5. Planning NAP DHCP Enforcement
DHCP enforcement provides for NAP enforcement
before an IPv4 client receives its automatic configuration information
from a DHCP server. DHCP enforcement uses a limited IPv4 configuration
to restrict a DHCP client to a restricted network to perform
remediation.
DHCP enforcement combines the use of Windows
Server 2008 running the DHCP Server service, the NPS service for RADIUS
client capabilities, and the supported Windows clients:
Windows XP SP3
Windows Vista
Windows Server 2008
DHCP enforcement uses the following configurations of IPv4 to restrict a noncompliant client:
Sets the router option to 0.0.0.0 for noncompliant clients
Sets the subnet mask for the IPv4 address to 255.255.255.255
Uses the Classless Static Routes DHCP option to set host routes to specified computers on the restricted network
DHCP enforcement is simple to set up but has some considerable disadvantages when compared to other forms of NAP enforcement:
It is relatively the weakest form of NAP enforcement.
A local administrator can override the settings by setting an appropriate manual IPv4 configuration to access the network.
It does not provide support for IPv6 environments. Currently, DHCP enforcement is an IPv4-only solution.
Design Considerations for DHCP Enforcement
Several items need to be in place for a successful DHCP enforcement solution:
All DHCP servers need to be upgraded to Windows Server 2008.
All DHCP servers need to add the NPS role and configure a Remote Servers group containing the NAP health policy servers.
Installation of RADIUS infrastructure is necessary if one is not already deployed.
Consideration is necessary for how to implement exemptions for non-NAP-capable computers.
The network infrastructure, switches, routers,
and Active Directory domain controllers require no updates or upgrades.
Only the DHCP servers need to be upgraded to Windows Server 2008;
install the NPS service and configure the service to function as a
RADIUS proxy for the back-end NAP health policy servers.
Final Say on DHCP Enforcement
Despite all the disadvantages of DHCP
enforcement, it can provide a fine solution for a small company intent
on enhancing its malware protection services. For larger environments,
DHCP enforcement can provide an inexpensive reporting solution, assuming
the necessary Windows Server 2008 components can be installed. For a
small environment, as well as for branch offices in larger enterprises,
one server can be used to deploy all the necessary components, DHCP,
NPS, and NAP health policy server. This is an inexpensive solution to
provide at least a fine reporting tool by which to monitor your
noncompliant clients’ health in your environment and provide a step
toward a more secure environment.
6. Domain and Server Isolation
Domain
isolation and server isolation, introduced initially with Windows
Server 2003, are effective means of improving secure communications
within an enterprise. By ensuring which computers may communicate with
other computers, you provide secure end-to-end authenticated
communication. Securing end-to-end communication is not addressed
through VPN enforcement, DHCP enforcement, or 802.1x enforcement. NAP
IPsec enforcement does provide the same end-to-end authenticated
communication service as isolation and, thus, can implement a similar
style of security while adding support for health policies.
With domain and server isolation, IPsec
authenticated communication defends a computer against network attacks,
protection that application-layer user authentication security services
do not offer. User authentication does prevent users from attacking
specific files and applications, but it is not true security at the
lower layers. IPsec authentication would help prevent attacks against
services running at the network layer.
Domain vs. Server Isolation
Domain isolation is a way of ensuring that
computers that need to communicate are members of the domain and have
received the necessary IPsec policies through Group Policy. This
isolates trusted computers from untrusted computers. All incoming
requests and subsequently transferred data must be authenticated and
protected by IPsec. Using Windows Firewall with Advanced Security policy
settings, you can define IPsec and connections security rules that
either require or request all inbound traffic to be authenticated with
IPsec.
Server isolation is a more selective isolation
method than domain isolation. Server isolation enables the enterprise
administrator to designate specific hosts within the environment that
should require that all client connection requests to it be
authenticated by IPsec, much like domain isolation. In addition, you can
designate select servers to allow communication with specific clients
and servers through:
Selective certificates used for IPsec authentication.
Specific IP addresses, using Windows Firewall with Advanced Security policy settings.
Windows
Server 2008, creating firewall rules that permit traffic from computers
or users who are members of a select Active Directory security group.
Windows
Server 2003, using the local Group Policy Access This Computer From The
Network user right to specify users and computer accounts.
Using either domain or server isolation,
exemptions can be made for computers that are not capable of performing
IPsec authentication or are not members of AD DS.
Comparing Server and Domain Isolation to IPsec Enforcement
From
a high-level perspective, these technologies are more similar than
different. Both technologies use IPsec to provide logical network
segmentation. Both server isolation and domain isolation attempt to make
the network safer through ensuring that only trusted computers can
communicate. IPsec enforcement ensures that computers trusted by health
validation are allowed to communicate. Both use IPsec authentication to
assure communicating computers mutually of their ability to trust and be
trusted. Both technologies can use the default Kerberos authentication
or deploy certificates for computer authentication prior to establishing
IPsec security associations (SAs).
Server isolation enables an administrator to
segment high-value servers further for granular control within the
trusted environment. IPsec NAP can define specific zones of security to
tighten access even further to high-value servers. Figure 3 displays the logical network segmentation that both forms of IPsec isolation can provide.
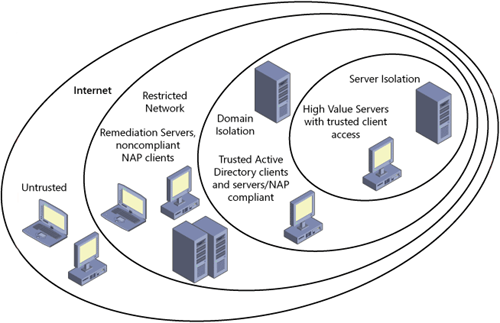
Adding NAP technology to your IPsec isolation solution now provides the following additional security aspects:
Formalizes policy validation for healthy computers
Further restricts computer trust to computers that are managed and healthy
Uses remediation to enable updating for unhealthy managed computers
Creates a system of ongoing enforced compliance that offers flexible management for defining trust
Moving from Server and Domain Isolation to IPsec NAP
If your environment is using Windows 2000 Server
or later, you can use IPsec NAP to provide a trusted environment and
enforce logical network segmentation for the creation of trusted zones.
For networks that have already upgraded to Windows XP SP3 and Windows
Vista on the desktop and have begun the upgrade to Windows Server 2008, a
steady migration toward NAP can begin.
You can begin introducing health validation in
network locations that have already upgraded their operating systems to
NAP-capable clients by implementing a pilot program. This pilot program
should initially use reporting and quickly move toward the
implementation of restriction. After a predominant portion of each
network location—branch offices or the main office—have upgraded to
NAP-capable clients, you can introduce a NAP solution using reporting.
Finally, each office in the network can eventually turn on restriction
after a careful review of logs gathered during the implementation of
reporting only.
Proper planning is essential to a NAP
implementation. It is conceivable that if IPsec NAP is your choice of
NAP enforcement, then first instituting server and domain isolation in
phases throughout your environment would be a good starting place.