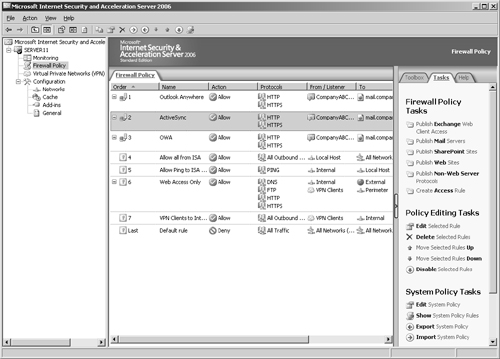
Allowing your information workers access to a
technology like ActiveSync can do wonders for productivity, but can also
potentially expose your organization to threats from the outside. Just
like Outlook Web Access or Outlook Anywhere, ActiveSync requires a web
connection to be available to a CAS. Because ActiveSync is meant to be
used when out of the office, the web traffic must go over the Internet
and must be accessible without requiring a specific virtual private
network (VPN) client to be utilized.
This creates somewhat of a
dilemma, as the HTTP used by ActiveSync can be subject to attack,
potentially exposing your organization to unnecessary risk. Fortunately,
however, Microsoft Exchange Server 2007 can be readily secured against
these types of attack with the use of an Application-layer inspection
product such as the Internet Security and Acceleration (ISA) Server 2006
product available from Microsoft.
Understanding How ISA Server 2006 Can Protect ActiveSync
ISA Server 2006 is
an Application-layer aware firewall that can filter HTTP traffic for
exploits and scumware. It can reside inline to the ActiveSync traffic
(as a traditional firewall), or as a dedicated reverse proxy system that
sits in the demilitarized zone (DMZ) of a packet-filter firewall,
similar to the scenario shown in Figure 1.
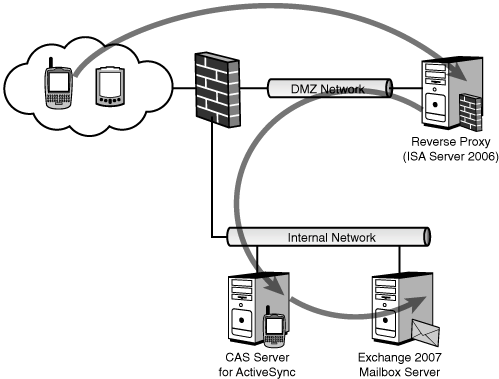
In this scenario, the
client believes it is directly accessing the CAS, but it is instead
being secretly authenticated and scanned at the ISA server itself. Using
this scenario or the inline firewall scenario with ISA Server 2006 is a
highly useful way to secure the ActiveSync traffic.
Creating an ActiveSync Securing Rule in ISA Server 2006
To create the rule in the ISA Server console, perform the following steps:
1. | Open the ISA Management Console and navigate to the Firewall Policy node in the console pane.
|
2. | On the Tasks tab of the tasks pane, click the Publish Exchange Web Client Access link.
|
3. | Enter a descriptive name in the welcome dialog box, such as “ActiveSync Rule,” and click Next.
|
4. | In the Select Services dialog box, shown in Figure 2, change the Exchange version to Exchange Server 2007, and then check the Exchange ActiveSync check box. Click Next to continue.
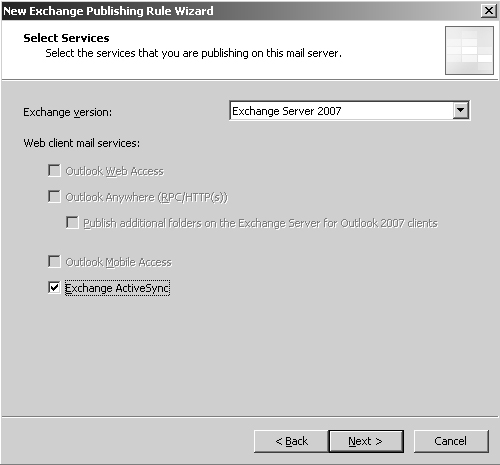
|
5. | In the Publishing Type dialog box, click the Publish a Single Web Site or Load Balancer, and click Next to continue.
|
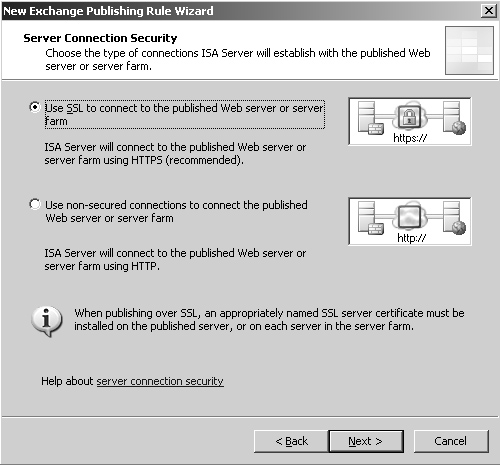
6. | In the Server Connection Security dialog box, shown in Figure 3,
click the Use SSL to Connect to the Published Web Server or Server Farm
option. This creates an end-to-end SSL connection. Click Next to
continue.
|
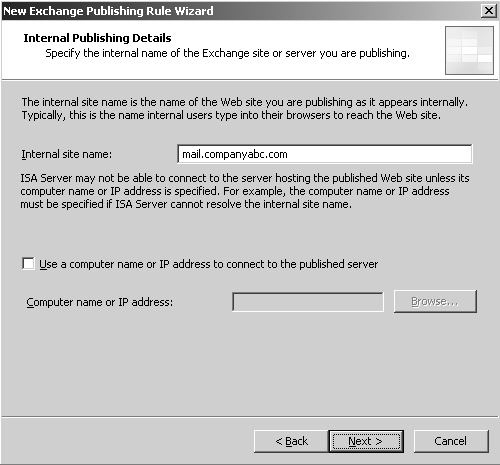
7. | For the internal site name, enter the FQDN that clients use to connect to the CAS, as shown in Figure 4.
In this case, the name should match what the external clients use, as
problems can be encountered when using SSL if the names do not match. If
internal DNS does not forward that FQDN to the CAS, you might need to
fool the ISA server by using a hosts file to make it resolve the FQDN to
the CAS. Click Next to continue.
|
8. | Under
Public Name Details, enter “This domain name,” and then type in the
FQDN of the public name, such as mail.companyabc.com. Click Next to
continue.
|
9. | For
Web Listener, either choose an existing listener that can be used for
OWA or Outlook Anywhere, or click the New button. This scenario assumes
you are creating a new listener. Click the New button.
|
10. | At
the start of the Web Listener Wizard, enter a descriptive name for the
listener, such as Exchange HTTP/HTTPS Listener, and click Next to
continue.
|
11. | A
prompt appears to choose between SSL and non-SSL. This prompt refers to
the traffic between the client and ISA, which should always be SSL
whenever possible. Click Next to continue.
|
12. | Under Web Listener IP addresses, select the External Network, and leave it at All IP Addresses. Click Next to continue.
|
13. | Under Listener SSL Certificates, click Select Certificate.
|
14. | Select the mail.companyabc.com
certificate. If the certificate is not on the ISA server, it must be
installed into the Certificates store of the ISA server.
|
15. | Click Next to continue.
|
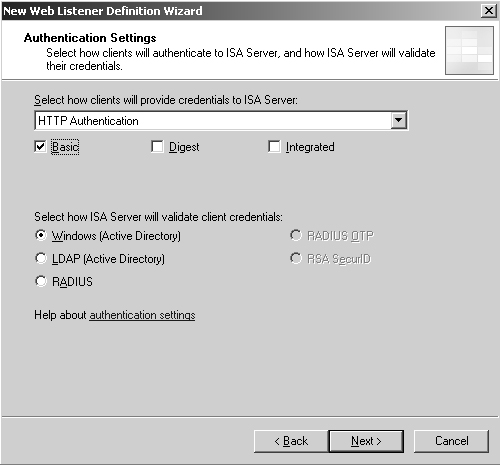
16. | For the type of authentication, choose HTTP Authentication and then check the Basic check box, as shown in Figure 5. Leave Windows (Active Directory) selected, and click Next.
|
17. | Click Next at the Single Sign on Settings dialog box. SSO is not available with Basic authentication.
|
18. | Click Finish to end the wizard.
|
19. | Click Next after the new listener is displayed in the Web Listener dialog box.
|
20. | Under
Authentication Delegation, choose Basic from the drop-down list. Basic
is used as the secured transport mechanism chosen. Click Next to
continue.
|
21. | Under
User Sets, leave All Authenticated Users selected. In stricter
scenarios, only specific AD groups can be granted rights to OWA using
this setting. In this case, the default is fine. Click Next to continue.
|
22. | Click Finish to end the wizard.
|
23. | Click Apply in the details pane, and then click OK when you are finished to commit the changes.
|
The ActiveSync Policy will then show up in the details pane, as shown in Figure 6. Further customization of the rule can take place if necessary.