You will attach a policy to the service entry point to the POProcessing composite to authenticate based on the user ID/password in the SOAP header (usernameToken). The identity of the client is securely propagated to the credit card validation composite using a SAML
token. The invocation of the credit card validation composite passes
sensitive data. Hence, you should sign and encrypt the message. This is
done by attaching the appropriate policies to the reference in the POProcessing composite to invoke validationForCC and to the service entry point to validationForCC composite.
After testing the secured service, you detach the policies.
Defining a new user
You use the Weblogic console to define a new user that you use in this exercise.
1. Log into the Weblogic console at http://localhost:7001/console.
2. Click on Security Realms and then click on myrealm.
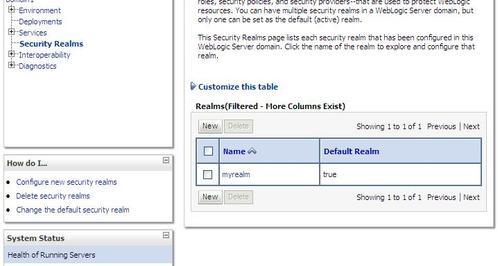
3. Click on the Users and Groups tab.
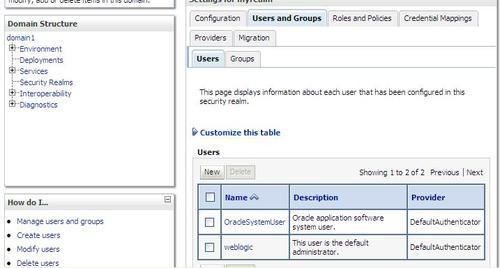
5. Create a new user weblogic1 with password welcome1 and click on OK.
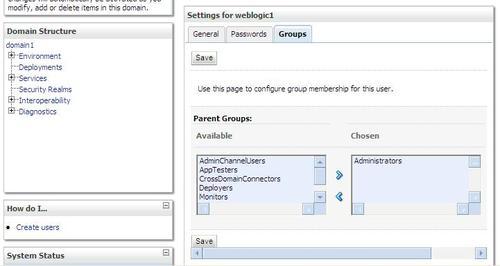
6. Click on the weblogic1 user and then click on Groups tab.
7. Select Administrators as the group and click on Save.
Attaching the policies
1. Log into the EM console at http://localhost:7001/em.
2. Click on the POProcessing composite link.
3. Click on the Policies tab.
4. Select receivePO in the Attach To/Detach From drop-down.
5. Select wss_username_token_service_policy, click on Attach, and click on OK.
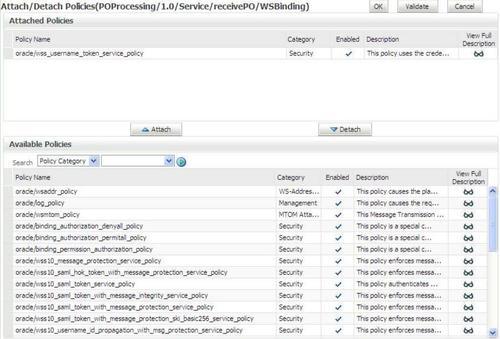
6. Similarly, attach the policy wss11_saml_token_with_message_protection_client_policy to the attach point getCreditCardStatus.
7. Similarly, attach the policy wss11_saml_token_with_message_ protection_service_policy to the attach point getStatusByCC in the validationForCC composite.
8. Test using the EM test console.
9. Test POProcessing using the EM test console. Be sure to select WSS Username Token and specify the user ID/password as weblogic1/welcome1.
10. Retest, but specify an invalid password. You will see an authentication failure error.
11. Test validationForCC.
But this time, do not specify any WSS Username Token. You will see an
error because the SAML token is not present and the message is not
signed and encrypted.
Detaching policies
1. Click on the POProcessing composite link.
2. Click on the Policies tab.
3. Select receivePO in the Attach To/Detach From drop-down.
4. Select the attached wss_username_token_service_policy, click on Detach, and click on OK.
5. Similarly detach the policy wss11_saml_token_with_message_protection_client_policy from the attach point getCreditCardStatus.
6. Similarly detach the policy wss11_saml_token_with_message_ protection_service_policy from the attach point getStatusByCC in the validationForCC composite.
Attaching and detaching policies in JDeveloper
To
attach/detach policies in JDeveloper, right-click on services,
references, and components in the composite view and choose Configure WS
Policies. Try to repeat the exercise you did in the EM console by
yourself, but this time, use JDeveloper.