Most Exchange information is stored in Active
Directory. You can use the features of Active Directory to manage these
standard permissions across the Exchange organization.
1. Assigning Exchange Server Permissions to Users, Contacts, and Groups
Users, contacts, and
groups are represented in Active Directory as objects. These objects
have many attributes that determine how they are used. The most
important attributes are the permissions assigned to the object. Permissions
grant or deny access to objects and resources. For example, you can
grant a user the right to create public folders but deny that same user
the right to view the status of the information store.
Permissions
assigned to an object can be applied directly to the object, or they
can be inherited from another object. Generally, objects inherit permissions from parent objects.
A parent object is an object that is above another object in the object
hierarchy. However, you can override inheritance. One way to do this is
to assign permissions directly to an object. Another way is to specify that an object shouldn't inherit permissions.
In Exchange Server 2010, permissions are inherited through the organizational hierarchy. The root of the hierarchy is the Organization node.
All other nodes in the tree inherit the Exchange permissions of this
node. For example, the permissions on the Recipient Configuration node
are inherited from the Organization node.
For the management of Exchange information and servers, Exchange Server 2010 uses several predefined groups. These predefined
security groups have permissions to manage Exchange organization,
Exchange server, and Exchange recipient data in Active Directory. In
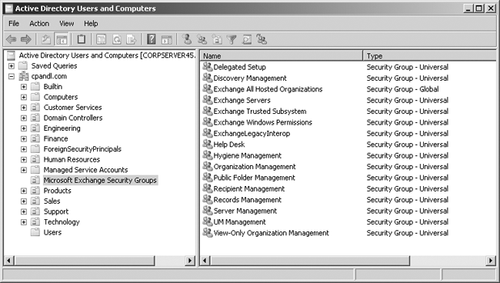
Active Directory Users And Computers, you can view and work with the
Exchange-related groups using the Microsoft Exchange Security Groups node. (See Figure 1.)
Tip:
In Active Directory Users
And Computers, there's a hidden container of Exchange objects called
Microsoft Exchange System Objects. You can display this container by
selecting Advanced Features on the View menu.
2. Understanding the Exchange Management Groups
Table 8-1 lists predefined
groups created in Active Directory for Exchange Server 2010. As the
table shows, each group has a slightly different usage and purpose.
Several of the groups are used by Exchange servers. These groups are
Exchange Servers, Exchange Trusted Subsystem, Exchange Windows Permissions, and ExchangeLegacyInterop. As indicated in the table, you use the other groups for role-based access control and assigning management permissions.
Note:
Exchange 2003 and Exchange 2007 use a different set of security groups for managing Exchange permissions. If you want a user or group that had permissions
in Exchange 2003 or Exchange 2007 to have permission in Exchange 2010,
you need to configure the appropriate Exchange 2010 permissions for that user or group.
Table 1. Security Groups Created for Exchange
| GROUP | GROUP TYPE | DESCRIPTION | ROLE GROUP |
|---|
| Delegated Setup | Universal Security Group | Members of this group have permission to install and uninstall Exchange on provisioned servers. | Yes |
| Discovery Management | Universal Security Group | Members of this group can perform mailbox searches for data that meets specific criteria. | Yes |
| Exchange All Hosted Organizations | Global Security Group | Members
of this group include hosted organization mailbox groups. This group is
used to apply Password Setting objects to all hosted mailboxes. | No |
| Exchange Install Domain Servers | Global Security Group | Members
of this group include domain controllers on which Exchange Server is
installed. You can see this group only when you select View and then
click Advanced Features in Active Directory Users And Computers. | No |
| Exchange Servers | Universal Security Group | Members
of this group are Exchange servers in the organization. This group
allows Exchange servers to work together. By default, all computers
running Exchange Server 2010 are members of this group; you should not
change this setup. | No |
| Exchange Trusted Subsystem | Universal Security Group | Members of this group are Exchange servers that run Exchange cmdlets using Windows Remote Management
(WinRM). Members of this group have permission to read and modify all
Exchange configuration settings as well as user accounts and groups. | No |
| Exchange Windows Permissions | Universal Security Group | Members
of this group are Exchange servers that run Exchange cmdlets using
WinRM. Members of this group have permission to read and modify user
accounts and groups. | No |
| ExchangeLegacyInterop | Universal Security Group | Members of this group are granted send-to and receive-from permissions,
which are necessary for routing group connections between Exchange
Server 2010 and Exchange Server 2003. Exchange Server 2003 bridgehead
servers must be made members of this group to allow proper mail flow in
the organization.
| No |
| Help Desk | Universal Security Group | Members of this group can view any property or object within the Exchange organization and have limited management permissions. | Yes |
| Hygiene Management | Universal Security Group | Members of this group can manage the antispam and antivirus features of Exchange. | Yes |
| Organization Management | Universal Security Group | Members of this group have full access to all Exchange properties and objects in the Exchange organization. | Yes |
| Public Folder Management | Universal Security Group | Members of this group can manage public folders and perform most public folder management operations. | Yes |
| Recipient Management | Universal Security Group | Members
of this group have permissions to modify Exchange user attributes in
Active Directory and perform most mailbox operations. | Yes |
| Records Management | Universal Security Group | Members
of this group can manage compliance features, including retention
policies, message classifications, and transport rules. | Yes |
| Server Management | Universal Security Group | Members
of this group can manage all Exchange servers in the organization but
do not have permission to perform global operations. | Yes |
| UM Management | Universal Security Group | Members
of this group can manage all aspects of unified messaging (UM),
including Unified Messaging server configuration and UM recipient
configuration. | Yes |
| View-Only Organization Management | Universal Security Group | Members of this group have read-only access to the entire Exchange
organization tree in the Active Directory configuration container and
read-only access to all the Windows domain containers that have Exchange recipients. | Yes |
When working with Exchange-related groups, be sure to keep in mind that Organization Management grants the widest set of Exchange management permissions possible. Members of this group can perform any Exchange
management task, including organization, server, and recipient
management. Members of the Recipient Management group, on the other
hand, can manage only recipient information, and Public Folder
Management can manage only public folder information. View-Only
Organization Management can view Exchange organization, server, and
recipient information, but this group cannot manage any aspects of
Exchange.
Table 2 provides an overview of the default
group membership for the Exchange groups. Membership in a particular
group grants the member the permissions of the group. Exchange groups
that aren't listed don't have any default members or membership.
Table 2. Default Membership for Exchange Security Groups
| GROUP | MEMBERS | MEMBER OF |
|---|
| Exchange Install Domain Servers | Individual Exchange servers | Exchange Servers |
| Exchange Servers | Exchange Install Domain Servers, individual Exchange servers | Windows Authorization Access Group |
| Exchange Trusted Subsystem | Individual Exchange servers | Exchange Windows Permissions |
| Exchange Windows Permissions | Exchange Trusted Subsystem | n/a |
8.1.3. Assigning Standard Exchange Management Permissions
To grant Exchange management
permissions to a user or group of users, all you need to do is make the
user or group a member of the appropriate Exchange management group. The
tool of choice for managing users in a domain is Active Directory Users
And Computers. You can make users, contacts, computers, or other groups members of an Exchange management group by completing the following steps:
Click Start, point to All Programs, select Administrative Tools, and select Active Directory Users And Computers.
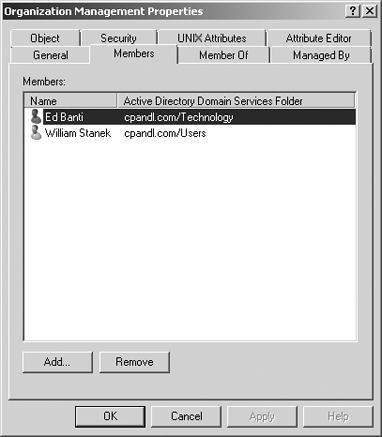
In
Active Directory Users And Computers, double-click the Exchange
management group you want to work with. This opens the group's
Properties dialog box.
Click the Members tab, as shown in Figure 2.
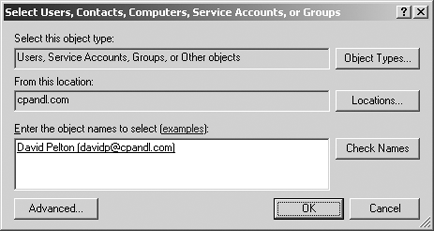
To
make a user or group a member of the selected group, click Add. The
Select Users, Contacts, Computers, Service Accounts, Or Groups dialog
box appears, as shown in Figure 3.
Type the name of the account to which you want to grant permissions,
and then click Check Names. If matches are found, select the account
you want to use and then click OK. If no matches are found, update the
name you entered, and try searching again. Repeat this step as
necessary. Click OK.
You can remove a user,
contact, computer, service account, or other group from an Exchange
management group by completing the following steps:
Open Active Directory Users And Computers.
In
Active Directory Users And Computers, double-click the Exchange
management group with which you want to work. This opens the group's
Properties dialog box.
On
the Members tab, click the user or group you want to remove and then
click Remove. When prompted to confirm, click Yes, and then click OK.
You can use the Exchange Control Panel (ECP) to manage membership in role groups. By default, the Exchange Control Panel URL is https://yourserver.yourdomain.com/ecp.
When you are managing the organization and Users & Groups is
selected in the left pane, you can select the Administrator Roles tab to
work with Exchange role groups. When you select a role, the right-most
pane provides a description of the role, lists the assigned roles, and
also shows the current members. While working with this view, you can
double-click a group entry to view and manage its membership.