5. Protecting Your AD CS Configuration
Along with the security measures you must perform for your root
and intermediate CAs, you must also protect each CA, especially
issuing CAs through regular backups. Backing up a CA is very simple.
In Server Manager, expand Roles\Active Directory Certificate Services\CA Server
Name. Right-click the server name, point to All Tasks, and
click Back Up CA. When you launch the backup operation, it launches
the Certification Authority Backup Wizard. To back up the
CA, use the following operations:
Launch the Certification Authority Backup Wizard and click
Next. On the Items To Back Up page, select the items you want to
back up. The Private Key And CA Certificate option protects the
certificate for this server. The Certificate Database And Certificate Database Log
option protects the certificates that this CA manages. You can
also perform incremental database backups.
Identify the location to back up to. For example, you could create the backup to a file share on
a central server location. Remember, however, that you are backing
up highly sensitive data and transporting it over the network,
which might not be the best solution. A better choice might be to
back up to a local folder and then copy the backup to removable
media. Identify the location and click Next. Note that the target
location must be empty. Assign a strong password to the backup. Click Next. Review the information and click Finish. The wizard performs the backup. Protect the backup media
thoroughly because it contains very sensitive information.
You can also perform automated backups through the command line
with the Certutil.exe command with the appropriate switches to back up
and restore the database.
To restore information, use the Certification Authority Restore
Wizard. When you request a restore operation by right-clicking the
server name, pointing to All Tasks, and clicking Restore CA, the
wizard immediately prompts you to stop the CA service before the
restore operation can begin. Click OK. After the service is stopped,
the Welcome page of the wizard appears.
Select the items you want to restore. You can restore the
private key and the CA certificate as well as the database and
log. Type the location of the backup files or click Browse to
locate the backup data. Click Next. Type the password to open the backup and click Next. Verify your settings and click Finish. After the restore operation is complete, the wizard offers
to restart the AD CS service. Click Yes. Verify the operation of your CA after the restore
is complete.
5.1. Practice Configuring and Using AD CS
5.1.1. Practice Configuring and Using AD CS
In this practice, you perform five key tasks. In the first,
you finalize the configuration of an Online Responder. In the
second, you work with Enterprise PKI to correct the errors in an
AD CS implementation. Then you create a custom certificate
template to publish certificates. You also enable autoenrollment
for certificates to ensure that your users can obtain them
automatically. Finally, you ensure that your issuing CA will
automatically enroll clients.
EXERCISE 1 Finalizing the
Configuration of an Online Responder
As mentioned earlier, to finalize the configuration of an
online responder, you must configure and install an OCSP Response
Signing certificate and configure an Authority Information Access
(AIA) extension to support it. Use the following procedure:
Log on to SERVER04 using the domain administrator
account. In Server Manager, expand Roles\Active Directory
Certificate Services and select Certificate Templates. When
you click it, the node displays the server name in
parentheses, in this case SERVER01.contoso.com. Right-click the OCSP Response Signing template and click
Duplicate Template. Select Windows Server 2008 Enterprise and
click OK. Type a valid name for the new template, such as OCSP Response Signing WS08. Select the Publish Certificate In Active Directory check
box. On the Security tab, under Group Or User Names, click
Add, click Object Types to enable the Computer object type,
and click OK. Type SERVER04, and then
click Check Names. Click OK. Under Group Or User Names, click the computer name you
just added, and then, in the Permissions section of the dialog
box, select the Read, Enroll, and Autoenroll permissions in
the Allow column. Click OK to create the duplicate template.
Your certificate template is ready. Now you must configure
the AIA extension to support the OR. Continue with these
steps:
Launch Server Manager from the Administrative Tools
program group. Expand Roles\Active Directory Certificate
Services\Contoso-Issuing-CA01. Right-click Contoso-Issuing-CA01 in the tree pane and
click Properties. On the Extensions tab, click the Select Extension
drop-down list and choose Authority Information Access
(AIA). Specify the locations to obtain certificate revocation
data. In this case, select the location beginning with
http://. Select the Include In The AIA Extension Of Issued
Certificates and the Include In The Online Certificate Status
Protocol (OCSP) Extension check boxes. Click OK to apply the changes. Note that you must stop and restart the AD CS service because of the change. Click Yes
in the Certification Authority dialog box to do so. Move to the Certificate Templates node under
Contoso-Issuing-CA01 in the tree pane, right-click Certificate
Templates, point to New, and then click Certificate Template
To Issue. In the Enable Certificate Templates dialog box, select
the new OCSP Response Signing template that you created
earlier and click OK. The new template should appear in the details
pane. You now need to verify that the OCSP certificate has
been assigned to the server. You do so with the Certificates
snap-in. By default, this snap-in is not in a console. You
must create a new console to use it. Open the Start menu, type mmc in the search box, and then press
Enter. In the MMC, click Add/Remove Snap-in on the File menu to
open the Add Or Remove Snap-ins dialog box. Select the Certificates snap-in and click Add. Select Computer Account and click Next. Select Local Computer and click Finish. Click OK to close the Add Or Remove Snap-ins dialog
box. On the File menu, click Save to save the console and
place it in your Documents folder. Name the console Computer Certificates and click
Save. Expand Certificates\Personal and select
Certificates. Right-click Certificates under Personal, point to All
Tasks, and then click Request New Certificate. Click
Next. On the Certificate Enrollment page, make sure the Active
Directory Enrollment Policy is selected and click Next. Select the new OCSP certificate and click Enroll. On the next page, click the down arrow to the right of
Details, and then click View Certificate. Browse through the
tabs to view the certificate details, noting the certificate
name. Click OK. Click Finish to complete this part of the
operation. Right-click the new certificate, point to All Tasks, and
then click Manage Private Keys. On the Security tab, under Group Or User Names, click
Add. In the Select Users, Computers, Service Accounts, Or
Groups dialog box, click Locations, select SERVER04, and click
OK. Type Network Service and
click Check Names. Click OK. Click Network Service, and then, in the Permissions
section of the dialog box, make sure the Allow::Full Control
permission is selected. Click OK to close the dialog
box.
Your OR is ready to provide certificate validation
information. Now that it is ready, add a revocation configuration.
Perform the following steps:
Launch Server Manager from the Administrative Tools
program group. Expand Roles\Active Directory Certificate
Services\Online Responder and select Revocation
Configuration. Right-click Revocation Configuration and click Add
Revocation Configuration. On the Welcome page, click Next. On the Name The Revocation Configuration page, type
RCSERVER04. On the Select CA Certificate Location page, identify the
location from which the certificate can be loaded. You can
choose from Active Directory, a local certificate store, or a
file. Choose Select A Certificate For An Existing Enterprise
CA and click Next. Because your root CA is offline, choose Browse CA
Certificates Published In Active Directory and click
Browse. Locate the root certification authority
(Contoso-Root-CA) and click OK. After the certificate is selected, the wizard loads the
Online Responder signing templates. Click Next. On the Select Signing Certificate page, you must select
a signing method because the OR signs each response to clients
before it sends it. Three choices are available: Automatic selection loads a certificate from the
OCSP template you created earlier. Manually, you can choose the certificate to
use. CA Certificate uses the certificate from the CA
itself.
Choose Automatically Select A Signing Certificate and
select Auto-Enroll For An OCSP Signing Certificate. Click Browse to browse for a CA and select
Contoso-Issuing-CA01. Click OK. This should automatically select the certificate
template you prepared earlier. Click Next. The wizard initializes the revocation provider. If for
some reason it cannot find it—it is not displayed in the
dialog box—you must add the provider manually, as described in
steps 14 and 15; otherwise, skip to step 16. For the purposes
of this exercise, perform steps 14 through 16. Click Provider, and then click Add under Base CRLs. Use
the following HTTP address: http://localhost/ca.crl. Click
OK. Repeat the preceding step for the Delta CRLs and use the
same HTTP address. Note, because you are obtaining the
certificate from Active Directory, the listed provider is an
address in ldap:// format and should be provided automatically
by the wizard. AD CS relies on Lightweight Directory Access
Protocol (LDAP) to obtain information from the AD DS directory
store. In production, however, you might need to add a second
source such as from an HTTP address. Click OK. Click Finish to complete the revocation
configuration.
You should now have a new revocation configuration listed in
the details pane, however it will not be working because of the
HTTP addresses you added in step 14 and 15, which you will correct
in the next exercise.
In production you would repeat this procedure for each CA
that is an OR.
EXERCISE 2 Correct an AD CS
Implementation with Enterprise PKI
In this exercise, you rely on Enterprise PKI to identify and
then correct configuration issues with your AD CS implementation.
This exercise demonstrates the value of working with Enterprise
PKI.
Make sure that SERVER01, SERVER03, and SERVER04 are
running. Log on to SERVER04, using the domain Administrator account. Launch Server Manager from the Administrative Tools
program group. Expand Roles\Active Directory Certificate Services and
select Enterprise PKI. Expand Enterprise PKI\Contoso-Root-CA.
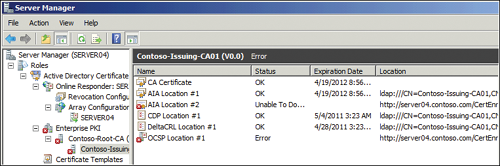
Click Contoso-Issuing-CA01 and note the errors. (See Figure 3.) These
errors exist if you added HTTP locations in the preceding
exercise. If you did not, your configuration will not include
any errors. These errors refer to the web-based download locations
for the CRL Distribution Point and for the AIA. These errors
appear because they refer to locations that do not exist.
These locations must be created manually in IIS. However,
because you are using an AD DS–integrated AD CS deployment,
you do not need to add web-based download locations even if
they are indicated by default in the configuration of AD CS.
In an AD DS–integrated deployment, the directory service is
responsible for AIA and CRL distribution, and, because this
service is highly available, no secondary location is
required. In fact, you need to add secondary locations only if
you want to make them available to mobile or external users
who are outside your internal network. If you do so, the URLs
you specify must be available externally.
Right-click Contoso-Issuing-CA01 under AD CS in Server Manager and click
Properties. On the Extensions tab, verify that CRL Distribution
Point (CDP) is selected in the drop-down list. Select
http://<ServerDNSName>/CertEnroll/<CaName><CRLNameSuffix><DeltaCRLAllowed>.crl
in the Locations section of the dialog box, and make sure that
Include In CRLs, Clients Use This To Find Delta CRL Locations,
as well as Include In The CDP Extension Of Issued Certificates
are cleared. (They may already be cleared.) Select Authority Information Access (AIA) from the
drop-down list. Select
http://<ServerDNSName>/CertEnroll/<ServerDNSName>_<CaName><CertificateName>.crt
and clear Include In The AIA Extension Of Issued Certificates
as well as Include In The Online Certificate Status Protocol
(OCSP) Extension. Click OK to apply your changes. AD CS automatically points to a CertEnroll virtual
directory under the default website as the CDP. However, the
installation process for AD CS does not create this virtual
directory by default. If you need to provide web support for
CRLs, even if this is only an internal deployment, you must
create the virtual directory in IIS. However, in this case, it
is not required. Also, as a best practice, you do not remove the HTTP location.
If you need to add it later, the proper format for the URL
will already be there, and you need only to reselect the
appropriate options. Because you modified the configuration of the AD CS
server, the console asks you to restart AD CS on this server.
Click Yes. Return to Enterprise PKI in Server Manager. On the toolbar, click the Refresh button to update
Enterprise PKI. There should no longer be any errors in the Enterprise
PKI view.
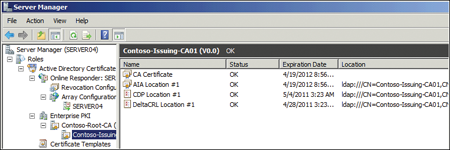
You must verify Enterprise PKI in your production network to
make sure no errors are displayed. Use this procedure to correct
them if errors are present.
EXERCISE 3 Create a Duplicate
Certificate Template for EFS
In this exercise, you create a duplicate certificate to
enable EFS and publish it so it can use autoenroll and use EFS to
protect the system data.
Make sure SERVER01 and SERVER04 are both running. Log on to SERVER04, using the domain Administrator account. Launch Server Manager from the Administrative Tools
program group. Expand Roles\Active Directory Certificate Services.
Click Certificate Templates
(servername). Note that all the existing templates are listed in the
details pane. Also note that you are connected to a DC (SERVER01) by
default. To work with templates, you must be connected to a DC
so that the templates can be published to AD DS. If you are not connected, you must click
the More Actions\Connect To Another Writable Domain Controller
link in the action pane to do so. Select the Basic EFS template in the details pane,
right-click it, and click Duplicate Template. Select the version of Windows Server to support—in this
case, Windows Server 2008—and click OK. Name the template Basic EFS
WS08 and set the following options. Leave all other
options as is. On the Request Handling tab, select the Archive
Subject’s Encryption Private Key and Use Advanced
Symmetric Algorithm To Send The Key To The CA check boxes.
Archival storage of the private key allows you to protect
it if the user loses it. On the Subject Name tab, add information to the
Alternate Subject Name values. Select the E-mail Name and
User Principal Name (UPN) check boxes.
Right-click the EFS Recovery Agent template and click
Duplicate. Select the version of Windows Server to support—in this
case, Windows Server 2008—and click OK. Name the template EFS Recovery
Agent WS08 and set the following options. Leave all
other options as is. On the General tab, select the Publish Certificate
In Active Directory check box. Note that the recovery
agent certificate is valid for a much longer period than
the EFS certificate itself. On the Request Handling tab, make sure you select
the Archive Subject’s Encryption Private Key and Use
Advanced Symmetric Algorithm To Send The Key To The CA
check boxes. Archival storage of the private key allows
you to protect it if the user loses it. On the Subject Name tab, add information to the
Alternate Subject Name values. Select the E-mail Name and
User Principal Name (UPN) check boxes.
In Server Manager, expand Roles\Active Directory
Certificate Services\Issuing CA Name and
select Certificate Templates. To issue a template, right-click Certificate Templates,
point to New, and then click Certificate Template To
Issue. In the Enable Certificate Templates dialog box, hold
down the Ctrl key and click to select both Basic EFS WS08 and
EFS Recovery Agent WS08. Click OK. Your templates are ready.
EXERCISE 4 Configure
Autoenrollment
In this exercise, you use Group Policy to configure
autoenrollment. This exercise uses the Default Domain policy for
simplicity, but in your environment, you should create a custom
policy for this purpose and for all other custom settings you need
to apply at the entire domain level.
Move to SERVER01 and log on as a domain
administrator. Launch Group Policy Management from the Administrative
Tools program group. Expand all the nodes to locate the Default Domain
Policy. Right-click it and click Edit. To assign autoenrollment for computers, expand Computer
Configuration\Policies\Windows Settings\Security Settings and
select Public Key Policies. Double-click Certificate Services Client –
Auto-Enrollment. Enable the policy and select the Renew Expired
Certificates, Update Pending Certificates, And Remove Revoked
Certificates check box. Click OK to assign these settings. Close the
GPMC. Your policy is ready.
EXERCISE 5 Enable the CA to Issue
Certificates
Now you need to set the default action that the CA performs
when it receives certificate requests.
Return to SERVER04 and log on, using the domain Administrator account. Right-click the issuing CA server name under AD CS, Contoso-Issuing-CA01, and click
Properties. On the Policy Module tab, click Properties. To have certificates issued automatically, verify that
Follow The Settings In The Certificate Template, If
Applicable. Otherwise, Automatically Issue The Certificate is
selected. Click OK. Click OK again to close the Properties
dialog box. Your issuing CA is now ready for production and will
begin to issue EFS certificates automatically when they are
requested either by your users or by computers.
|