3. Implementing File-Level Antivirus Scanning
Implementing file-level antivirus
scanning can help enhance the security and health of your Exchange Server 2010
organization. However, you need to take care that the file-level scanner you use
is correctly configured. Badly configured file-level scanners can cause problems
in Exchange Server 2010. You can use two types of file-level scanners:
Memory-resident file-level
scanners
The antivirus software is loaded in memory at all times and checks
all the files that are used on the hard disk and in computer
memory.
On-demand file-level
scanners
You can configure the antivirus software to scan files on a hard
disk manually or at scheduled intervals. Some antivirus software
packages start an on-demand scan automatically after virus
signatures are updated to ensure that all files are scanned with the
latest signatures.
3.1. Potential Problems Related to File-Level Scanners
A number of problems may occur when you use file-level scanners with
Exchange Server 2010. For example, a scanner may scan a file when the file
is being used. This can cause the scanner to lock or quarantine the file. In
particular, a file-level scanner could lock an Exchange log or a database
file while Exchange tries to use it, resulting in a severe failure.
You should also be aware that file-level scanners do not provide
protection against some email viruses, such as backdoor Trojan horse
viruses. An example of this is the Storm Worm, which propagated itself
through email messages. The worm joined the infected computer to a network
of similarly compromised machines, known as a botnet,
which could then be remotely controlled by an attacker and used to send spam
email messages in periodic bursts.
When you deploy file-level scanners on Exchange Server 2010 servers, you
can avoid many of the associated problems by ensuring that the appropriate
exclusions, such as directory exclusions, process exclusions, and file name
extension exclusions, are in place for both memory-resident and file-level
scanning.
3.2. Directory Exclusions
You must exclude specific directories on each Exchange Server 2010 server
or server role on which you run a file-level antivirus scanner. On a Mailbox
server, you should exclude the following:
Exchange databases, checkpoint files,
and log files
These are located by default in subfolders of the
%ExchangeInstallPath%\Mailbox folder. You can obtain the
directory location using the EMS. For example, the following
command determines the location of mailbox databases,
transaction logs, and checkpoint files on the Mailbox server
VAN-EX1:
Get-MailboxDatabase -server VAN-EX1 | FL *path*
Figure 6 shows
the output from this command.
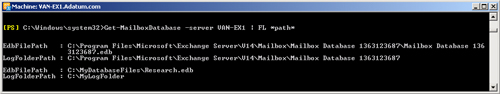
Database content
indexes
These are located by default in the same folder as the
database file.
Group Metrics
files
These are located by default in the
%ExchangeInstallPath%\GroupMetrics folder.
General log files
These include, for example, message tracking and calendar
repair log files. These files are located by default in
subfolders in the %ExchangeInstallPath%\TransportRoles\Logs
folder and %ExchangeInstallPath%\Logging folder. The following
command determines the log paths being used on the Mailbox
server VAN-EX1:
Get-MailboxServer -Identity VAN-EX1 | FL *path*
Figure 7 shows the
output from this command.
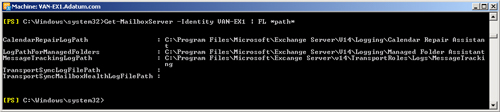
IIS system files
These are located in the %SystemRoot%\System32\Inetsrv
folder.
Offline address book
files
These are located by default in subfolders in the
%ExchangeInstallPath%\ExchangeOAB folder.
Temporary folder used with offline
maintenance utilities such as Eseutil.exe
This is the folder location from which you run the .exe file.
You can configure where you perform the operation when you run
the utility.
The Mailbox database temporary
folder
This is located at
%ExchangeInstallPath%\Mailbox\MDBTEMP.
Exchange-aware antivirus program
folders.
If
the Mailbox server is a member of a database availability group (DAG), you
should also exclude the quorum disk and the %Winnt%\Cluster folder. If the
server is a witness server, you should exclude the witness directory files.
These are located on another server in the environment—typically a Hub
Transport server—by default in
\\%SystemDrive%:\DAGFileShareWitnesses\<DAGFQDN> and default share
(<DAGFQDN>) on that server.
On a Hub Transport server, you should exclude the following:
Pickup and Replay message directory
folders
These folders are located by default in the
%ExchangeInstallPath%\TransportRoles folder. To determine the
paths being used on, for example, the Hub Transport server
DEN-EX1, you run the following command:
Get-TransportServer -Identity DEN-EX1 | FL *dir*path*
General log files
These include, for example, message tracking and connectivity
logs. These files are located by default in subfolders under the
%ExchangeInstallPath%\TransportRoles\Logs folder. The following
command would, for example, determine the log paths being used
on the Transport server DEN-EX2:
Get-TransportServer -Identity DEN-EX2| FL *logpath*,*tracingpath*
The Transport Server role Sender
Reputation database, checkpoint, and log
files
These are located by default in the
%ExchangeInstallPath%\TransportRoles\Data\SenderReputation
folder.
The Transport Server role IP filter
database, checkpoint, and log files
These are located by default in the
%ExchangeInstallPath%\TransportRoles\Data\IpFilter
folder.
The Transport Server role queue
database, checkpoint, and log files
These are located by default in the
%ExchangeInstallPath%\TransportRoles\Data\Queue folder.
The temporary folders used to perform
content and object linking and embedding (OLE)
conversions
By default, content conversions are performed in the Exchange
server’s TMP folder, and OLE conversions are performed in
the %ExchangeInstallPath%\Working\OleConvertor folder.
Exchange-aware antivirus program
folders.
On an Edge Transport server, you should exclude the following:
General log files
These can include, for example, message tracking log files.
These files are located by default in subfolders in the
%ExchangeInstallPath%\TransportRoles\Logs folder. To determine
the log paths being used on the Edge Transport server VAN-EX2,
for example, you run the following EMS command:
Get-TransportServer -Identity VAN-EX2 | FL *logpath*,*tracingpath*
Pickup and Replay message
folders
These are located by default
in the %ExchangeInstallPath%\TransportRoles folder. To determine
the log paths being used on the Edge Transport server VAN-EX2,
for example, you run the following command:
Get-TransportServer -Identity VAN-EX2 | FL *dir*path*
AD LDS database and log
files
These are located by default in the
%ExchangeInstallPath%\TransportRoles\Data\Adam folder.
Transport Server role queue database,
checkpoint, and log files
These are located by default in the
%ExchangeInstallPath%\TransportRoles\Data\Queue folder.
Transport Server role IP filter
database, checkpoint, and log files
These are located by default in the
%ExchangeInstallPath%\TransportRoles\Data\IpFilter
folder.
Transport Server role Sender
Reputation database, checkpoint, and log
files
These are located by default in the
%ExchangeInstallPath%\TransportRoles\Data\SenderReputation
folder.
The temporary folders that are used
to perform content and OLE conversions
By default, content conversions are performed in the Exchange
server’s TMP folder, and OLE conversions are performed in
the %ExchangeInstallPath%\Working\OleConvertor folder.
Exchange-aware antivirus program
folders.
On a Client Access server, you should exclude the following:
The compression folder used with
OWA On servers running IIS 7.0, the compression
folder is located by default at %SystemDrive%\inetpub\temp\IIS
Temporary Compressed Files. On servers running IIS 6.0, the
compression folder is located by default at %systemroot%\IIS
Temporary Compressed Files. IIS system files in the
%SystemRoot%\System32\Inetsrv folder. The Internet-related files stored in
subfolders of the %ExchangeInstallPath%\ClientAccess
folder. Folders on servers that have protocol
logging enabled for POP3 or IMAP4 The POP3 folder
%ExchangeInstallPath%\Logging\POP3 and the IMAP4 folder:
%ExchangeInstallPath%\Logging\IMAP4. The folder
Inetpub\logs\logfiles\w3svc. The temporary folders that are used to
perform content and OLE conversions By default,
content conversions are performed in the Exchange server’s TMP
folder, and OLE conversions are performed in the
%ExchangeInstallPath%\Working\OleConvertor folder.
On a Unified Messaging server, you should exclude the following:
Grammar files for different
locales These could include, for example, en-EN and
es-ES. By default, these files are stored in subfolders of the
%ExchangeInstallPath%\UnifiedMessaging\grammars folder. Voice mail files temporarily stored in the
%ExchangeInstallPath%\UnifiedMessaging\voicemail
folder.
Voice prompts, greetings, and
informational message files
These are stored by default in the subfolders of the
%ExchangeInstallPath%\UnifiedMessaging\Prompts folder.
Temporary files generated by unified
messaging
These are stored by default in the
%ExchangeInstallPath%\UnifiedMessaging\temp folder.
On a server running Microsoft Forefront Protection 2010 for Exchange
Server, you should exclude the following:
The Forefront installation
folder
By default, this is %Program Files%\Microsoft Forefront
Security\Exchange Server.
Quarantined files
These are stored by default in the %Program Files%\Microsoft
Forefront Security\Exchange Server\Data\Quarantine
folder.
Archived messages
These are stored by default in the %Program Files%\Microsoft
Forefront Security\Exchange Server\Data\Archive folder.
Antivirus engine
files
These are stored by default in the subfolders of %Program
Files%\Microsoft Forefront Security\Exchange
Server\Data\Engines\x86 folder.
Configuration
files
These are stored by default in the %Program Files%\Microsoft
Forefront Security\Exchange Server\Data folder.
Note:
The topic of exclusions configured on file-level virus scanning
software inevitably involves lists of exclusions. Treat these lists as a
reference. Read through them a few times but do not attempt to memorize
them. Know that you need to configure directory, file, and process
exclusions.
3.3. Process Exclusions
If a file-level scanner supports the scanning of processes and the
incorrect processes are scanned, this can adversely affect Exchange
operation. You should exclude the following processes from file-level
scanners:
Cdb.exe Cidaemon.exe Cluster.exe Dsamain.exe EdgeCredentialSvc.exe EdgeTransport.exe ExFBA.exe GalGrammarGenerator.exe Inetinfo.exe Mad.exe Microsoft.Exchange.AddressBook.Service.exe Microsoft.Exchange.AntispamUpdateSvc.exe Microsoft.Exchange.ContentFilter.Wrapper.exe Microsoft.Exchange.EdgeSyncSvc.exe Microsoft.Exchange.Imap4.exe Microsoft.Exchange.Imap4service.exe Microsoft.Exchange.Infoworker.Assistants.exe Microsoft.Exchange.Monitoring.exe Microsoft.Exchange.Pop3.exe Microsoft.Exchange.Pop3service.exe Microsoft.Exchange.ProtectedServiceHost.exe Microsoft.Exchange.RPCClientAccess.Service.exe Microsoft.Exchange.Search.Exsearch.exe Microsoft.Exchange.Servicehost.exe MSExchangeASTopologyService.exe MSExchangeFDS.exe MSExchangeMailboxAssistants.exe MSExchangeMailboxReplication.exe MSExchangeMailSubmission.exe MSExchangeRepl.exe MSExchangeTransport.exe MSExchangeTransportLogSearch.exe MSExchangeThrottling.exe Msftefd.exe Msftesql.exe OleConverter.exe Powershell.exe SESWorker.exe SpeechService.exe Store.exe TranscodingService.exe UmService.exe UmWorkerProcess.exe W3wp.exe
If you are deploying Forefront Protection for Exchange Server, you should
also exclude the following processes:
Sometimes directory exclusions fail or files are moved from their default
locations. Therefore, in addition to excluding directories and processes,
you should exclude the following Exchange-specific file name
extensions:
Application-related extensions, for example, .config, .dia, and
.wsb Database-related extensions, for example, .chk, .log, .edb, .jrs,
and .que Offline address book–related extensions (.lzx) Content Index–related extensions, for example, .ci, .wid,
.dir, .000, .001, and .002 Unified Messaging–related extensions, for example, .cfg and
.grxml GroupMetrics extensions, for example, .dsc, .bin, and .xml Forefront Protection 2010 for Exchange Server–related
extensions, for example, .avc, .dt, .lst, .cab, .fdb, .mdb, .cfg,
.fdm, .ppl, .config, .ide, .set, .da1, .key, .v3d, .dat, .klb, .vdb,
.def, .kli, and .vdm
Note that the file name extensions listed for Forefront Protection 2010
for Exchange Server are the signature files from various antivirus directory
engines. Additional file name extensions may be added in the future as
third-party antivirus vendors update their antivirus signature files.
|