4. Naming Standards
Naming AD components is entirely up to the architect.
Windows doesn't really care what you name anything as long as most
objects have a unique name within the domain or the forest. The name
uniqueness is especially important when migrating multiple Windows NT
domains into a single AD domain or fewer AD domains; there can only be
one group called Sales and only one computer account called PC1. Also
NetBIOS has the 15-character limit and DNS names in Windows 2000 are
limited to 64 characters including the dot (“.”) delimiters. However,
naming standards from a design and troubleshooting perspective is
important. This section discusses suggested naming strategies for
various objects. Defining a standard naming practice allows for growth
in the eventuality of a merger, acquisition, or expansion of the
business without throwing the AD into disarray.
Naming standards are especially true in
troubleshooting. No matter how well you design the AD, something will
break and you'll be on the phone with Microsoft or HP or someone who
will need to understand your environment. When you start listing names
like Skywalker, Yoda, Darth, and HanSolo, you will not only be a little
embarrassed, but the poor support person on the other end of the line
will have a hard time telling whether Yoda is in Atlanta or Singapore
and whether it's a GC or an application server, even if he knows that
Skywalker is in Los Angeles. Besides, from a pure security standpoint,
it's best to name your servers without a special naming convention that
could lead a hacker to the best server to attack in the enterprise.
However, when you start to increase the number of servers, and run out
of Star Wars characters, what will you do?
General Standards
Determine the general standards that will be employed
in names. These standards can include things like the length of names,
inclusion of special characters, and how naming standards can be
modified.
Domain Namespace
You must choose an appropriate name for the Windows
2000 or 2003 domain that will be the root of your domain tree. For
Windows NT 4.0 environments, you probably already have a public domain
name that hosts an external Web site and supplies your e-mail address
identification, such as HP.com or Microsoft.com.
However, selecting the internal Windows domain name presents some
interesting challenges, such as whether you will use the same namespace
for internal as well as external use. For example, Compaq used
Compaq.com for the external space (e-mail, external Web site, and so on)
and Cpqcorp.net for the internal namespace.
Problems with the domain namespace can arise if you
are part of a larger parent company that has not migrated to Windows
Server 2003 yet. For example, a county attorney's office we were working
with was actually controlled by the county's IT department, and the
county attorney's office only had a staff of three people for IT
support. The attorney's office wanted to migrate to Windows 2000, but
the rest of the county offices were either at Windows NT 4.0 or using
Netware or UNIX environments. The problem with choosing the name early
is that when the county goes to Windows 2000, and it chooses a different
name, the attorney's office will have to migrate to the new structure.
Our recommendation was to talk to the IT manager and determine what the root name would be if
the county goes to Windows 2000. Because the county already had a root
DNS name for its UNIX infrastructure, it would probably be that name.
After the attorney's office determined that name, it could take two
servers, promote them to create the county root domain (remember you
never want to do fewer than two DCs for redundancy), create the county
attorney's office domain as a child to the county root, and then build
everything off of that. Figure 12 depicts the expansion under this configuration.
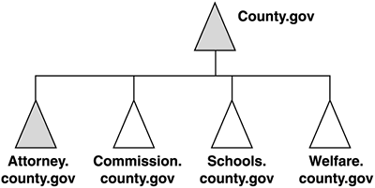
When the county decides to implement Windows 2000, it
simply joins its servers to the root domain already established and
demotes the DCs in the attorney's office if desired. The county attorney
domain can continue uninterrupted, and other county offices can join as
separate domains. In case they adopt a single domain for the county
with OUs for each county department, the county attorney's office would
need to migrate from the domain to the OU, which would be fairly easy
because it would be an intra-forest migration. The problem, of course,
is that the IT department could decide to use a different name when
actually creating the Windows Server 2003 environment. However, Windows
Server 2003 would add additional flexibility by allowing the county to
rename that root domain.
tip
Windows Server 2003 removes a lot of the fear of
naming domains and forests with the Domain Rename feature. Microsoft
refers to this as “removing irreversible decisions.” However, Domain
Rename is complex and has restrictions that might prevent you from using
it in your infrastructure, so you still need to plan carefully.
Security Principals
Security principals are defined as users, computers,
and groups. These objects usually have names associated with actual
names (for users) or with descriptive functions. For instance, a user
object might have the user's actual name—for example, Tyler
Olsen—whereas a group might be labeled HRAdmins to describe the usage.
On the other hand, other objects, such as servers and printers, contain
location information such as site or domain affiliation. You can
determine these names in a variety of ways. Some options to consider are
noted here:
Users:
Your e-mail mailbox-naming scheme should be used here, especially if you
are using Exchange 2000 or newer. Beginning in Exchange 2000, the
Exchange user account is the same as the AD user account with the
mailbox and other Exchange required attributes added. You need to have
procedures in place to deal with duplicate usernames as well. A company
acquisition can really create havoc with usernames. When the HP/Compaq
merger caused the HP Windows NT 4.0 accounts to be merged with the
Compaq Windows 2000 environment, a couple of thousand usernames had
duplicates. The company decided to just add a number such as -1 at the
end of the HP Windows NT accounts and increment for each duplicate. That
is, the second instance of a name would have a -2, and so on.
Third-party migration tools, allow you to set rules to handle duplicate names.
Workstations:
The challenge here is to maintain uniqueness in the names as a security
principal in the domain. That is, you don't want an OU with the same
name as a workstation. You might use a user's employee number (if not
her Social Security number) and perhaps employ a prefix or suffix if
users have more than one workstation each.
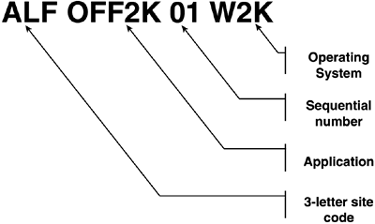
Servers:
Servers can have many different functions. A well-designed name can help
identify the server without making it unwieldy and hard to remember
(and type). Figure 13 shows one suggestion for a server naming standard.
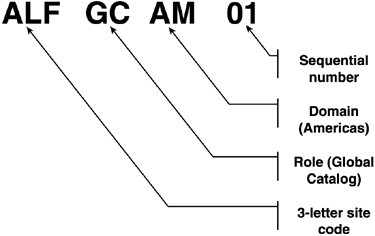
DCs:
DCs are similar to application, file, and print servers, but because
their application is always the same, it isn't necessary to have a
variety of labels for different applications. Figure 14 shows how one company named its DCs. DCs typically include the site and domain as well as a sequential number.
tip
Keep track of DC names, because it's possible to
create duplicates. If a DC is offline during the DCPromo process of
another machine, DCPromo performs a NetBIOS broadcast for the name. If
there is no response, it permits the name. We ran into this in HP's
Qtest environment. Even with Microsoft's help, we could not clean up all
the references for the two machines with the same name. We had to
reinstall both machines (though now you could do a manual demotion) and
be sure to never use that name again.
Groups:
Groups can be labeled with the domain (if a multiple domain structure),
type (universal, global, local, domain local), and a code to identify
special-purpose groups. For instance, if you have an application called
HR Reports, and you need to create a global group of Administrators for
that application, you might call it HRReports-GG. Again, the trick here
is to make names descriptive without making them unwieldy. This becomes
more difficult when many data Administrators have been delegated the
rights to create groups in their OU within the same domain. Because
groups also need to be unique in a domain, it can be beneficial to add
the name or code of the Administrative entity (OU containing the group
or the group's sub-OU) to the name of the group simply to avoid
duplicates.
Printers:
Printer names usually contain descriptive features, such as the model
(for example, LJ4) and whether it is public or assigned to a group
(restricted access). The important thing here is to make the printer
name easy to remember. Note that if the printer is published in AD,
additional information such as location can be added to allow users to
find printers with the AD search function.
Sites:
Sites are usually named for the city they represent, although it might
also be a U.S. state or a country. For a a college campus, sites might
be buildings. If your company occupies a large high-rise building, sites
might even be the floors of the building. Develop a descriptive name
that is no more than seven or eight characters even if you have to
abbreviate it somewhat. The recommendation for naming site links uses
two site names in the link name, so the length of link names can easily
get very long if you aren't careful.
Site Links:
These replication topology objects are used to link two or more sites,
although they seldom include more than two sites. The naming strategy
that seems to work well is xxxxx-yyyyyy. For instance, a link connecting
the Atlanta and Chicago sites would be Atlanta-Chicago. This makes the
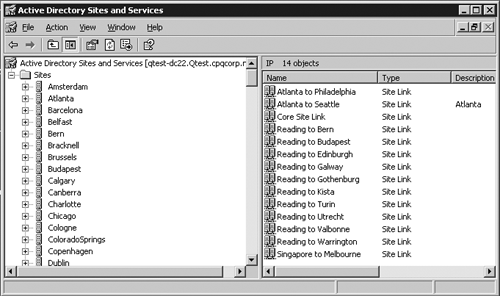
links easy to identify and is great for troubleshooting. Figure 15
shows HP's Qtest site link list from the AD Sites and Services snap-in.
In this example, three core sites sit on the corporate backbone:
Atlanta (US), Reading (UK), and Singapore (AsiaPacific). We decided to
name the links always starting with the core site name. The snap-in
alphabetizes them in an easy-to-read format. Note how easy it is to find
a link. The only link that contains more than two sites is the core
link, which contains the three core sites of Atlanta, Reading, and
Singapore because they all have the same cost and scheduling.
GPOs:
These should be descriptive for the function of the policy. Consider
adding the name of the domain or OU it is linked to and a short
descriptive part, such as “scripts” or “desktopLkdwn”. Because GPOs can
change over time due to changing demands in the infrastructure, it's
also beneficial to add a version number to the GPO name, simply for
documentation and recovery reasons. A GPO that defines EFS settings for
the users in the Marketing OU, for example, might be called
“EFSMKTGPolicyV1.0”.