After the Forefront Threat Management Gateway 2010
installation completes, the configuration of the reverse proxy rules can
begin. The following sections describe how to create the components
required to publish the Lync Server services.
Getting Started Wizard
After opening the
Forefront TMG Console from the Start menu the first time, it presents
the Getting Started Wizard. This wizard assists an administrator in
configuring the initial setup tasks.
1. | Click Configure network settings.
|
2. | Click Next to begin the Network Setup Wizard.
|
3. | Select Edge firewall, and then click Next.
|
4. | In the Network adapter for the LAN selection box, choose the network adapter that faces the internal network.
Tip
When reverse proxy has
multiple network adapters, only a single default gateway should be used,
which is usually placed on the externally facing adapter. The
internal-facing adapter should have an IP address and subnet mask
assigned, but no default gateway. To reach the internal networks, add
routing statements to the reverse proxy to direct traffic for those
networks through the internal-facing adapter.
|
5. | Verify the IP address and subnet mask configuration. Add required routes to internal networks, and click Next.
|
6. | In the Network adapter connected to the Internet selection box, choose the external-facing adapter and click Next.
|
7. | Click Finish to complete the Network Setup Wizard.
|
8. | Click Configure system settings.
|
9. | Click Next to begin the System Configuration Wizard.
|
10. | Verify the computer name, domain membership, and primary DNS suffix. Click Next.
Note
To leverage the strongest form
of Forefront Threat Management Gateway pre-authentication, Kerberos
Constrained Delegation, it must be a member of the Active Directory
domain.
|
11. | Click Finish to complete the System Configuration Wizard.
|
12. | Click Define deployment options.
|
13. | Click Next to begin the Deployment Wizard.
|
14. | Select a Microsoft Update option and click Next.
|
15. | Select Activate complementary license and enable NIS in the Network Inspection System selection.
|
16. | Select to enable Web Protection features if desired, and then click Next.
|
17. | Configure the NIS Signature Update Settings to meet the organization requirements, and then click Next.
|
18. | Select whether to participate in the Customer Experience Improvement Program and then click Next.
|
19. | Select a participation level for Microsoft telemetry reporting and then click Next.
|
20. | Click Finish to complete the Deployment Wizard.
|
21. | Clear the Run web access wizard check box and then click Close to complete the initial configuration.
|
Install Certificates
Before creating rules
or Forefront Threat Management Gateway rules the appropriate
certificates should be installed on the server. The required subject
name should match the external URL of the pool and include subject
alternative names for simple URLs created for dial-in conferencing or
meetings. If the Lync Server Certificate Wizard is used, the External
Edge services certificate may already contain all the required names.
To present the certificate to
external clients, the certificate must have the private key associated.
If exporting certificates from other servers, include the private key.
If the private key is not available for export, the certificate might
need to be re-issued, but with the “private key is exportable” option.
Additionally,
be sure the Forefront Threat Management Gateway has the root
certificate of any internal certificate authorities used to issue
certificates to internal Lync Server pools. For Threat Management
Gateway to successfully publish internal pools, it must be able to
access the HTTPS ports on the internal servers and trust the
certificates presented for web services.
Create Web Listener
The first step in configuring any kind of HTTPS publishing in Threat Management Gateway is to create a web listener. Web listeners
are objects that a web publishing rule uses to determine IP addresses
and certificates to present to external clients. Web listeners can be
created during the Web Publishing Wizard, but if changes are required,
the entire wizard must be cancelled. For this reason, create the web
listener object in advance of the rule configuration.
1. | Open the Forefront TMG Console from the Start menu.
|
2. | Expand the Forefront TMG (<Computer Name>) node and then click Firewall Policy.
|
3. | In the far right pane, click the Toolbox link.
|
4. | In the Network Objects section, right-click Web Listeners and select New web listener.
|
5. | Enter a name for the Web Listener and click Next.
|
6. | Select Require SSL secured connections with clients and click Next.
|
7. | If the Threat Management Gateway publishes only a single public IP address, check the External box. If multiple IP addresses are bound to the server, click Select IP addresses and choose only the IP addresses used by the listener. Click Next.
|
8. | Click the Select certificate button to choose the certificate that the web listener will present to external clients, as shown in Figure 1. Click Select and then Next.
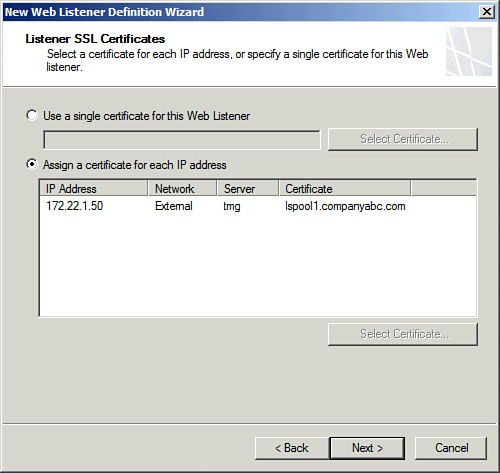
|
9. | In the Select how clients will provide credentials to Forefront TMG box, select No authentication and click Next.
Note
This selection does not
necessarily mean anonymous access to Lync Server pools is allowed. It
simply means the Forefront Threat Management Gateway is not responsible
for pre-authenticating users. Instead, users are authenticated by the
Front End pools before being allowed to access content.
|
10. | Click Next because single sign on is not available with this type of authentication.
|
11. | Click Finish to complete the wizard. |