User Account Control (UAC)
provides an added layer of security to ensure that you are notified if
changes to your system are attempted. UAC is intertwined with much of
the underlying operations of Windows 7, but the core goal is to limit
the capabilities of malicious software.
When a regular user logs on, an access token is created that
includes the user's SID and the SIDs of any groups where the user is a
member.
In earlier Windows
systems, a significant risk was present if a user logged on with
administrative permissions. If a system was infected with malware while a
user was logged on with administrative permissions, the malware had
administrative permissions and was able to do significant damage.
Corporate
environments often implemented policies requiring administrators to use
two accounts. One account was for regular usage. If administrative
access was needed to perform tasks, only the administrative account was
used, but only for the time needed to perform the task.
In Windows XP and Windows
Server 2003, administrators were able to log on as a regular user and
then use the Run As feature to run individual applications with
administrative permissions. This reduced the risk of malware taking over
the administrative account.
Windows Vista introduced
UAC, and Windows 7 has improved on the functionality of UAC. The core
goal remains to protect the system from malware that tries to modify
settings. UAC requires any attempts to modify the system settings by an
application to be approved.
The default UAC setting in
Windows 7 separates the actions taken by the user from the actions taken
by applications. In other words, if a user makes the change, they
aren't prompted by UAC. If an application attempts to make a change, UAC
does prompt for approval. This prevents malware from making
unauthorized changes while reducing the number of UAC pop-ups when a
user is making changes.
NOTE
In Windows Vista, UAC
prompted the user every time an action needed administrative privileges.
This included every time an application tried to make a change and
every time the user tried to make a change. This resulted in a
significant number of UAC prompts and was one of the criticisms of
Windows Vista.
UAC works by implementing
something called Admin Approval Mode. Admin Approval Mode uses two
access tokens when a user logs on to Windows 7 with an administrative
account. One is for regular use, and the second is used only when
administrative permissions are needed.
Standard user access token
This is the token used
for most regular work, such as launching and using applications. This
token does not have any administrative privileges.
Administrator access token
If an
action requires administrative privileges, this token is used. UAC
usually prompts the user to use this access token before the token is
used.
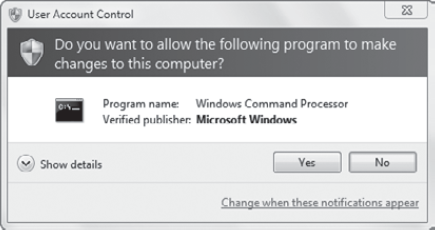
Figure 1
shows the UAC screen that appears when the administrator access token
is needed. The program name identifies the program that is requiring the
elevated permissions. In the figure, the command prompt is being
launched with administrative permissions.
|
Control Panel includes an icon
of a shield for any activity that requires UAC permissions. When you
click one of these links, the UAC prompt will appear unless the default
behavior has been modified.
|
|
A useful tool that shows you the different privileges that are available when the administrative token is used is the whoami command-line command. It can be used to get user name and group information along with assigned privileges or rights.
|
The whoami command
is also a quick way to determine the logon context of a user. When
entered without a switch, it identifies the user in the format of computer\username or domain\username.
|
|
As an example, if a regular user account is used, whoami will show that only the following privileges are assigned:
SeShutdownPrivilege shuts down the system.
SeChangeNotifyPrivilege bypasses traverse checking.
SeUndockPrivilege removes the computer from the docking station.
SeIncreaseWorkingSetPrivilege increases a process working set.
SeTimeZonePrivilege changes the time zone.
If the administrative account is used, there are over 20 privileges granted.
Exercise 1 shows how to use whoami
and, more specifically, allows you easily to see the difference in the
privileges assigned to the regular user and the administrator accounts.
Log on to Windows 7 with an account that has administrative permissions but is not the Administrator account. (If
you log on with the Administrator account, the command prompt will
always be launched with administrative privileges and you won't be able
to see the differences.) Launch a command prompt by clicking Start, typing cmd in the Start Search box, and pressing Enter. Enter the following command: Whoami /all
You can see details on the user account and group memberships. Notice that the BUILTIN\Administrators
account is included, but the attribute specifies that this account is
being used for Deny Only. In other words, rights and permissions are not
being granted for this group. View the list of privileges listed at the
end of the output. Leave this command-prompt window open. Launch a command prompt with elevated permissions. Click Start, type cmd in the Start Search box, right-click cmd, and select Run As Administrator. If prompted by UAC, click Yes. Enter the following command: Whoami /all
Compare this output to that generated by whoami
for the regular user account. The Administrator group isn't being
restricted to Deny Only, and the list of privileges is extensive.
|
1.1. UAC Settings
Although the default
setting for UAC provides good protection, you can modify the default
behavior. You can access the UAC settings screen by clicking Start,
entering UAC in the Start Search box, and pressing Enter. You can also
access it by clicking Start => Control Panel => System And Security => Action Center => Change User Account Control Settings.
Figure 2 shows the User Account Control Settings screen with the default settings selected.
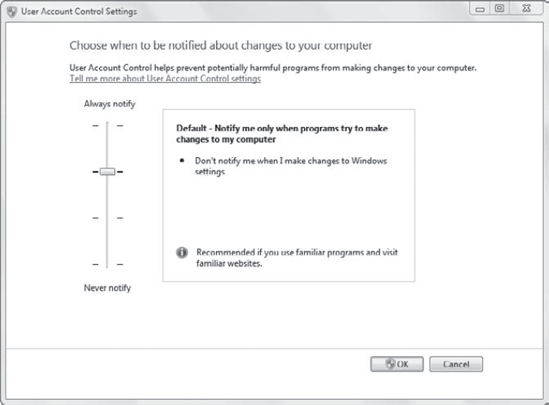
Always Notify
This is the way that UAC
works in Windows Vista. UAC will notify you anytime you make changes to
a Windows setting or a program tries to install software or make
changes. This level of notification was annoying to many Windows Vista
users and was one of the more common complaints. However, for users who
routinely install new software and visit unfamiliar websites, it is
recommended.
Default – Notify Me Only
When Programs Try To Make
Changes To My Computer This setting will still notify you if an
application makes changes to your system, but it doesn't notify you when
you make changes to Windows settings. This is recommended if you use
familiar programs and visit familiar websites.
Notify Me Only When Programs Try To Make Changes To My Computer (Do Not Dim My Desktop)
This setting is similar to
the default setting, but it does add some risk. Normally the desktop is
dimmed, preventing any action other than addressing the prompt. This
setting doesn't dim the desktop. It may allow malware to interfere or
dismiss the UAC prompt. This is not recommended.
Never Notify
This setting disables UAC.
It is not recommended and is only included for programs that must run in
Windows 7 but do not support User Account Control.
NOTE
The dimmed desktop is
also referred to as the secure desktop. When the desktop is dimmed, UAC
doesn't allow any other actions except for a response to the UAC.
1.2. Configuring UAC via Group Policy
Group Policy includes several
settings that you can use to modify the default behavior of UAC. The
primary settings you'll modify are located in the Computer Configuration => Policies => Windows Settings => Security Settings => Local Policies => Security Options node.
NOTE
These settings can also be found in the Local Computer Policy in the Computer Configuration => Windows Settings => Security Settings => Local Policies => Security Options node.
The following list explains some of these Group Policy settings:
User Account Control: Run All Administrators In Admin Approval Mode
This setting turns on
Admin Approval Mode for all administrators including the Built-in
Administrator account. When this setting is disabled, all UAC policy
settings are disabled for administrators.
User Account Control: Admin Approval Mode For The Built-in Administrator Account
This setting affects
only users logged on using the built-in Administrator account, not users
in the Administrators group. When it is enabled, users who log in using
the Administrator account will be prompted by UAC. This setting is
disabled by default, meaning that anyone logged in with the local
Administrator account will not be prompted by UAC. The administrator
access token will be used by default whenever it is needed.
User Account Control: Behavior Of The Elevation For Administrators In Admin Approval Mode
This setting affects any
user in the local Administrators group when Admin Approval Mode is
enabled. When enabled it has several possible settings:
Elevate Without Prompting
Prompt For Credentials On The Secure Desktop
Prompt For Consent On The Secure Desktop
Prompt For Credentials
Prompt For Consent
Prompt For Consent For Non-Windows Binaries (Default)
User Account Control: Behavior Of The Elevation Prompt For Standard Users
If users are logged
on with standard user accounts (non-administrator accounts), you can use
this setting to control what happens if they try to do something that
requires elevated permissions. The three choices are as follows:
User Account Control: Switch To The Secure Desktop When Prompting For Elevation
If enabled, this
setting overrides other settings and ensures that all UAC requests dim
the desktop for administrators and standard users.
User Account Control: Detect Application Installations And Prompt For Elevation
This setting is
disabled by default for computers joined to a domain. When disabled, it
allows applications to be deployed via Group Policy or advanced tools
such as Systems Management Server (SMS) or Systems Center Configuration
Manager (SCCM).
User Account Control: Only Elevate Executables That Are Signed And Validated
When this setting is
enabled, only files that are signed with a certificate and can be
verified via a certification authority are permitted to run. This
setting is disabled by default.
User Account Control: Virtualize File And Registry Write Failures To Per-User Locations
This setting allows some
legacy applications still to operate in Windows 7. UAC prevents
applications from writing data to protected locations and the
application fails. However, enabling this setting allows the write
failures to be redirected to user locations when the application runs.
The application can still operate, but the data is stored in the user
profile instead of modifying the system.