For administrators of large networks, one of the main
objectives is to minimize the amount of travel from site to site to
work on individual computers. Many of the administration tools included
with Windows Server 2003 are capable of managing services on remote
computers as well as on the local system. For example, most Microsoft
Management Console (MMC) snap-ins have this capability, enabling
administrators to work on systems throughout the enterprise without
traveling. These are specialized tools used primarily for server
administration, however, that can perform only a limited number of
tasks. For comprehensive administrative access to a remote computer,
Windows Server 2003 includes two tools that are extremely useful to the
network administrator, called Remote Assistance and Remote Desktop.
Using Remote Assistance
Remote Assistance is a
feature of Windows XP and Windows Server 2003 that enables a user (an
administrator, trainer, or technical support representative) at one
location to connect to a distant user’s computer, chat with the user,
and either view all the user’s activities or take complete control of
the system. Remote Assistance can eliminate the need for administrative
personnel to travel to a user’s location for any of the following
reasons:
Off the Record
In
Microsoft interfaces and documentation, the person connecting to a
client using Remote Assistance is referred to as an expert or a helper. |
Technical support
A system administrator or help desk operator can use Remote Assistance
to connect to a remote computer to modify configuration parameters,
install new software, or troubleshoot user problems.
Troubleshooting
By connecting in read-only mode, an expert can observe a remote user’s
activities and determine whether improper procedures are the source of
problems the user is experiencing. The expert can also connect in
interactive mode to try to recreate the problem or to modify system
settings to resolve it. This is far more efficient than trying to give
instructions to inexperienced users over the telephone.
Training Trainers
and help desk personnel can demonstrate procedures to users right on
their systems, without having to travel to their locations.
To receive remote
assistance, the computer running Windows Server 2003 or Windows XP must
be configured to use the Remote Assistance feature in one of the
following ways:
Using Control Panel
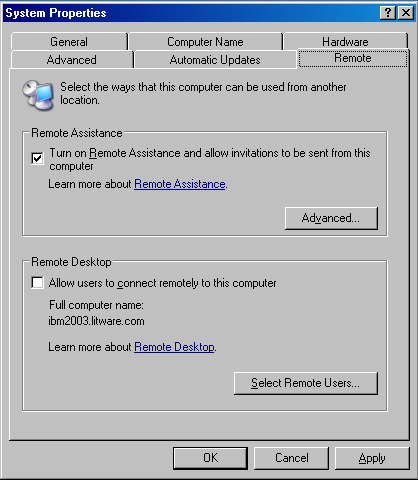
Display the System Properties dialog box from the Control Panel and
click the Remote tab. Then select the Turn On Remote Assistance And
Allow Invitations To Be Sent From This Computer check box (see Figure 1).
Tip
By
clicking the Advanced button in the Remote tab in the System Properties
dialog box, the user can specify whether to let the expert take control
of the computer or simply view activities on the computer. The user can
also specify the amount of time that the invitation for remote
assistance remains valid. |
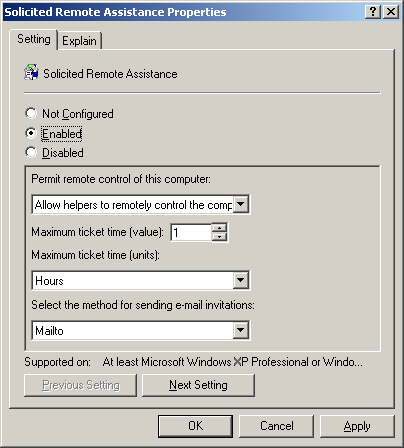
Using Group Policies
Use the Group Policy Object Editor console to open a GPO for an Active
Directory domain or organizational unit object containing the client
computer. Browse to the Computer Configuration\Administrative
Templates\System\Remote Assistance container and enable the Solicited
Remote Assistance policy (see Figure 2).
Tip
The
Solicited Remote Assistance policy also enables you to specify the
degree of control the expert receives over the client computer, the
duration of the invitation, and the method for sending e-mail
invitations. The Offer Remote Assistance policy enables you to specify
the names of users or groups that can function as experts, and whether
those experts can perform tasks or just observe. |
Creating an Invitation
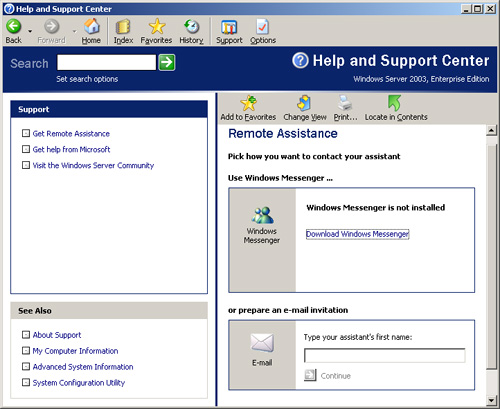
To
receive remote assistance, a client must issue an invitation and send
it to a particular expert. The client can send the invitation using
e-mail, Microsoft Windows Messenger, or can save it as a file to be sent
to the expert in some other manner, using the interface shown in Figure 3.
Tip
When
users create invitations, they can specify a password that the expert
has to supply to connect to their computers. You should urge your users
to always require passwords for Remote Assistance connections, and
instruct them to supply the expert with the correct password using a
different medium from the one they are using to send the invitation. |
Once the expert
receives the invitation, invoking it launches the Remote Assistance
application, which enables the expert to connect to the remote computer,
as shown in Figure 4.
Using this interface, the user and the expert can talk or type messages
to each other and, by default, the expert can see everything that the
user is doing on the computer. If the client computer is configured to
allow remote control, the expert can also click the Take Control button
and operate the client computer interactively.

Securing Remote Assistance
Because an expert
offering remote assistance to another user can perform virtually any
activity on the remote computer that the local user can, this feature
can be a significant security hazard. An unauthorized user who takes
control of a computer using Remote Assistance can cause almost unlimited
damage. However, Remote Assistance is designed to minimize the dangers.
Some of the protective features of Remote Assistance are as follows:
Invitations
No person can connect to another computer using Remote Assistance
unless that person has received an invitation from the client. Clients
can configure the effective lifespan of their invitations in minutes,
hours, or days, to prevent experts from attempting to connect to the
computer later.
Interactive connectivity When
an expert accepts an invitation from a client and attempts to connect
to the computer, a user must be present at the client console to grant
the expert access. You cannot use Remote Assistance to connect to an
unattended computer.
Client-side control
The client always has ultimate control over a Remote Assistance
connection. The client can terminate the connection at any time, by
pressing the Esc key or clicking Stop Control (ESC) in the client-side
Remote Assistance page.
Remote control configuration
Using the System Properties dialog box or Remote Assistance group
policies, users and administrators can specify whether experts are
permitted to take control of client computers. An expert who has
read-only access cannot modify the computer’s configuration in any way
using Remote Access. The group policies also enable administrators to
grant specific users expert status, so that no one else can use Remote
Access to connect to a client computer, even with the client’s
permission.
Firewalls
Remote Assistance uses Transmission Control Protocol (TCP) port number
3389 for all its network communications. For networks that use Remote
Assistance internally and are also connected to the Internet, it is
recommended that network administrators block this port in their
firewalls, to prevent users outside the network from taking control of
computers that request remote assistance. However, it is also possible
to provide remote assistance to clients over the Internet, which would
require leaving port 3389 open.
Using Remote Desktop
While Remote
Assistance is intended to enable users to obtain interactive help from
other users, Remote Desktop is an administrative feature that enables
users to access computers from remote locations, with no interaction
required at the remote site. Remote Desktop is essentially a remote
control program for computers running Windows Server 2003 and Windows
XP; there are no invitations and no read-only capabilities. When you
connect to a computer using Remote Desktop, you can operate the remote
computer as though you were sitting at the console and perform most
configuration and application tasks.
Off the Record
One
of the most useful application of Remote Desktop is to connect to
servers, such as those in a locked closet or data center, that are not
otherwise easily accessible. In fact, some administrators run their
servers without monitors or input devices once the initial installation
and configuration of the computer is complete, relying solely on Remote
Desktop access for everyday monitoring and maintenance. |
Tip
Be
sure that you understand the differences between Remote Assistance and
Remote Desktop, and that you understand the applications for which each
is used. |
Remote Desktop
For Administration is essentially an application of the Terminal
Services service supplied with Windows Server 2003. A desktop version
called Remote Desktop is included with Windows XP Professional. When you
use Terminal Services to host a large number of clients, you must
purchase licenses for them. However, Windows Server 2003 and Windows XP
allow up to two simultaneous Remote Desktop connections without the need
for a separate license.
When you connect to a
computer using Remote Desktop, the system creates a separate session for
you, independent of the console session. This means that even someone
working at the console cannot see what you are doing. You must log on
when connecting using Remote Desktop, just as you would if you were
sitting at the console, meaning that you must have a user account and
the appropriate permissions to access the host system. After you log on,
the system displays the desktop configuration associated with your user
account, and you can then proceed to work as you normally would.
Activating Remote Desktop
By default, Remote
Desktop is enabled on computers running Windows Server 2003 and Windows
XP. Before you can connect to a computer using Remote Desktop, you must
enable it using the System Properties dialog box, accessed from the
Control Panel. Click the Remote tab and select the Allow Users To
Connect Remotely To This Computer check box, as shown earlier in Figure 13-9, and then click OK.
Note
Because
Remote Desktop requires a standard logon, it is inherently more secure
than Remote Assistance, and needs no special security measures, such as
invitations and session passwords. However, you can also click Select
Remote Users in the Remote tab to display a Remote Desktop Users dialog
box, in which you can specify the names of the only users or groups that
are permitted to access the computer using Remote Desktop. All users
with Administrator privileges are granted access by default. |
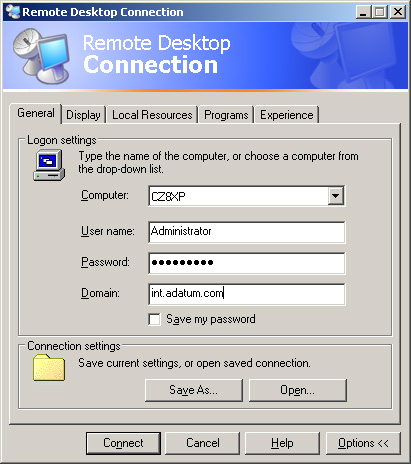
Using the Remote Desktop Client
Both Windows Server
2003 and Windows XP include the client program needed to connect to a
host computer using Remote Desktop (see Figure 5).
In addition, both operating systems include a version of the client
that you can install on earlier Windows operating systems.
Tip
Windows
Server 2003 also includes a Remote Desktops console (accessible from
the Administrative Tools program group) that you can use to connect to
multiple Remote Desktop hosts and switch between them as needed. |