9.1.4. Working with ADMX/ADML files
Despite the fact that Vista GPOs include up to
2450 settings, there is always one setting that you cannot find but want
to control. This is done by using administrative templates.
Administrative templates are structured text files which allow you to
modify components in the system registry. These templates are imported
into the GPO of your choice through GPEdit. In GPEdit, go to the
settings you want to control: either computer or user, right-click on
Administrative Templates in the Tree pane and select Add/Remove
Templates. In the Add/Remove Templates dialog box, click the Add button.
Navigate to the appropriate template, select it, and click Open. Close
the Add/Remove Template dialog box when done.
Prior to Windows Vista, all GPO definition
templates used an ADM file format — pure text files that were organized
in a structured manner. With Vista, Microsoft introduces the ADMX format
— a format based on the Extended Markup Language (XML), which provides
much richer content for GPO templates. Note that ADMX templates no
longer need to be imported into GPOs; they are automatically referenced
when GPEdit is opened.
ADMX templates are now language independent,
globalizing Group Policy settings. Each ADMX file is accompanied by one
or more ADML files which include language-specific content. Global
organizations will want to include an ADML file for each language their
administrators work in. In addition, ADMX files can be centrally stored
as opposed to the distributed approach used by ADM files — one on each
domain controller in a particular AD domain. And, because of the
increased number of policy settings in Vista, 132 ADMX files are
included in the release version of Vista by default.
Because of the changes to Group Policy in Vista,
the ADMX format is incompatible with the ADM format. Environments who
manage a mix of Windows 2000 and/or XP with Vista need to either
translate their existing templates to ADMX format or create new ones.
Organizations that want to make sure critical settings are applied to
all of their Windows clients need to put in place a strategy that
supports the translation of ADM to ADMX and vice versa, but of course,
only for the settings that apply to specific Windows versions. ADM and
ADMX files can coexist together. End users and end machines will have no
awareness as to whether the policy settings were configured from Vista
or Windows 2000 or XP. However, it is a good idea to think about
migrating your existing ADM files to ADMX format.
The location of administrative templates has
also changed with Vista. In the earlier Windows versions, ADM files were
located in the directory %WINDIR%\INF. Note that text-based ADM templates are still located in this folder. Now ADMX files are located in %WINDIR%\PolicyDefinitions and the corresponding ADML files are placed in %WINDIR\PolicyDefinitions\<LanguageFolder>.
In previous versions of Windows, each time a new
ADM template was created it would be copied from the local system to
the SYSVOL share on a domain controller. It would then be copied to
every DC in the domain. This method was cumbersome and could lead to
errors. If a user had an outdated ADM template on their system, it could
overwrite the proper one. It was difficult to have an authoritative
store for ADM templates.
In Vista, ADMX template files are obtained by
default from the PC they are generated from. If you have multiple
technicians working on ADMX templates, then it is a good idea to create a
central ADMX file store that will be referenced each time someone needs
to edit a GPO no matter which machine they use. The central store is
usually created by a server administrator because it involves changes in
a domain controller, something PC technicians often don't have access
to. Follow these steps to create the central store:
Log on with domain administrative rights.
Locate the PDC Emulator domain controller in your network.
The easiest way to do this is to open the Active Directory Users and
Computers console and right-click on the domain name to choose
Operations Masters, click on the PDC tab to find the name of the DC.
Then use Explorer to navigate to its SYSVOL shared folder. You use the
PDC Emulator because it is the engine which drives GPO changes in the
network.
Navigate to the SYSVOL\domainname\Policies folder where domainname is the DNS name of your domain.
Create a new folder called PolicyDefinitions.
Copy the contents of the C:\Windows\PolicyDefinitions from any Windows Vista PC to the new folder created in Step 4.
Include the appropriate ADML folders. For example, U.S. English systems would use the en-US folder.
Launch the Group Policy Editor. From now on, it will automatically reference the new central store as will all editors on any Vista PC in your domain.
Make sure that you create this central store as
soon as possible to help mitigate any potential versioning issues with
your templates.
|
There is no Group Policy interface for loading
ADMX files into a GPO. If you want to add new settings based on an ADMX
file, create the ADMX file and copy it to your central store. It will
appear in the Group Policy Object as soon as you reopen GPEdit.
|
|
5. Assigning PC-Related GPOs
To create your own GPOs, you need to think
through each one of the changes you want to apply to your systems. There
are lots of different settings you can apply, but the most common are
listed in Table 4.
Remember that if you are using Windows Server 2008 domain controllers,
you must use Policy in the path after either Computer Configuration or
User Configuration.
Table 4. Recommended Computer Configuration Group Policy Object Settings
| Setting | Application |
|---|
| Software Settings | Use
this setting to deploy software in your organization. Deploy software
to PCs (Computer Configuration section) instead of users. This
automatically makes the software available to all users on a PC and
makes it easier to manage. Multiple packages can be deployed in the same
GPO. |
| Windows Settings | This
section lets you control scripts, deploy printers, security settings,
and Quality of Service (QoS) communications. Scripts are normally
applied to users (User Configuration section). Printers are deployed to
groups of users or groups of computers. Security settings are most often
assigned in the Default Domain Policy so that they apply to all systems
and user accounts. |
| Administrative Templates | Administrative
templates let you control most of the settings in a GPO. You can set
regional and language options, control user account behavior, control
network and printer behavior, and work with both system and Windows
components. |
| Administrative Templates => Network => Offline Files | Offline
files allow users to work on local copies of files that are normally
stored on a server. Configure these settings to control the
synchronization behavior between PCs and servers. |
| Administrative Templates => Network => Windows Connect Now | This
section is useful for mobile workers because it controls the behavior
of their system when a wireless connection is available. |
| Administrative Templates => Printers | Controls how Vista PCs interact with printers. |
| Administrative Templates => System | Controls
items such as logon or logoff messages, as well as the locations of
service pack and Windows Installer installation files. |
| Administrative Templates => System => Device Installation | Controls
whether or not users can plug in USB storage devices. This is quite
useful when you do not want users to walk away with confidential data. |
| Administrative Templates => System => Driver Installation | Controls
whether non-administrators can install specified device drivers or not.
This is useful for mobile workers who need to add devices while on the
road. |
| Administrative Templates => System => Folder Redirection | Controls
the location (local versus remote) of user data folders such as
Documents, Pictures, Videos, and more. Helps protect user data by moving
it to centralized storage areas. |
| Administrative Templates => System => Group Policy | Controls the general behavior of Group Policy. |
| Administrative Templates => System => Internet Communication | Controls any Vista activity that requires either use of the HTTP protocol or an Internet connection to function. |
| Administrative Templates, System, Locale Services | Allows you to automatically switch the PC's language to match a user's when they log in to Vista. |
| Administrative Templates => System => Logon or Net Logon | Control the local or network logon behavior of the system. |
| Administrative Templates => System => Power Management | Helps reduce the power consumption of PCs in your organization by putting them on stand-by when not in use. |
| Administrative Templates => System => Remote Assistance | Controls the behavior of the Remote Assistance tool built into Vista. |
| Administrative Templates => System => Removable Storage Access | Controls
whether or not users can rely on removable storage to access data. Use
in environments that need to protect sensitive data. |
| Administrative Templates => System => Scripts | Controls general script behavior such as timeouts and display settings. |
| Administrative Templates => System => Trusted Platform Module Services | Controls
the Trusted Platform Module (TPM) that can be used in conjunction with
BitLocker Full drive Encryption. Used in environments that are sensitive
to laptop theft. |
| Administrative Templates => System => User Profiles | Controls how user profiles are managed in Vista. Should be reviewed to set all defaults for your organization. |
| Administrative Templates => Windows Components | Includes
controls for over 50 Vista components from Movie Maker — something you
probably don't need in your network — to the Task Scheduler and the
Event Viewer. You should take the time to review each of the settings in
this section and assign those you think are best for your organization. |
NOTE
Most settings have default configurations
even if they are listed as Not configured. Make sure you read the
details of the Explanation before you change behavior that might already
be set by default.
As you can see, GPOs can be quite granular and
can control almost any aspect of a PC's behavior. Take the time to
review all of these settings and then determine which ones should be set
to meet your organization's security and system usage policies.
6. Troubleshooting and monitoring Group Policy
GPO issues arise most often when too many
technicians have access to the ability to create GPOs and they
proliferate GPOs at all levels of the directory. It gets even worse when
these technicians do not document the GPOs they create. The first step
you should take to reduce GPO issues is to limit who has control of GPOs
and make sure they always document their changes.
NOTE
For organizations that want tighter control
over their policies, Microsoft offers Advanced Group Policy Management
(AGPM), a tool that is designed to provide change management on all
GPOs. The AGPM is available through the Microsoft Desktop Optimization
Pack for Software Assurance.
If you do run into issues anyway, you can rely
on two tools to resolve them. Both are found in the GPMC. RSoP allows
you to identify the resultant settings on an object that might have
several GPOs applied to it. Modeling lets you perform "what if"
scenarios to see how changes might affect objects.
Troubleshooting GPOS
If a computer or user account is behaving oddly, then perform an RSoP test on the object. Use the following procedure to do so:
Go to Start Menu, Search and then type GMPC.MSC and press Enter. Accept the UAC prompt.
After the GPMC is launched, expand the Forest to view all subitems in the Tree pane.
Right-click on Group Policy Results and select Group Policy Results Wizard. Click Next.
Select
which computer you want to test the policy on. If you are
troubleshooting a policy for a user, select the user's main computer.
Click Another computer and click Browse. Type the computer name and
click Check Names. Click OK.
If
you are testing for a user account only, select the Do not display
policy settings for the selected computer in the results. Otherwise,
click Next.
Identify the user account for which you want to test settings. Click Next.
If you only want computer settings, then select Do not display user policy settings in the results, otherwise, click Next.
Review your selections. Click Back to change settings. Click Next when ready.
Click Finish once the results are generated.
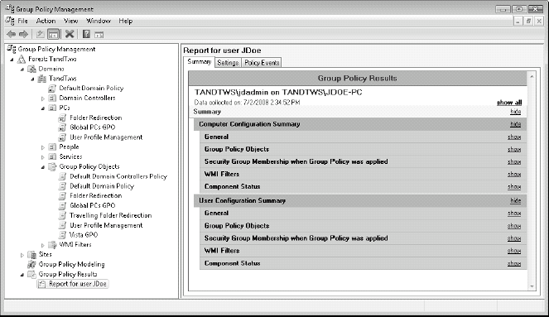
Name the Report and review its contents. Repair any untoward setting assignment.
Reports include several items as shown in Figure 13.
The Details pane includes three tabs. The first, Summary, provides a
summary of all settings. The second, Settings, provides a list of the
actual settings that are applied to the object. The third, Policy
Events, lists all of the events that have occurred on the system in
relation to Group Policy application. Each provides valuable information
in the troubleshooting of GPO application.
NOTE
Be very careful when moving objects in the
directory. Objects are located in specific containers because they are
managed from that particular container. When you move an object, it will
automatically change its management scope and will now receive the GPO
settings that are applied to the new location. If a user or computer
system is facing GPO issues, begin by identifying if the object was
recently moved in the directory.
Performing what-if scenarios
What-if scenarios are also quite useful when
troubleshooting GPOs. They let you identify what would happen if an
object were moved or if a new GPO setting were applied. They are similar
to RSoP but instead of detailing the actual results, they detail
potential results.
Follow these steps to perform a what-if scenario:
Choose Start Menu, =>
Search, type GMPC.MSC, and press Enter. Accept the UAC prompt.
After the GPMC is launched, expand the Forest to view all subitems in the Tree pane.
Right-click on Group Policy Modeling and select Group Policy Modeling Wizard. Click Next.
Select the domain controller to perform the modeling and click Next.
Note that you should not perform this first thing in the morning as
users log on to the network because it affects the domain controller's
performance.
Select either the container or the object.
To simulate for users in a container, select the OU by using the Browse
button. Do the same for computers in a container. For individual
simulations, select the actual object, computer, or user. Click Next.
Identify
that you want to test for Slow network connections or Loopback
processing. Also identify the Site if you need to. Click Next when done.
Select the security user group used to filter the policy. In most cases, this is the Authenticated Users group. Click Next when ready. Repeat for the security computer group.
Select the applicable WMI filter for users if required. Click Next when ready. Repeat for computer WMI filters.
Review your selections. Click Back to change settings. Click Next when ready. Click Finish once the results are generated.
Name the Report and review its contents.
Note that the resulting report is very similar
to the RSoP report. One significant difference is the last tab in the
Details pane. It includes the contents of the query you generated
instead of the events related to GPO processing. Use these two tools to
troubleshoot and repair policy settings in your network.