3. Share Permissions
Folders can be shared on any
computer by creating a share. Within an enterprise, file servers (such
as Windows Server 2008 or Windows Server 2008 R2) are commonly used to
share folders, but it's also possible to share folders on a Windows 7
system. However, the Share permissions are the same on both clients and
servers.
Compared to NTFS
permissions, Share permissions are much simpler. There are only three
permissions, but they take different names depending on how you access
them. Figure 7 shows the traditional way Share permissions are identified, and Figure 8 shows the way Share permissions are assigned with Permission Levels.
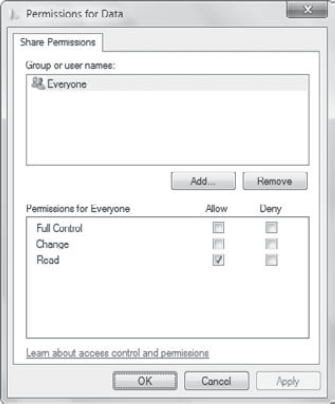
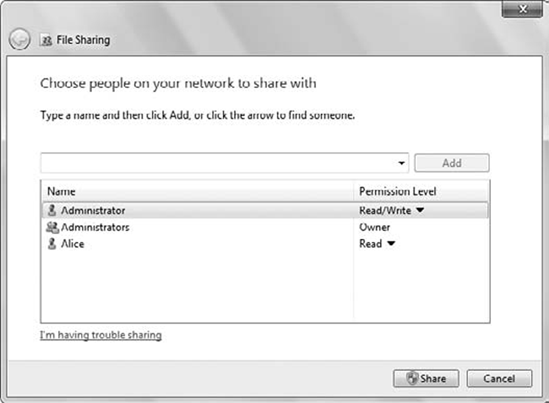
In Windows XP and older
operating systems, the Share permissions were listed as Read, Change, or
Full Control. In Windows 7, the interface guides you to assign
Permission Levels of Read, Read/Write, or Full Control. Table 1 shows the Share permissions and Permission Levels, including the level of access granted for each.
Table 1. Share Permissions and Permission Levels
| Share Permission | Permission Level | Access |
|---|
| Read | Read
Also known as Reader | Users can view the files and folders, view data within files, and run any executable files. |
| Change | Read/Write
Also known as Contributor | Users have Read permission and can also add files and subfolders, change data in files, and delete subfolders and files. |
| Full Control | Owner
Can also have co-owners | Users have all Read and Change permissions and can also change the permissions for any NTFS files and folders. |
|
In Windows Vista and
Windows Server 2008, the Permission Levels were known as Reader,
Contributor, Owner, and Co-owner roles. In Windows 7, these permissions
levels aren't assigned as roles but instead are assigned using the
permissions of Read, Read/Write, and Owner.
|
|
It's important to
realize that Share permissions apply to shared folders only when they
are accessed over the network. If the folder is accessed locally with
Windows Explorer, the Share permissions do not apply at all.
4. Combining NTFS and Share Permissions
When a share is accessed
over the network, the NTFS and Share permissions interact. This is a
common source of confusion for many administrators until they understand
exactly how the permissions interact.
As an example, if Sally tries to access a file named Project.docx
over the network but is denied access, she'll be asking for help. If
she requires access to this file, you'll need to determine what her
current permissions are and what needs to be changed to grant her
access. For our example, imagine that Sally is a member of the G_Sales
and G_Marketing groups and the following permissions are assigned:
NOTE
Groups are commonly
prefixed with letters to identify the scope of the group. For example, a
global group is often identified with a prefix of G_, and a domain
local group is often identified with a prefix of DL_.
The simplest way to determine the resulting permissions is by using a three-step process:
Determine
the effective NTFS permissions. NTFS permissions are cumulative, so the
effective NTFS permissions are determined by combining all of the
assigned NTFS permissions. Because Sally is in both the G_Sales and
G_Marketing groups, she is granted both Read and Modify.
Modify includes Read, so her cumulative NTFS permission is Modify.
Determine
the effective Share permissions. Share permissions are cumulative, so
the effective Share permissions are determined by combining all of the
assigned Share permissions. Because Sally is in both the G_Sales and
G_Marketing groups, she is granted both Read and Full Control.
Full Control includes Read, so her cumulative Share permission is Full Control.
Determine
the most restrictive permissions. The resulting permission is the most
restrictive permission (the permission that provides the least access)
between the effective NTFS and the effective Share permissions. The
effective NTFS permission is Modify, and the effective Share permission
is Full Control.
Modify is more restrictive than Full Control, so the resulting permission when the share is accessed over the network is Modify.
NOTE
The most common
reason why people become confused with this is that they try to do all
three steps at the same time. However, if you separate the process into
three distinct steps, you can reach the correct result without
confusion.
As another example, imagine
that Bob is a member of the G_Supply and G_Production groups, and the
following permissions are assigned to a folder named Data, which is also shared from a Windows 7 system:
Can you determine Bob's permissions when he accesses the share? Can you determine Bob's permissions when he accesses the Data folder on the Windows 7 system?
Determine
the effective NTFS permissions. Because Bob is in both the G_Supply and
G_Production groups, he is granted both Read and Full Control.
Full Control includes Read, so his cumulative NTFS permission is Full Control.
Determine
the effective Share permissions. Because Bob is in the G_Supply group
he is granted Read. He is not in the Administrators group, so he is not
granted the permissions from that group.
Bob has Read permission on the share.
Determine
the most restrictive permissions. The effective NTFS permission is Full
Control and the effective Share permission is Read.
Read is more restrictive than Full Control, so the resulting permission when the share is accessed over the network is Read.
However, if Bob accesses the
folder on the local Windows 7 system, share permissions will not apply;
only NTFS permissions will apply. Bob will have Full Control
permissions if he accesses the Data folder locally on the Windows 7 system.
Here's one more example.
Imagine that Alice is a member of the G_HR and G_Legal groups, and the
following permissions are assigned:
Determine the effective NTFS permissions.
Because Alice is in both the G_HR and G_Legal groups, she would be
granted both Full Control and Modify. However, Alice is specifically
denied Full Control, and because there's a conflict, Deny takes
precedence.
Alice's effective NTFS permission is Deny Full Control.
Determine the effective Share permissions. Because Alice is in the G_HR and G_Legal groups, she is granted Modify and Read.
Modify includes Read, so the effective Share permission is Modify.
Determine the most restrictive permissions. Deny Full Control is more restrictive than Modify, so the resulting permission for Alice is Deny Full Control.
5. Printer Permissions
Printer permissions apply when a printer is shared. There are three basic printer permissions and three special permissions. Figure 9 shows the basic permissions for a printer.
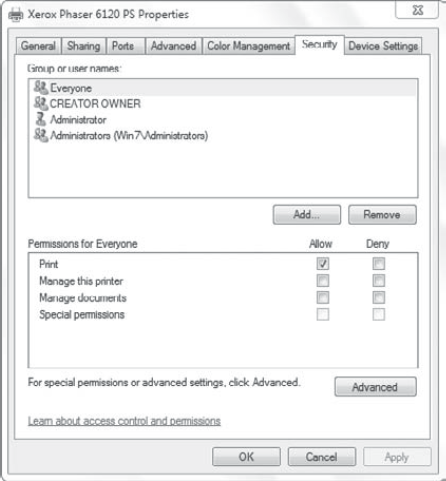
Print
Users granted this
permission can print to the printer. By default, the Everyone group is
granted Allow Print permissions when a printer is added.
- Manage Documents
Users with
Manage Documents permission can pause, cancel, and restart print jobs
for any user. In organizations where multiple users share a single
printer, a responsible user may be granted Manage Documents permission
so that they can pause, restart, and cancel print jobs that any user has
sent to the printer.
By default, the Creator Owner
group is granted Manage Documents permission. Any user who sends a print
job to a printer is identified as the Creator Owner for that print job,
allowing the user to manage the print job.
- Manage This Printer
Users with the Manage
This Printer permission can modify any of the properties for the printer
including ports used, drivers installed, and permissions assigned.
Users with this permission can also restart the Printer Spooler service,
which is sometimes useful when print jobs become hung up in the print
queue and can't be cancelled or deleted.
|
The Printer Spooler
service can be restarted from the Services applet available via the
Administrative Tools menu or from a command prompt with administrative
permissions with the following commands: SC Stop Spooler and SC Start
Spooler, or Net Stop Spooler and Net Start Spooler.
|
|
Figure 10 shows the three basic permissions and the three special permissions for a printer with the three basic permissions.
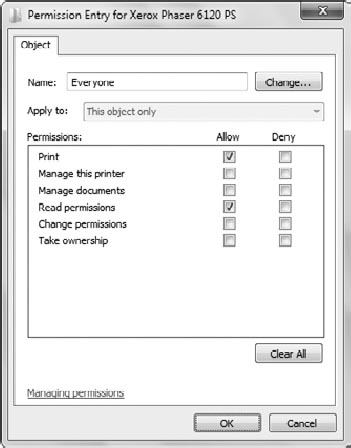
Read Permissions
Users granted this
permission can read the assigned permissions. The Everyone group is
granted Read Permissions when the printer is shared in addition to the
Print permission.
Change Permissions
Any user granted
Manage This Printer permission is also granted the Change Permissions
permission. This allows them to change permissions for other users. This
permission is automatically granted to the Administrators group.
Take Ownership
Any user granted
Manage This Printer is also granted the Take Ownership permission. This
permission allows a user to take ownership of a printer. As the owner,
the user is able to modify permissions. This permission is automatically
granted to the Administrators group.