In most enterprises today, each individual
application or system has its own user database or directory to track
who is permitted to use that resource. Identity and access control data
reside in different directories as well as applications such as
specialized network resource directories, mail servers, human resource,
voice mail, payroll, and many other applications.
Each has its own
definition of the user’s “identity” (for example, name, title, ID
numbers, roles, membership in groups). Many have their own password and
process for authenticating users. Each has its own tool for managing
user accounts and, sometimes, its own dedicated administrator
responsible for this task. In addition, most enterprises have multiple
processes for requesting resources and for granting and changing access
rights. Some of these are automated, but many are paper-based. Many
differ from business unit to business unit, even when performing the
same function.
Administration
of these multiple repositories often leads to time-consuming and
redundant efforts in administration and provisioning. It also causes
frustration for users, requiring them to remember multiple IDs and
passwords for different applications and systems. The larger the
organization, the greater the potential variety of these repositories
and the effort required to keep them updated.
In response to
this problem, Microsoft developed Microsoft Metadirectory Services (MMS)
to provide for identity synchronization between different directories.
As the product improved, it was rereleased under the new name Microsoft
Identity Integration Server (MIIS). For a third time, the tool was
renamed, this time as Identity Lifecycle Manager (ILM) 2007. The latest
and fourth rename of this tool took place shortly before the release of
Exchange Server 2010; Microsoft has now incorporated this tool into its
Forefront security line and named it Forefront Identity Manager (FIM).
The use of FIM for
Exchange Server 2010 is particularly useful because it can synchronize
information between the AD forest that contains Exchange Server and the
other messaging systems in use within the organization.
Understanding FIM
FIM is a
system that manages and coordinates identity information from multiple
data sources in an organization, enabling you to combine that
information into a single logical view that represents all of the
identity information for a given user or resource.
FIM enables a
company to synchronize identity information across a wide variety of
heterogeneous directory and nondirectory identity stores. This enables
customers to automate the process of updating identity information
across heterogeneous platforms while maintaining the integrity and
ownership of that data across the enterprise.
Password management
capabilities enable end users or help desk staff to easily reset
passwords across multiple systems from one easy-to-use web interface.
End users and help desk staff no longer have to use multiple tools to
change their passwords across multiple systems.
Understanding FIM
Concepts
It is important to
understand some key terms used with FIM before comprehending how it can
be used to integrate various directories. Keep in mind that the
following terms are used to describe FIM concepts but might also help
give you a broader understanding of how metadirectories function in
general:
Management agent (MA)—
A FIM MA is a tool used to communicate with a specific type of
directory. For example, an Active Directory MA enables FIM to import or
export data and perform tasks within Active Directory.
Connected directory (CD)— A connected directory is a directory that FIM
communicates with using a configured MA. An example of a connected
directory is an Active Directory forest.
Connector namespace (CS)— The connector namespace is the replicated information
and container hierarchy extracted from or destined to the respective
connected directory.
Metaverse namespace (MV)— The metaverse namespace is the authoritative
directory data created from the information gathered from each of the
respective connector namespaces.
Metadirectory—
Within FIM, the metadirectory is made up of all the connector namespaces
plus the authoritative metaverse namespace.
Attributes— Attributes are the fields of information that are
exported from or imported to directory entries. Common directory entry
attributes are name, alias, email address, phone number, employee ID, or
other information.
FIM can be used for many
tasks, but is most commonly used for managing directory entry identity
information. The intention here is to manage user accounts by
synchronizing attributes, such as logon ID, first name, last name,
telephone number, title, and department. For example, if a user named
Jane Doe is promoted and her title is changed from manager to vice
president, the title change could first be entered in the HR or Payroll
databases; then through FIM MAs, the change could be replicated to other
directories within the organization. This ensures that when someone
looks up the title attribute for Jane Doe, it is the same in all the
directories synchronized with FIM. This is a common and basic use of FIM
referred to as identity management. Other common uses of FIM include
account provisioning and group management.
Note
FIM is a versatile and powerful directory
synchronization tool that can be used to simplify and automate some
directory management tasks. Because of the nature of FIM, it can also be
a very dangerous tool as MAs can have full access to the connected
directories. Misconfiguration of FIM MAs could result in data loss, so
careful planning and extensive lab testing should be performed before
FIM is released to the production directories of any organization. In
many cases, it might be prudent to contact Microsoft consulting services
and certified Microsoft solution provider/partners to help an
organization decide whether FIM is right for its environment, or even to
design and facilitate the implementation.
Exploring FIM
Account Provisioning
FIM enables
administrators to easily provision and deprovision users’ accounts and
identity information, such as distribution, email and security groups
across systems, and platforms. Administrators will be able to quickly
create new accounts for employees based on events or changes in
authoritative stores such as the human resources system. In addition, as
employees leave a company, they can be immediately deprovisioned from
those same systems.
Account
provisioning in FIM enables advanced configurations of directory MAs,
along with special provisioning agents, to be used to automate account
creation and deletion in several directories. For example, if a new user
account is created in Active Directory, the Active Directory MA could
tag this account. Then, when the respective MAs are run for other
connected directories, a new user account could be automatically
generated.
One enhancement of FIM
over previous versions is that password synchronization is now supported
for specific directories that manage passwords within the directory.
FIM provides an application programming interface (API) accessed through
the Windows Management Instrumentation (WMI). For connected directories
that manage passwords in the directory’s store, password management is
activated when an MA is configured in MA Designer. In addition to
enabling password management for each MA, Management Agent Designer
returns a system name attribute using the WMI interface for each
connector space object.
Outlining the Role
of Management Agents (MAs) in FIM
An MA links a specific
connected data source to the metadirectory. The MA is responsible for
moving data from the connected data source and the metadirectory. When
data in the metadirectory is modified, the MA can also export the data
to the connected data source to keep the connected data source
synchronized with the metadirectory. Generally, there is at least one MA
for each connected directory. FIM includes MAs for multiple directory
sources, as shown in Figure 1.
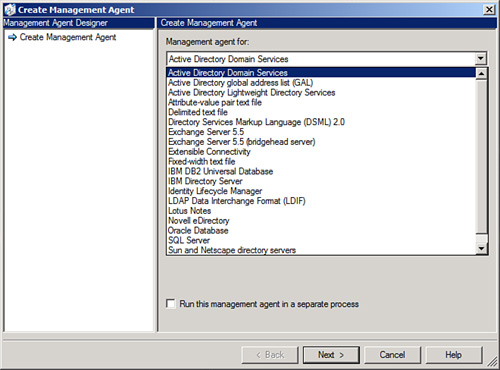
Note
FIM includes integrated support for synchronization
with additional directories such as Oracle, SAP, Lotus Notes, and more.
In addition, it also introduced the ability for end users to reset
their own passwords via a web management interface.
MAs contain rules that
govern how an object’s attributes are mapped, how connected directory
objects are found in the metaverse, and when connected directory objects
should be created or deleted.
These agents are used to
configure how FIM will communicate and interact with the connected
directories when the agent is run. When an MA is first created, all the
configuration of that agent can be performed during that instance. The
elements that can be configured include which type of directory objects
will be replicated to the connector namespace, which attributes will be
replicated, directory entry join and projection rules, attribute flow
rules between the connector namespace and the metaverse namespace, plus
more. If a necessary configuration is unknown during the MA creation, it
can be revisited and modified later.
Defining FIM and
Group Management
Just as FIM can
perform identity management for user accounts, it also can perform
management tasks for groups. When a group is projected into the
metaverse namespace, the group membership attribute can be replicated to
other connected directories through their MAs. This enables a group membership
change to occur in one directory and be replicated to other directories
automatically.
Installing FIM
with SQL Server
Both versions of FIM
require a licensed version of SQL Server 2005 or 2008 to run, and an
install of the product will prompt for the location of a SQL server.
It is not necessarily
required to install a new instance of SQL because an existing SQL
instance can be used as well. If an existing SQL 2005/2008 server is not
available, SQL can be installed on the same system as FIM.
Deploying FIM for
Identity Management with Novell eDirectory
FIM can be an
effective tool for managing identities between Novell eDirectory
environments and Active Directory. Identity information could include
names, email and physical addresses, titles, department affiliations,
and much more. Generally speaking, identity information is the type of
data commonly found in corporate phone books or intranets. To use FIM
for identity management between Active Directory and Novell eDirectory,
follow these high-level steps:
1. | Install FIM and the latest service packs and patches.
|
2. | Create an MA for each of the directories, including an
Active Directory MA and a Novell eDirectory MA.
|
3. | Configure the MAs to import directory object types into
their respective connector namespaces.
|
4. | Configure one of the MAs—for example, the Active
Directory MA—to project the connector space directory objects and
directory hierarchy into the metaverse namespace.
|
5. | Within each of the MAs, a function can be configured
called attribute flow, which defines which directory object attributes
from each directory will be projected into the respective metaverse
directory objects. Configure the attribute flow rules for each MA.
|
6. | Configure the account-joining properties for directory
objects. This is the most crucial step because it determines how the
objects in each directory are related to one another within the
metaverse namespace. To configure the account join, certain criteria can
be used, such as employee ID or first name and last name combination.
The key is to find the most unique combination to avoid problems when
two objects with similar names are located—for example, if two users
named Tom Jones exist in Active Directory.
|
7. | After completely configuring the MAs and account joins,
configure MA run profiles to tell the MA what to perform with the
connected directory and connector namespace. For example, perform a full
import or export of data. The first time the MA is run, the connected
directory information is imported to create the initial connector
namespace.
|
8. | After
running the MAs once, you can run them a second time to propagate the
authoritative metaverse data to the respective connector namespaces and
out to the connected directories.
|
These steps outline the
most common use of FIM; these steps can be used to simplify account
maintenance tasks when several directories need to be managed
simultaneously. When more sophisticated functionality using FIM is
needed, such as the automatic creation and deletion of directory
entries, extensive scripting and customization of FIM can be done to
create a more complete enterprise account provisioning system.