Enhancing Online Privacy by Managing Cookies
A cookie
is a small text file that’s stored on your computer. It’s used by
websites to “remember” information about your session at that site:
shopping cart data, page customizations, passwords, and so on. No other
site can access the cookie, so they’re generally safe and private under
most—but definitely not all—circumstances. To understand why cookies can
sometimes compromise your privacy, you need to understand the different
cookie types that exist:
Note
The term cookie is based on the old programming term magic cookie,
which is defined as something passed between routines or programs that
enables the receiver to perform some operation. It’s this idea of
passing data from one thing to another (in this case, from a page to
your computer) that inspired the original cookie creators.
Temporary cookie—
This type of cookie lives just as long as you have Internet Explorer
running. When you shut down the program, all the temporary cookies are
deleted.
Persistent cookie—
This type of cookie remains on your hard disk through multiple Internet
Explorer sessions. The cookie’s duration depends on how it’s set up,
but it can be anything from a few seconds to a few years.
First-party cookie— This is a cookie that’s set by the website that you’re viewing.
Third-party cookie—
This is a cookie that’s set by a site other than the one you’re
viewing. Most third-party cookies are created and stored by advertisers
who have placed an ad on the site you’re viewing.
Given these cookie types, there are two ways that your privacy can be compromised:
A site might store personally identifiable information—your
name, email address, home address, phone number, and so on—in a
persistent first- or third-party cookie and then use that information in
some way (such as filling in a form) without your consent.
A
site might store information about you in a persistent third-party
cookie and then use that cookie to track your online movements and
activities. They can do this because they might have (for example) an ad
on dozens or hundreds of websites and that ad is the mechanism that
enables the site to set and read their cookies. Such sites are supposed
to come up with privacy policies stating that they won’t engage in surreptitious monitoring of users, they won’t sell user data, and so on.
To help you handle
these scenarios, Windows XP implements a privacy feature that gives you
extra control over whether sites can store cookies on your machine. To
check out this feature, select Internet Explorer’s Tools, Internet
Options command, and then display the Privacy tab, shown in Figure 2.
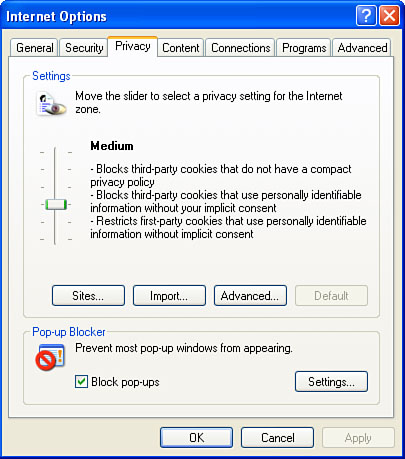
You set your cookie privacy level by using the slider in the Settings group. First, let’s look at the two extreme settings:
Accept All Cookies— This setting (it’s at the bottom of the slider) tells Internet Explorer to accept all requests to set and read cookies.
Block All Cookies— This setting (it’s at the top of the slider) tells Internet Explorer to reject all requests to set and read cookies.
Caution
Blocking
all cookies might sound like the easiest way to maximize your online
privacy. However, many sites rely on cookies to operate properly, so if
you block all cookies you might find that your web surfing isn’t as
convenient or as smooth as it used to be.
In between there are four settings that offer more detailed control. Table 1 shows you how each setting affects the three types of privacy issues:
Table 1. Cookie Settings and Their Effect on Surfing Privacy
| | Third-Party Cookies with No Compact Privacy Policy | Third-Party Cookies Using Personally Identifiable Information Without the Type of Consent | First-Party Cookies Using Personally Identifiable Information Without the Type of Consent |
|---|
| Low | Restricted | Restricted (implicit) | OK |
| Medium (the default) | Blocked | Blocked (implicit) | Restricted (implicit) |
| Medium High | Blocked | Blocked (explicit) | Blocked (implicit) |
| High | Blocked | Blocked (explicit) | Blocked (explicit) |
Here are some notes about the terminology in this table:
Restricted means that Internet Explorer doesn’t allow the site to set a persistent cookie, just a temporary one.
A compact
privacy policy is a shortened form of a privacy policy that can be sent
along with the cookie and that can be read by the browser.
Implicit consent
means that on one or more pages leading up to the cookie, you were
warned that your personally identifiable information would be used and
you agreed that it was okay.
Explicit consent
means that on the page that reads the cookie, you were warned that your
personally identifiable information would be used and you agreed that
it was okay.
Note
If you decide to
change the privacy setting, you should first delete all your cookies
because the new setting won’t apply to any cookies already on your
computer. To delete your cookies, select Tools, Internet Options,
display the General tab, and then click Delete Cookies. If you prefer to
delete individual cookies, click Settings, click View Files, and then
look for filenames that begin with Cookie:.