When a system starts having problems, you want to
figure out the source of the problem as quickly as possible. One of the
ways to get a head start on that goal is to become familiar with the
tools you have available for troubleshooting.
1. Analyzing Logs with Event Viewer
One of the most important tools you always have available to you on Windows 7 is Event Viewer.
Events are constantly logged to various logs on Windows 7, and when you
know what logs to look at, you can quickly determine the problem.
Windows 7 is constantly
logging events on the health and performance of your system, and you can
easily query one of many logs to retrieve valuable information. The
primary logs you'll monitor when working with Windows 7 are these:
System
The System log
records Windows system component events. This includes components such
as drivers, services, and Windows-based processes.
Application
The Application log
contains events related to applications or programs. As an example,
antivirus application events are typically logged in the Application
log. Program developers have the choice of which log to use when
recording events, so it is possible for an application developer to log
an event in the System log instead.
Security
The Security log
records security-related events such as logon attempts and auditing.
When auditing is enabled, it can be used to record auditable events such
as anytime a user accesses a resource. Auditing can also record if
someone attempted to access a resource but failed because of not having
permissions.
Setup
The Setup log is used to record events related to application installations.
The Forwarded Events log is
used if an event subscription is created. A single computer can
subscribe to events that are forwarded from multiple other computers.
NOTE
Event Viewer looks the
same on Windows 7 as it does on Windows Vista, Windows Server 2008, and
Windows Server 2008 R2. Many of the available logs are much more
valuable on a server than they are on a desktop computer. Desktop
administrators often focus on only the Application and System logs for
troubleshooting and on the Security log when investigating security
events.
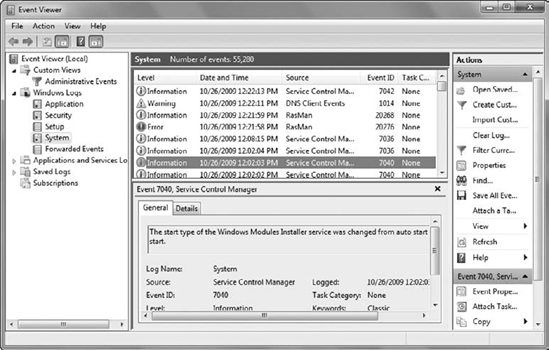
Figure 1
shows the Event Viewer in Windows 7. The Event Viewer is one of the
Administrative Tools and can be accessed by multiple methods. One way is
by clicking Start =>
Control Panel, typing Event Viewer in the Search box, and pressing
Enter. You can then select View Event Logs under Administrative Tools.
There are several items of
interest in the figure. The left pane shows the different logs that you
can select. Our focus in this article is on the Windows logs, especially
the System and Application logs. The System log is selected in the
figure. The top of the center pane includes summary information on the
events for the selected log. The event that is selected is displayed in
the bottom of the center pane.
Logs are displayed based on
the Date And Time value, with newest log entries showing first. However,
you can click any of the headings to sort the logs by a different
order. For example, you could click the Event ID header, and the logs
would be resorted based on the number of the Event ID.
Events are classified
based on a severity level. Four severity-level types can be logged in
the System, Application, and Setup logs:
 Information severity-level events
Information severity-level events
Information events are
logged when a change to an application or component has occurred. For
example, if a service is stopped or started, it will be logged here.
Information events have an icon of a blue i in a white circle.
 Warning severity-level events
Warning severity-level events
Warning events indicate
that something has occurred that may impact a service or result in a
more serious problem if the event is not addressed. Errors are usually
preceded by warnings.
Warning events have an icon of a black exclamation point (!) in a yellow triangle.
 Error severity-level events
Error severity-level events
An error event
indicates that a problem has occurred. Errors can impact the
functionality of the application or component that triggered the event.
For example, if a service tried to start but a condition prevented it
from starting, an error event would be logged.
Error events have an icon of a white exclamation point (!) in a red circle.
 Critical severity-level events
Critical severity-level events
Critical events indicate that a failure has occurred and the application or component that triggered the event cannot recover.
Critical events have an icon of a white X in a red circle.
You can double-click any event in the Event Viewer to see additional details on the event. Figure 2 shows the details of an event logged after Windows Explorer hung on a system, requiring it to be stopped via Task Manager.
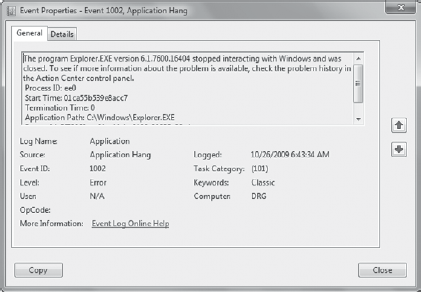
Events include details such as
what, when, and where and, in the case of security events, also identify
the user performing the event. If an error or a warning event occurs on
a regular basis, it indicates a problem that needs to be addressed. If
the event occurs only once, you may be able to ignore the event.
NOTE
An Application
Hang source indicates that the application would not respond and had to
be forcibly terminated using Task Manager.
The Details tab is more
useful to the developers of the application or component than to the
administrators. As an administrator, you'll find all the information you
need on the General tab. A valuable feature is the Copy button, which
allows you to copy the details of the event easily to the Clipboard so
that you can paste them into another document.
2. Using the Action Center
The Action Center
provides a central location to view alerts and take actions. Messages
in the Action Center provide insight into the system's security,
reliability, and stability. When the Action Center has issues that can
be resolved by taking specific actions, a little white flag appears in
the notification area of Windows 7.
NOTE
The notification area is on
the far right of the taskbar. It includes several notification icons
such as the Clock, Volume, Network, Power, and Action Center. Any of
these icons can be enabled or disabled by right-clicking the
notification area and selecting Properties.
Figure 3
shows the Action Center on a Windows 7 system. It includes several
issues that the Action Center suggests should be investigated.
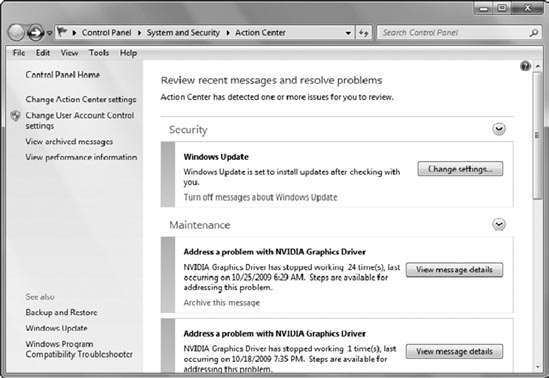
Not all Action Center
messages need action. As an example, the Security section is reminding
me that I have Windows Update set to download the updates automatically,
but I must choose when to install them. Since this is contrary to the
recommendations, it's included in the Action Center. It is possible to
turn off messages about Windows Update, but that will turn off all
messages about Windows Update, not only this notification.
On the other hand, it also shows
I have issues with an NVIDIA graphics driver that has stopped working
24 times. When I click View Message Details, it does an Internet query
and gives me a list of possible solutions, such as checking for driver
updates through the Microsoft Update site or other methods.
NOTE
The NVIDIA
driver occasionally fails when the system is waking up from hibernate,
forcing a reboot. The Action Center has detected the failure and
identified the problem as a driver issue. Unfortunately, there doesn't
seem to be a driver update for it just yet. Since Windows 7 has been
officially released for just a couple of days as I write this, I'm
willing to be patient.
The Action Center has two areas where different messages can be displayed: Security and Maintenance.
Security
The Security section provides security-related messages. It can provide
messages on network firewall, Windows Update, virus protection, spyware
and unwanted software protection, Internet security settings, User
Account Control, and Network Access Protection.
Maintenance The Maintenance section provides messages related to backups, checking for updates, and system maintenance settings.
2.1. Changing Action Center Settings
It's possible to turn
on or off various Action Center messages. If you click the Change Action
Center Settings link in the Action Center, a display similar to Figure 4 appears.
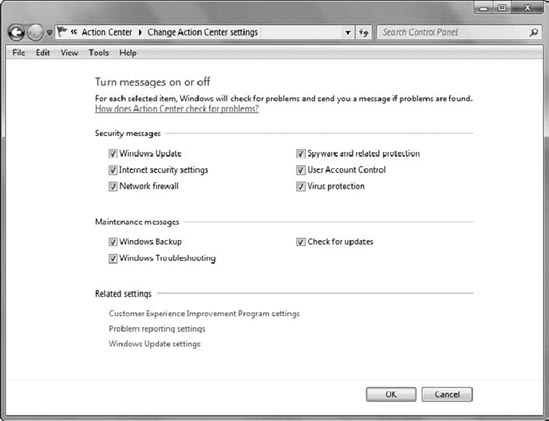
You can check or uncheck the
boxes to turn on or turn off messages for that category. For example, if
you wanted to keep your system configured to download updates
automatically but you choose when to install them, and you don't want to
be notified of your choice, uncheck the Windows Update selection.
2.1.1. Customer Experience Improvement Program Settings
This program collects
information about the computer hardware and how Windows is being used,
but it does not collect any information that can be used to identify or
contact the user personally. It also periodically downloads a file that
can be used to collect information about problems experienced on the
system.
By using this method,
Microsoft is able to identify how people are using Windows. This
information can then be used to identify ways Windows can be improved or
enhanced.
You have two choices when you click this link:
Yes, I Want To Participate In The Program
No, I Don't Want To Participate In The Program
2.1.2. Problem Reporting Settings
The Problem Reporting Settings are directly related to Windows Error Reporting (WER).
WER is used to report issues to Microsoft from individual computers.
When a problem event occurs, WER can be invoked to collect and report
information on the error.
WER is most commonly
invoked when an unresponsive application is terminated using Task
Manager. If authorized, information on the error is sent to Microsoft
servers that collect the data. Once Microsoft is aware of an error that
is causing problems for end users, they begin looking for a solution.
NOTE
WER is especially useful
for emerging threats. If thousands of computers start having the same
issue that WER reports, Microsoft is able to collect data quickly on the
issue and respond with a solution in a much more timely fashion.
The solution may require a
patch that is written and released as an update, or investigation may
show that the problem is due to a set of circumstances that the user can
control. Once a solution is identified, Microsoft's response to the WER
message indicates that a solution is available. In addition, if the
Action Center is configured to receive the solutions, the solutions will
appear in the Action Center, prompting the user take action.
Figure 5 shows the four choices for WER, with the recommended setting selected.
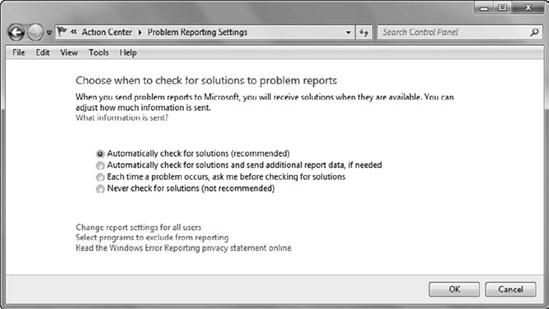
When WER is configured as
shown, problems are automatically reported to Microsoft. When solutions
are identified, they will appear in the Action Center.
2.2. Changing User Account Control Settings
User Account Control (UAC)
is used to prevent malicious software (malware) or other potentially
harmful programs from making unauthorized changes to your computer. The
challenge is determining the difference between an authorized change and
an unauthorized change.
If a user is using a system and
that system becomes infected with malware, the malware can assume the
permissions and rights of the user. If the user has sufficient rights to
make system-level changes, the malware has those same rights. With
elevated rights and permissions, the malware can quickly embed itself
deep into the system and start its mischief.
Windows Vista introduced UAC
to detect when changes were occurring to the system and to ask users if
they initiated the action. If the action was initiated by malware, it
could be stopped. However, one of the complaints about UAC with Windows
Vista is that users were prompted too frequently to confirm their
actions.
Windows 7 has improved UAC.
One significant change is that Windows 7 can differentiate between
changes made by a user and changes made by an application. By default,
UAC in Windows 7 notifies the user only when an application attempts to
make a change.
2.2.1. Balancing Security
When it comes to security,
it's often difficult to find the right balance that ensures an
acceptable level of security while also allowing an acceptable level of
usability to the end user. You probably know that the only way to ensure
a computer is 100 percent secure is never to take it out of the box. As
soon as you plug it in, you start accepting some risk.
On the other hand, a computer
without any security at all may be very easy to use but won't be secure.
What's important—usability or security? The answer is that both are
important, so when computers are deployed they are done so with a
balance of security and usability. However, that balance isn't the same
for everyone.
If a computer houses
highly classified data, security is much more important than usability.
On the other hand, a computer used by administrative staff for
day-to-day tasks doesn't need the same level of security.
2.2.2. Selecting the UAC Level
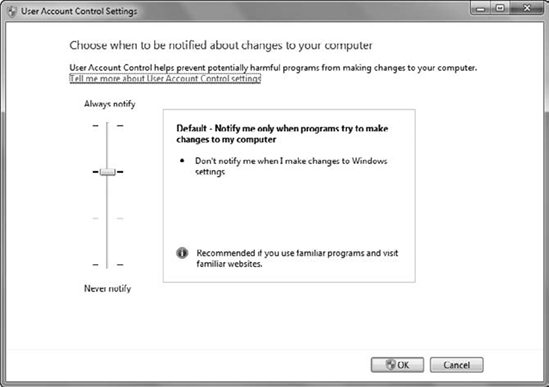
Figure 6
shows the User Account Control Settings page that can be accessed from
the Action Center with the default selected. There are four choices
available:
Always Notify
This is the most
secure setting. Any system-level change results in a UAC prompt. It
doesn't matter whether the change was initiated by the user or by a
program. This setting is recommended if a user routinely installs new
software or visits risky or unfamiliar websites. The desktop is switched
to a secure desktop mode (the user will see it dimmed) until the UAC
prompt is approved or denied.
|
Secure desktop mode is used to
prevent malware from mimicking the UAC prompt. When dimmed by UAC,
nothing else can be done until the UAC query is answered.
|
|
Notify Me Only When Programs Try To Make Changes To My Computer
This setting will notify the
user when a program attempts to make changes to a computer that
requires administrator permissions. When this occurs, the desktop will
be dimmed. Changes made by the user do not result in notification. This
is the default setting.
Notify Me Only When Programs Try To Make Changes To My Computer (Do Not Dim My Desktop)
This is the same as the
previous setting but does not use the secure desktop setting. Since the
desktop is not dimmed, malware may be able to spoof or otherwise
interfere with the appearance of the UAC dialog box.
Never Notify
This is the least-secure setting. Any changes made by the user or a computer will be allowed without any notification.