Auditing lets you track what's happening with
Exchange Server. You can use auditing to collect information related to
information logons and logoffs, permission use, and much more. Any time
an action that you've configured for auditing occurs, this action is
written to the system's security log, where it's stored for your review.
You can access the security log from Event Viewer.
1. Using Auditing
You enable auditing in the
domain through Group Policy. You can think of group policies as sets of
rules that help you manage resources. You can apply group policies to
domains, organizational units within domains, and individual systems.
Policies that apply to individual systems are referred to as local group policies and are stored only on the local system. Other group policies are linked as objects in Active Directory.
You can audit Exchange
activity by enabling auditing in a Group Policy object applied to your
Exchange servers. This policy object can be a local Group Policy object
or an Active Directory Group Policy object. You manage a server's local
Group Policy object using the Local Security Policy tool. You manage
Active Directory Group Policy using the Group Policy Management Console
(GPMC). GPMC is included as a Windows feature with Windows Vista and
later versions of the Windows operating system. After you add GPMC as a
feature, you can access it on the Administrative Tools menu.
2. Configuring Auditing
You can enable Exchange auditing by completing the following steps:
Start
the Group Policy Management Console by clicking Start, All Programs,
Administrative Tools, Group Policy Management. You can now navigate
through the forest and domains in the organization to view individual
Group Policy objects. To
specifically audit users' actions on Exchange Server, you should
consider creating an organizational unit (OU) for Exchange servers and
then define auditing policy for a Group Policy object applied to the OU.
After you've created the OU or if you have an existing OU for Exchange
servers, right-click the related policy object, and then select Edit to
open the policy object for editing in Group Policy Management Editor. As shown in Figure 1
you access the Audit Policy node by working your way down through the
console tree. Expand Computer Configuration, Policies, Windows Settings,
Security Settings, and Local Policies. Then select Audit Policy.
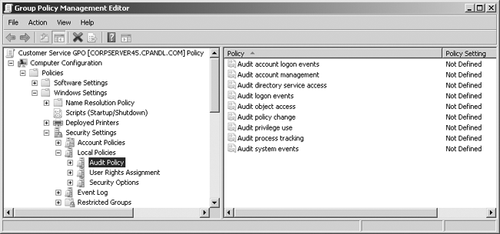
You should now see the following auditing options: Audit Account Logon Events
Tracks user account authentication during logon. Account logon events
are generated on the authenticating computer when a user is
authenticated. Audit Account Management
Tracks account management by means of Active Directory Users And
Computers. Events are generated any time user, computer, or group
accounts are created, modified, or deleted. Audit Directory Service Access Tracks access to Active Directory. Events are generated any time users or computers access the directory. Audit Logon Events Tracks local logon events for a server or workstation. Audit Object Access Tracks system resource usage for mailboxes, information stores, and other types of objects. Audit Policy Change Tracks changes to user rights, auditing, and trust relationships. Audit Privilege Use Tracks the use of user rights and privileges, such as the right to create mailboxes. Audit Process Tracking Tracks system processes and the resources they use. Audit System Events Tracks system startup, shutdown, and restart, as well as actions that affect system security or the security log.
To configure an auditing
policy, double-click or right-click its entry, and then select
Properties. This opens a Properties dialog box for the policy. Select
the Define These Policy Settings check box, and then select the Success
check box, the Failure check box, or both. Success logs successful
events, such as successful logon attempts. Failure logs failed events,
such as failed logon attempts. Repeat steps 5 and 6 to enable other auditing policies. The policy changes won't be applied until the next time you start the Exchange server.
|