TCP port 443. Verify that the forwarding computer and the collecting computer are both connected to
Private or Domain networks, rather than to Public networks. To verify the network profile,
right-click the network icon in the system tray and then click Open Network And Sharing
Center. In the Network And Sharing Center, the profile type appears after the network name.
If it shows Public Network, click Customize and change the profile type to Work Network,
which uses the private network profile.
In addition to the forwarding computer, verify that the Windows Remote Management
(HTTP-In) firewall exception is enabled on the collecting computer. Verify that a network firewall is not blocking traffic by testing connectivity. Because
the forwarding computer must have HTTP (and possibly HTTPS) available, you can attempt to
connect to it from the collecting computer by using Windows Internet
Explorer—simply type http://computername (or https://computername if you are using HTTPS) in the Address bar. If the
firewall on the forwarding computer is configured correctly, you receive an HTTP 404 error
and Internet Explorer displays the message, "The webpage cannot be found." If Internet
Explorer displays the message, "Internet Explorer cannot display the webpage," the firewall
exception on the forwarding computer has not been enabled. Verify that the event query is valid by performing these steps: View the subscription properties, and click Select Events. Select the XML tab, select the contents of the query, and press Ctrl+C to copy it to
the Clipboard. Open a second instance of Event Viewer. Right-click Event Viewer, and then click
Connect To Another Computer. Select the forwarding computer, and then click OK. Right-click Custom Views, and then click Create Custom View. In the Create Custom View dialog box, select the XML tab. Select the Edit Query
Manually check box, and click Yes when prompted. Click the query box and press Ctrl+V to paste the query. Then click OK. The new custom view appears and shows the matching events. If any events have appeared
since you created the event forwarder, they should have been forwarded. If there are no new
events, the problem is with your forwarding criteria. Try creating a custom view that
matches the events that you want to forward and then importing that into a new
subscription.
4.1. PRACTICE: Forward Events Between Computers
4.1.1. PRACTICE: Forward Events Between Computers
In this practice, you configure event forwarding between two computers using the default
settings.
EXERCISE 1 Configuring a Computer to Collect Events
In this exercise, you configure a computer to collect events.
Log on to the computer running Windows 7 that you want to use to collect events using a domain account with
administrative privileges. Open an elevated command prompt by clicking Start, typing cmd, and pressing
Ctrl+Shift+Enter. At the command prompt, run the following command to configure the Windows Event
Collector service: wecutil qc
When prompted to change the service startup mode to Delay-Start, type Y, and then press Enter.
EXERCISE 2 Configuring a Computer to Forward Events
In this exercise, you configure a computer running Windows 7 to forward events to the
collecting computer. To complete this exercise, you must have completed Exercise 1.
Log on to the computer running Windows 7 that you want to use to forward events using
a domain account with administrative privileges. Open an elevated command prompt by clicking Start, typing cmd, and pressing Ctrl+Shift+Enter. At the command prompt, run the following command to configure the Windows Remote
Management service: winrm quickconfig. When prompted to change the service startup mode, type Y, and then press Enter. When prompted to create the WinRM listener and enable the firewall exception, type
Y and then press Enter. Verify that you have updated the Windows Firewall configuration by following these steps: Click Start and then click Control Panel. Click the System And Security link. Click the Windows Firewall link. Click the Advanced Settings link. Select the Inbound Rules node. In the Details pane, verify that the Windows Remote Management (HTTP-In) exception
is enabled for the Domain and Private profiles.
Verify that the Windows Remote Management service is configured to start automatically
by following these steps: Click Start, type services.msc, and then press
Enter. In the Services console, select the Windows Remote Management (WS-Management)
service. Verify that it is started and that the Startup Type is set to Automatic (Delayed
Start).
Now you need to grant the collecting computer permission to read this computer's event
log. If you skipped this step, you would need to configure the subscription to use an
administrative user account. To grant access to the collecting computer account, perform
these steps: Click Start, right-click Computer, and then click Manage. Under System Tools, expand Local Users And Groups. Then, select Groups. Double-click Event Log Readers. In the Event Log Readers Properties dialog box, click Add. In the Select Users, Computers, Service Accounts, Or Groups dialog box, click Object
Types. By default, it searches only Users and Groups. However, we need to add the
collecting computer account. Select the Computers check box and clear the Groups, Users,
and Service Accounts check boxes. Click OK. In the Select Users, Computers, Or Groups dialog box, type the name of the
collecting computer. Then, click OK. Click OK again to close the Event Log Readers Properties dialog box.
EXERCISE 3 Configuring an Event Subscription
In this exercise, you create an event subscription to gather events from the forwarding
computer. To complete this exercise, you must have completed Exercises 1 and 2.
Log on to the computer running Windows 7 that you want to use to collect events using a domain account with
administrative privileges. Click Start, right-click Computer, and then click Manage. In the Computer Management console, expand System Tools, expand Event Viewer,
right-click Subscriptions, and then click Create Subscription. In the Event Viewer dialog box, click Yes to configure the Windows Event Collector
service (if prompted). The Subscription Properties dialog box appears. In the Subscription Name box, type Windows Defender Warnings And
Errors. Click Select Computers. In the Computers dialog box, click Add Domain Computers. Type
the name of the computer that will be forwarding events, and then click OK. In the
Computers dialog box, click Test to verify that you can connect to the forwarding computer.
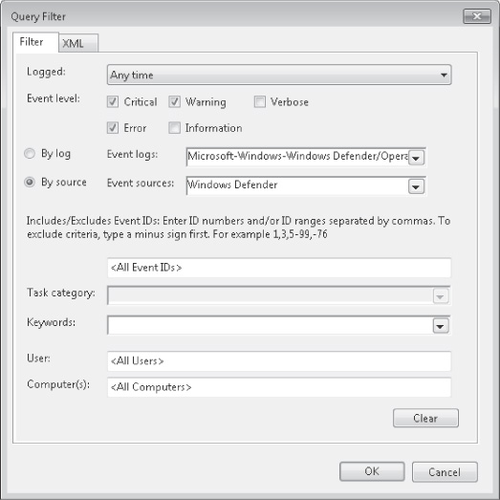
Click OK twice. Click Select Events. In the Query Filter dialog box, select the Error, Critical,
Warning, and Information check boxes. Click By Source. Then, click the Event Sources list
and select Windows Defender (as shown in Figure 4). Click OK.
Click Advanced to open the Advanced Subscription Settings dialog box. Note that it is
configured to use the Machine Account by default. This works because we have added this
computer's domain account to the forwarding computer's Event Log Readers local group. Also,
note that the subscription is configured by default to use Normal Event Delivery
Optimization using the HTTP protocol. Click OK. In the Subscription Properties dialog box, click OK. Next, generate a Windows Defender event on the forwarding computer by following these
steps: Log on to the forwarding computer. Click Start and type Defender. On the Start menu,
click Scan For Spyware And Other Potentially Unwanted Software. Windows Defender scans the computer and adds an event to the event log.
While still using the forwarding computer, open Event Viewer and check the Applications And Services Logs\Microsoft\Windows\Windows Defender\Operational
log. You should see several Informational events with a source of Windows Defender. Using the collecting computer, select the Forwarded Events event log. If you don't see
the Windows Defender event immediately, wait a few minutes—it might take up to 15
minutes for the event to appear.
|