1. Finalizing the Configuration of an Issuing CA
Finalizing the configuration of an issuing CA includes the
following actions:
Creating a certificate revocation configuration Configuring and personalizing certificate templates with
specific attention to the following factors: If you want to use the EFS to protect data, you must
configure certificates for use with EFS. This also involves
planning for the recovery agent or the agent that will be able
to recover data if a user’s EFS key is lost. If you want to protect your wireless networks with
certificates, you must configure wireless network
certificates. This enforces strong authentication and encrypts
all communication between wireless devices. If you want to use smart cards to support two-factor
authentication, you must configure smart card
certificates. If you want to protect websites and enable e-commerce,
you must configure web server certificates. You can also use
this certificate type to protect DCs and encrypt all
communication to and from them.
Configuring enrollment and issuance options
You perform each of these actions on the issuing CA itself or remotely through a workstation,
using the Remote Server Administration Tools (RSAT).
1.1. Creating a Revocation Configuration for a CA
Revocation is one of the only methods available to you for
controlling certificates when they are misused or when you need to
cancel deployed certificates. This is one reason your revocation
configuration should be completed before you begin to issue
certificates.
To create a revocation configuration, perform the following
actions:
Specify Certificate Revocation List (CRL) distribution
points. Configure CRL and Delta CRL overlap periods. Schedule the publication of CRLs.
Begin with the CRL distribution point. Revocation
configurations are performed in the Certification Authority
console.
Log on to an issuing CA with a domain account that has local
administrative rights. Launch the Certification Authority console from the
Administrative Tools program group. Right-click the issuing CA name and click
Properties. In the Properties dialog box, click the Extensions tab and
verify that the Select Extension drop-down list is set to CRL
Distribution Point (CDP). Also make sure that the Publish CRLs
To This Location and the Publish Delta CRLs To This Location
check boxes are selected. Click OK. If you made any changes to the CA’s configuration, you are
prompted to stop and restart the AD CS service. Click Yes to do
so.
Now configure CRL and Delta CRL overlap periods, using the
Certutil.exe command.
On the issuing CA, open an elevated command prompt and
execute the following commands: certutil -setreg ca\CRLOverlapUnits value
certutil -setreg ca\CRLOverlapPeriod units
certutil -setreg ca\CRLDeltaOverlapUnits value
certutil -setreg ca\CRLDeltaOverlapPeriod units
Value is the value you want to use to
set the overlap period, and units is
minutes, hours, or days. For example, you could set the CRL
overlap period to 24 hours and the Delta CRL publication period
to 12 hours. For this, you would use the following
commands: certutil -setreg ca\CRLOverlapUnits 24
certutil -setreg ca\CRLOverlapPeriod hours
certutil -setreg ca\CRLDeltaOverlapUnits 12
certutil -setreg ca\CRLDeltaOverlapPeriod hours
Go to the Certification Authority console and right-click
the issuing CA server name to stop and restart the
service.
Finally, configure the publication of the CRLs.
In the Certification Authority console, expand the console
tree below the issuing CA server name. Right-click Revoked Certificates and click
Properties. On the CRL Publishing Parameters tab, configure the CRL
and Delta CRL publication periods. By default, both values are set to one week and one day,
respectively. If you expect to have a high throughput of
certificates and need to ensure high availability of the CRLs,
decrease both values. If not, keep the default values. You can also view existing CRLs on the View CRLs
tab.
Your revocation configuration is complete.
1.2. Configuring and Personalizing Certificate Templates
Certificate templates are used to generate the
certificates you use in your AD CS configuration. Enterprise CAs use
version 2 and 3 templates. You can configure and personalize these
templates. To prepare templates for various uses, you must first
configure each template you intend to use and, after each is
configured, deploy each to your CAs. After templates are deployed,
you can use them to issue certificates. Begin by identifying which
templates you want to use, and then move on to the following
procedure.
Log on to an issuing CA, using domain administrative
credentials. Launch Server Manager from the Administrative Tools
program group. Expand Roles\Active Directory Certificate Services and select
Certificate Templates (servername). Note that all the existing templates are listed in the
details pane.
Warning:
IMPORTANT
UPGRADING CERTIFICATE AUTHORITIES
If you are upgrading an existing CA infrastructure to
Windows Server 2008 R2, the first time you log on to a new
server running AD CS, you are prompted to update the existing
certificate templates. Answer Yes. This upgrades all templates
to Windows Server 2008 R2 versions.
Note that you are connected to a DC by default. To work with templates, you must be connected to a DC so that
the templates can be published to AD DS. If you are not connected, use the More Actions\Connect To
Another Writable Domain Controller command in the Action pane to
connect to a DC. You are ready to create the templates you require. Select the source template, right-click the template,
click Duplicate Template, and then select the version of Windows
Server to support. This should always be Windows Server 2008 unless you are
running in a mixed PKI hierarchy. Name the new template, customize it, and save the
customizations. Customize templates according to the following
guidelines: To create an EFS template, select the Basic EFS
template as the source, duplicate it for Windows Server
2008, and name it. Use a valid name, such as Basic EFS WS08,
and then move through the property tabs to customize its
content. Pay particular attention to key archival on the
Request Handling tab, and make sure you select the
Archive Subject’s Encryption Private Key check
box. Also, use encryption to send the key to the CA. Archival storage of the private key allows
you to protect it if the user ever loses it. You can also
use the Subject Name tab to add information such as
Alternate Subject Name values. Click OK. If you plan to use EFS, you must also create an
EFS Recovery Agent template. Duplicate it for
Windows Server 2008. Name it with a valid name such as EFS
Recovery Agent WS08. Publish the recovery agent certificate in Active Directory by selecting the Publish
Certificate In Active Directory checkbox. Note
that the recovery agent certificate is valid for a much
longer period than the EFS certificate itself. Also, use the
same settings on the other property tabs as you assigned to
the Basic EFS duplicate.
If you plan to use wireless networks, create a
Network Policy Server (NPS) template for use
with your systems. Basically, you create the template and
configure it for autoenrollment. Then, the next time the NPS
servers in your network update their Group Policy settings,
they will be assigned new certificates. Use the RAS and IAS
Server templates as the sources for your new NPS template.
Duplicate it for Windows Server 2008. Name it appropriately,
such as NPS Server WS08. Publish it in Active Directory. On
the Security tab, select the RAS and IAS Servers group to
assign the Autoenroll and Enroll permissions. Review other
tabs as needed and save the new template. If you want to use smart card logons, create
duplicates of the Smartcard Logon and Smartcard User
templates. Set the duplicates for Windows
Server 2008. Name them appropriately and publish them in
Active Directory. You do not use Autoenrollment for these
certificates because you need to use smart card enrollment
stations to distribute the smart cards to the users. If you want to protect web servers or DCs, create
duplicates of the Web Server and Domain Controller
Authentication templates. Do not use the Domain Controller
template; it is designed for earlier versions of the
operating system. Duplicate them for Windows Server 2008,
publish them in Active Directory, and verify their other
properties.
Note:
CONFIGURING DUPLICATE
TEMPLATES
The configuration of each template type often includes
additional activities that are not necessarily tied to AD CS.
Make sure you view the AD CS online help to review the
activities associated with the publication of each certificate type.
Now that your templates are ready, you must issue the
template to enable the CA to issue certificates based on these
customized templates. In Server Manager, expand Roles\Active Directory Certificate
Services\Issuing CA Name and select
Certificate Templates. To issue a template, right-click Certificate Templates,
point to New, and then click Certificate Template To
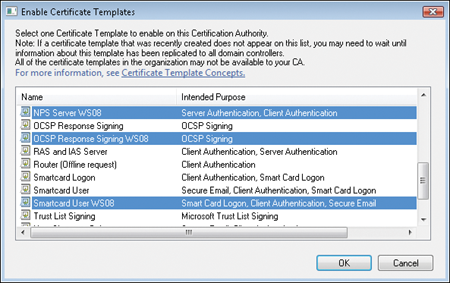
Issue. In the Enable Certificate Templates dialog box, shown in
Figure 1, hold
down the Ctrl key and click to select all the templates you want
to issue, and then click OK.
Now you’re ready to configure enrollment. This is done through
Group Policy. You can choose either to create a new Group Policy for
this purpose or modify an existing Group Policy object. This policy
must be assigned to all members of the domain; therefore, the
Default Domain Policy might be your best choice; if you do not want
to modify this policy, create a new policy and assign it to the
entire domain by using the Group Policy Management Console
(GPMC).
Log on to a DC, and then launch Group Policy Management
from the Administrative Tools program group. Locate or create the appropriate policy, right-click it,
and then click Edit. To assign autoenrollment for computers, expand Computer
Configuration\Policies\Windows Settings\Security Settings and
select Public Key Policies. Double-click Certificate Services Client –
Auto-Enrollment. Enable the policy and select the Renew Expired
Certificates, Update Pending Certificates, And Remove Revoked
Certificates check box. Select the Update Certificates That Use Certificate Templates check box if you have
already issued some certificates manually. Click OK to assign
these settings. To assign autoenrollment for users, expand User
Configuration\Policies\Windows Settings\Security Settings and
select Public Key Policies. Enable the Certificate Services Client – Auto-Enrollment
policy and select the same options as for computers. Notice that you can enable Expiration Notification for
users. Enable it and set an appropriate value. Users will be notified when their certificates are about
to expire. Click OK to assign these settings.
Warning:
IMPORTANT
COMPUTER AND USER GROUP POLICY SETTINGS
Normally, you should not apply both user and computer
settings in the same Group Policy object. This is done here
only to illustrate the settings you need to apply to enable
autoenrollment.
Return to the issuing CA and move to Server Manager to set the
default action that your issuing CA will use when it receives certificate
requests. Right-click the issuing CA server name under AD CS and
click Properties. On the Policy Module tab, click Properties. To have certificates issued automatically, select Follow
The Settings In The Certificate Template, If Applicable.
Otherwise, Automatically Issue The Certificate. Click OK. Click OK again to close the Properties dialog box.
Your issuing CA is now ready for production and will begin
to issue certificates automatically when they are requested either
by devices or by users.
|