Blocking Pop-Up Windows
Among the most annoying
things on the Web arethose ubiquitous pop-up windows that infest your
screen with advertisements when you visit certain sites. (A variation on
the theme is the pop under,
a window that opens under your current browser window, so you don’t
know it’s there until you close the window.) Pop-up windows can also be
dangerous because some unscrupulous software makers have figured out
ways to use them to install software on your computer without your
permission. They’re nasty things, any way you look at them.
Fortunately, Microsoft has
given us a way to stop pop-ups before they start. In the Windows XP
Service Pack 2, Internet Explorer comes with a new feature called the
Pop-up Blocker that looks for pop-ups and prevents them from opening.
Follow these steps to use and configure the Pop-up Blocker:
1. | In Internet Explorer, select Tools, Options to display the Internet Options dialog box.
|
2. | Display the Privacy tab.
|
3. | Activate the Pop-up Blocker check box.
|
4. | To
set options for this feature, click Settings to display the Pop-up
Blocker Settings dialog box. You have the following options (click Close
when you’re done):
| Address of Web Site to Allow | Use this option when you have a site that displays pop-ups you want to see. Type the address and then click Add. | | Play a Sound When a Pop-up | When
this check box is activated, Internet Explorer plays a Is Blocked brief
sound each time it blocks a pop-up. If this gets annoying after a
while, deactivate this check box. | | Show Information Bar When a Pop-up Is Blocked | When
this check box is activated, Internet Explorer displays a yellow bar
below the Address bar each time it blocks a pop-up so that you know it’s
working on your behalf. |
|
5. | Click OK.
|
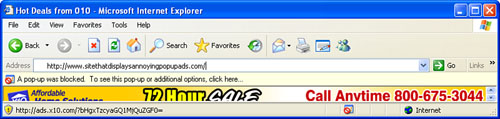
With the Pop-Up Blocker on
the case, it monitors your surfing and steps in front of any pop-up
window that tries to disturb your peace. Figure 3
shows the yellow Information bar that appears under the Address bar to
let you know when a pop-up was thwarted. If you want to see the pop-up
anyway, click the Information bar and then click Show Blocked Pop-up in
the menu that appears.
Understanding Internet Explorer’s Advanced Security Options
To close our look at
Windows XP’s Internet security features, this section takes you through
Internet Explorer’s Advanced security options. To see these options,
select Tools, Internet Options, display the Advanced tab, and then
scroll down to the Security section.
Caution
Don’t surf the Web from an
account with Administrator privileges. An account with Limited User or
Power User privileges is much less susceptible to getting a virus.
Allow Active Content from CDs to Run on My Computer (Service Pack 2)—
Leave this check box deactivated to prevent active content such as
scripts and controls located in CD-based web pages to execute on your
computer. However, if you have a CD-based program that won’t function,
you might need to activate this check box to enable the program to work
properly.
Allow Active Content to Run in Files on My Computer (Service Pack 2)—
Leave this check box deactivated to prevent active content such as
scripts and controls located in local web pages to execute on your
computer. If you’re testing a web page that includes active content,
activate this check box so that you can test the web pages locally.
Allow Software to Run or Install Even If the Signature Is Invalid (Service Pack 2)— Leave
this check box deactivated to avoid running or installing software that
doesn’t have a valid digital signature. If you can’t get a program to
run or install, consider activating this check box.
Check for Publisher’s Certificate Revocation—
When this option is activated, Internet Explorer examines a site’s
digital security certificates to see whether they have been revoked.
Check for Server Certificate Revocation (Requires Restart)— If you activate this option, Internet Explorer also checks the security certificate for the web page’s server.
Check for Signatures on Downloaded Programs— If you activate this check box, Internet Explorer checks for a digital signature on any program that you download.
Do Not Save Encrypted Pages to Disk— If you activate this option, Internet Explorer won’t store encrypted files in the Temporary Internet Files folder.
Empty Temporary Internet Files Folder When Browser Is Closed—
When this option is activated, Internet Explorer removes all files from
the Temporary Internet Files folder when you exit the program.
Enable Integrated Windows Authentication— When this check box is activated, Internet Explorer uses Integrated Windows Authentication—formerly known as Windows NT Challenge/Response authentication—to
attempt to log on to a restricted site. This means the browser attempts
to log on using the current credentials from the user’s network domain
logon. If this doesn’t work, Internet Explorer displays a dialog box
prompting the user for a user name and password.
Enable Profile Assistant— This check box toggles the Profile Assistant on and off. Your profile
is an extra entry in the Windows Address Book that stores your personal
information (name, address, and so on). The Profile Assistant can work
with some websites to share this data, which prevents you from having to
enter this data by hand. To edit your profile, see the options in the
Content tab’s Personal Information group.
Use SSL 2.0—
This check box toggles support for the Secure Sockets Layer Level 2
security protocol on and off. This version of SSL is currently the Web’s
standard security protocol.
Use SSL 3.0—
This check box toggles support for SSL Level 3 on and off. SSL 3.0 is
more secure than SSL 2.0 (it can authenticate both the client and the
server), but isn’t currently as popular as SSL 2.0.
Use TLS 1.0— This check box toggles support for Transport Layer Security (TLS) on and off. This is a relatively new protocol, so few websites implement it.
Warn About Invalid Site Certificates—
When activated, this option tells Internet Explorer to display a
warning dialog box if a site is using an invalid digital security
certificate.
Warn If Changing Between Secure and Not Secure Mode— When activated, this option tells Internet Explorer to display a warning dialog box whenever you enter and leave a secure site.
Warn If Forms Submittal Is Being Redirected—
When activated, this option tells Internet Explorer to display a
warning dialog box if a form submission is going to be sent to a site
other than the one hosting the form.