The Edge Server role in Lync Server comprises three
separate subroles just as in previous versions of the product: Access
Edge Server, Web Conferencing Edge Server, and A/V Edge Server role.
Each role provides slightly different functionality and depending on the
organization’s requirements it might not be necessary to use all three
services. With Lync Server 2010, all three roles are deployed together
as opposed to individually like in previous product versions.
Unlike
many of the internal roles, the Edge Server does not require database
or file shares because it does not store data other than the Local
Configuration Store replica from the Central Management Store. Because
the Edge Server is designed to be deployed in a perimeter or DMZ
network, it runs a limited set of services to make it as secure as
possible. Edge Servers are also typically not joined to the internal
Active Directory domain, but can be if necessary. The different Edge
Server roles provide unique features, as shown in Figure 1. The reverse proxy server also provides some external services through the Front-End pool.
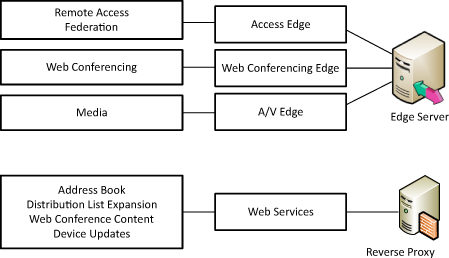
Access Edge
The Access Edge role serves
as the core of the Edge Server and is responsible for all of the
signaling functionality. Without the Access Edge role deployed, the Web
Conferencing Edge and A/V Edge roles cannot function. The Access Edge
also serves a few distinct purposes including remote access, federation,
and Public IM Connectivity.
Remote Access
One function of the Access Edge
Server is to provide remote access capabilities to a Lync Server
infrastructure. After an internal deployment of pools is complete, an
Access Edge Server can be provisioned to enable users to sign in and use
their endpoints across the Internet.
As long as the appropriate SRV
records exist in DNS or the client is manually configured correctly, a
user can travel in and out of the office without ever making a change to
an endpoint. This enables users to have full access to their internal
features regardless of location.
Note
Access
Edge Server traffic is performed using port 443 over TCP, which is the
standard for HTTPS traffic. Traffic is rarely blocked or interfered with
by any kind of proxy or firewall software.
Federation
The Access Edge Server also
provides the capability to federate with other organizations that have
deployed Lync Server, meaning the two organizations can communicate with
each other as if it were a single deployment.
Users have different
feature sets available when using federation, depending on the version
of Lync Server a partner has deployed. The feature set is the lowest
common denominator between the two organizations. For example, if a
partner runs Live Communications Server 2005, only IM and presence will
be available. However, if a partner organization is running Office
Communications Server 2007 R2, A/V and Desktop Sharing features can be
used through federation. The largest feature set is available if both
organizations are running Lync Server.
Access Edge Servers
use certificates and mutual TLS (MTLS) to secure the SIP signaling used
across the Internet with each other. This ensures that instant messaging
and presence traffic is completely secure and never transmitted in
plain text.
Note
Organizations
generally procure a certificate from a public certificate authority so
that partners trust their server by default. However, it is possible to
exchange certificate chains with a partner to support additional
certificate authorities.
Public IM Connectivity
A special form of
federation is the capability to use Lync Server to communicate with
contacts on the public IM networks, referred to as Public IM
Connectivity (PIC). The AOL, Yahoo!, and MSN networks are the native
Public IM Connectivity providers to Lync Server. To communicate with
these contacts, users simply need to add the address to a contact list.
Caution
Although it is possible to
federate with Google Talk contacts, this capability is not native to the
Access Edge Server role. To federate with Google Talk, an organization
must deploy the XMPP Gateway Server role, which was software introduced
for Office Communications Server 2007 R2. There is no equivalent or
updated product for Lync Server at this time.
Lync Server users can see
presence and exchange instant messages with their contacts when Public
IM Connectivity is provisioned. The conversations are limited to
peer-to-peer, though,
and they cannot include three or more participants as users are
accustomed to within the organization or with federated contacts.
Audio and video support with
the MSN or Windows Live networks is a new feature in Lync Server. The
A/V conversations are performed using the same RTAudio and RTVideo
codecs native to both platforms, but are also limited to two-party
calls.
Tip
With Microsoft Xbox Kinect
and Xbox Live service, it’s possible to conduct a video conversation
with an MSN user viewing a Lync Server user on his or her television at
home or work, as shown in Figure 2. This functionality will be delivered in a future update to the Kinect software.
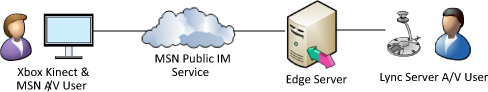
As of this writing, only the
Yahoo! network requires additional licensing, which is done on a
per-user monthly subscription fee. As long as users have a Lync Server
Standard CAL, the AOL and MSN Public IM Connectivity are provided at no
extra cost.
Web Conferencing Edge
When joining a web
conference, users first authenticate to the Access Edge Server before
the client joins using the Web Conferencing Edge Server role. The Web
Conferencing Edge Server enables remote users to participate in web
conferences with internal users or other remote workers.
Organizations may also
elect to enable anonymous or unauthenticated users to join web
conferences with their own users. This functionality is similar to what
many hosted web conferencing services offer. However, it is provided by
the organization’s own Lync Server infrastructure. Web conferencing uses
Microsoft’s Proprietary Shared Object Model (PSOM) protocol to
facilitate the meetings and data. Like the Access Edge traffic, all Web
Conferencing Edge traffic is conducted over HTTPS port 443, so it is
secure and resilient to proxy servers.
A/V Edge
The A/V Edge role is
responsible for providing audio and video media exchanges among
internal, external, and federated contacts. The A/V Edge role uses the
Interactive Connectivity Establishment (ICE), Simple Traversal Utilities
for NAT (STUN), and Traversal Using Relay NAT (TURN) methods to enable endpoints to communicate even if behind a NAT device.
When possible, endpoints
attempt to use a peer-to-peer connection for media streams, but when an
endpoint is behind a NAT device such as a home router, the A/V Edge role
can act as a relay point between the endpoints to facilitate
communication. The A/V Edge service uses a combination of HTTPS port 443
and UDP port 3478 to negotiate and provide the media stream.
To support media traffic
between internal and external users, an additional service exists on the
A/V Edge Server called the A/V Edge Authentication Service. This
service is responsible for authenticating media requests from internal
users to external contacts. When a user wants to initiate an external
A/V conversation, she is provided with a temporary media token that she
uses to authenticate to this service before media is allowed to flow.
Collocation
The Edge Server roles
cannot be collocated with any other role in Lync Server. Although many
of the other roles depend on access to Active Directory, Edge Servers
are typically placed in a perimeter network and might not even be joined
to the corporate domain for security reasons.
Caution
Although it is possible to
join an Edge Server to the domain, this is not a recommended
configuration because it will still not allow for the collocation of any
other server roles.
In previous
versions of Communications Server, it was possible to install only
specific Edge roles. However, in Lync Server, the three roles are always
installed together. This change cuts down on confusion of deployment
models, which required knowing which Edge roles were safe to collocate
together.
Reverse Proxy
In addition to the Edge
Server roles that provide remote access, federation, web conferencing,
and A/V conferencing, a reverse proxy is required to publish the web
components services that don’t run through an Edge Server.
Tip
Oftentimes, the reverse proxy
component is overlooked or considered unnecessary. However, it is a
critical step in deploying external access for users.
The reverse proxy provides
remote access to the web components running on Front End Servers or Edge
Servers. This includes the following features:
There are many vendors and
types of reverse proxies, and almost any of them work with Lync Server
because the publishing needs are fairly basic.