Computers running Windows Server 2003 are designed to
receive traffic from other computers over the network. The primary
function of a server is to receive and process requests sent by clients.
However, a computer that is left open to transmissions from other
computers is also a security hazard, particularly if the server is
accessible from the Internet. Unauthorized users might attempt to access
the server for destructive purposes, such as to access confidential
data files, introduce outside software, or simply to prevent others from
using the server. One of the most common techniques firewalls use to
prevent these kinds of intrusions is called packet filtering.
Introducing Packet Filtering
Packet filtering is
a method for regulating the TCP/IP traffic that is permitted to reach a
computer or a network, based on criteria such as IP addresses,
protocols, and port numbers. The system implementing the filter examines
each packet as it arrives and determines whether it meets the criteria
for admission. Packets that do meet the admission criteria are processed
by the system in the normal manner; those that do not are silently
discarded. For example, Internet e-mail servers typically use the Simple
Mail Transfer Protocol (SMTP) and the Post Office Protocol 3 (POP3).
These protocols use the port numbers 25 and 110, respectively. You can
create a packet filter that permits only packets addressed to port
numbers 25 and 110 to reach the server.
|
In the packet header of
each TCP/IP protocol at each layer of the Open Systems Interconnection
(OSI) reference model, identifiers specify which protocol at the next
layer should receive the packet. For example, a data-link layer
protocol, such as Ethernet, has an Ethertype value in its header that
specifies which network-layer protocol should process the packet. In the
same way, at the network layer, the Internet Protocol (IP) has a
Protocol field that specifies the transport-layer protocol that should
receive the packet, and each transport-layer protocol has a Port field
that specifies the application that should be the final recipient of the
data in the packet.
The
values for the TCP/IP port and protocol fields are assigned by an
administrative body called the Internet Assigned Numbers Authority
(IANA). Commonly used server applications have permanent port number
assignments; these are called well-known ports.
Clients often connect to a server using a port number chosen at random
and used only for the duration of the transaction; this is called an ephemeral port. Some of the most commonly used well-known ports are listed in Table 1. (For the complete, updated list, refer to the IANA Port Numbers online database at http://www.iana.org/assignments/port-numbers.)
Table 1. Well-Known Port Numbers| Application | Abbreviation | Protocol | Port Number |
|---|
| File Transfer Protocol (Control) | ftp-control | TCP | 21 | | File Transfer Protocol (Default Data) | ftp-default data | TCP | 20 | | Telnet | telnet | TCP | 23 | | Simple Mail Transfer Protocol | smtp | TCP | 25 | | Domain Name Service | domain | TCP/UDP | 53 | | Dynamic Host Configuration Protocol | dhcps | UDP | 67 | | (Server) | bootps | | | | Bootstrap Protocol Server (nondynamic) | | | | | Dynamic Host Configuration Protocol (Client) | dhcpc | UDP | 68 | | Bootstrap Protocol Client (nondynamic) | bootpc | | | | World Wide Web HTTP | http | TCP | 80 | | Post Office Protocol - Version 3 | pop3 | TCP | 110 | | Simple Network Management Protocol | snmp | UDP | 161 | | Simple Network Management Protocol Trap | snmptrap | UDP | 162 |
|
Packet filtering is
used primarily by routers and firewalls that connect a private network
to the Internet. However, you can use packet filtering inside a private
network as well, to isolate one part of the network from the others. For
example, you might have a separate local area network (LAN) dedicated
to your organization’s accounting department. You want to prevent
unauthorized users on the rest of the network from trying to access
information on the accounting servers, but the user on the accounting
LAN still need to access resources elsewhere on the network. By
installing a firewall between the accounting LAN and the rest of the
network, you can regulate the traffic that is permitted onto the
accounting LAN.
Most
routers have packet filtering capabilities built into them, enabling
you to implement filters at the boundaries between networks. The problem
with integrating packet filters into a router is that the filters can
introduce a large amount of overhead, slowing down the router’s
performance. The router must compare each incoming packet against all
the filters, and then decide whether to admit the packet to the network.
If you have a large, complex system of filters, the amount of time
needed for the router to process each packet can become a major network
performance bottleneck.
Separate firewall products
are also likely to have packet filtering capabilities. Using
firewall-based filters can be advantageous in two ways. First, by
separating the routing and filtering functions on different systems, you
are less likely to experience degraded network performance. Second,
firewalls are likely to have more advanced packet filtering
capabilities, such as preset filter configurations designed to protect
against specific types of attacks.
See Also
The
capabilities of most packet filtering implementations are the same;
what differs is the interface and the configurability of the filters.
Two products might have the same basic filtering capabilities, but one
with preset configurations and detailed documentation will be far easier
to use than one that requires you to understand the ramifications of
the filters you are creating. |
Packet filtering is not a
perfect security solution. It is still possible for intruders to attack
a server using the ports and protocols that the firewall lets through,
or to find a clever new way to bypass the filters you have in place. In
some cases, packet filtering can be an ongoing battle of wits between
the protector and a determined attacker. Every time the attacker finds a
way to penetrate the filters, the system administrator modifies them to
close the opening that is being exploited. Advanced packet filtering
requires a detailed understanding of the TCP/IP protocols and the
applications that use them.
Packet Filtering Criteria
Creating packet
filters is a matter of selecting the specific criteria you want the
system to examine and specifying the values that you want to allow or
deny passage. Packet filters can be inclusive or exclusive. This means
that you can start with a network connection that is completely blocked
and use filters to specify what traffic can pass through, or you can
start with a completely open connection and specify the types of traffic
you want to block. The former is inherently more secure, but can be
more difficult to debug, because you must make sure that all the traffic
that needs to pass through the filters is getting through.
Note
Packet
filtering can also work in either direction. You can use filters to
prevent users on the Internet from accessing your private network, or
you can use them to limit the Internet access granted to your internal
users. |
The criteria most commonly used in packet filtering are as follows:
Port numbers Filtering by port numbers, also know as service-dependent filtering,
is the most common type of packet filtering, and the most flexible.
Because port numbers represent specific applications, you can use them
to prevent traffic generated by other applications from reaching a
network. For example, to protect a perimeter network containing your
company’s Web servers, you can create filters that allow only traffic
using port 80 to enter from the Internet. Port 80 is the well-known port
assigned to World Wide Web HTTP, the main application layer protocol
used by Web servers.
Protocol identifiers
The Protocol field in every packet’s IP header contains a code that
identifies the protocol that should receive the packet next. In most
cases, the code represents a transport layer protocol, such as
Transmission Control Protocol (TCP) or User Datagram Protocol (UDP).
However, IP datagrams frequently carry Internet Control Message Protocol
(ICMP) messages as well. ICMP is another network layer protocol, but IP
frequently uses it to transmit error messages and diagnostic packets,
such as the Echo Request messages used by the Ping utility. Filtering
using protocol identifiers is not very precise, because it blocks or
allows all the traffic that uses a particular protocol. However, for
certain applications, blocking an entire protocol is warranted, and is
easier than anticipating the specific applications an attacker might
use. For example, you might use protocol filters on a network that
contains only Internet Web and FTP servers to limit incoming traffic to
TCP packets. Because these servers rely on TCP for their primary
functions, you can usually block all UDP and ICMP traffic, preventing
attackers from using any application that relies on these protocols to
attack your servers.
IP addresses
IP address filtering enables you to limit network access to specific
computers. For example, if you have an Internet Web server on a LAN with
other computers, and you want Internet clients to be able to access
only the Web server, you can create a filter permitting only packets
addressed to the Web server to enter the network from the Internet. IP
address filtering is also useful for protecting part of a private
network from users on the other parts. You can create filters that give
only certain computers access to the protected LAN, while preventing all
others from accessing it.
Security Alert
Filtering
using IP addresses is not particularly secure if potential attackers
have any way to discover the IP addresses of the computers on your
network. Once an attacker finds out the IP addresses that the filter
allows access to the network, it is simple to impersonate another
computer by using its IP address (which is called spoofing). |
Hardware addresses Hardware
addresses (also called media access control or MAC addresses) are coded
into network interface adapters at the factory. Filtering based on
hardware addresses provides the same basic functionality as IP address
filtering. However, it is much more difficult to spoof a hardware
address than an IP address, so using hardware addresses is inherently
more secure than using IP addresses. Hardware address filtering is
rarely used on Internet routers or fire-walls, primarily because
computers outside the private network have no way to discover the
hardware addresses of the computers on the inside. For internal
filtering, however, hardware addresses are a useful means of restricting
access to specific resources.
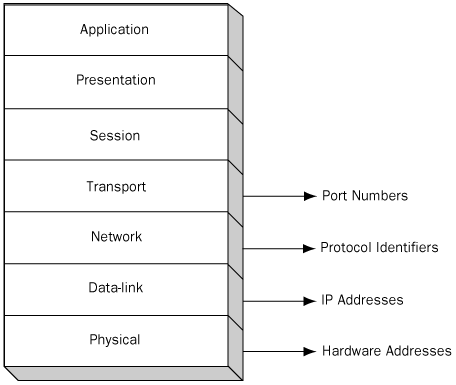
The four criteria
listed here correspond to the transport, network, data-link, and
physical layers of the OSI reference model, as shown in Figure 1.
Filters get more specific as you move up the OSI model. Filtering by
port numbers enables you to specify which applications you want to
permit through the filter, while filtering by IP addresses and hardware
addresses enables you to block access by entire computers.
The real strength of
packet filtering as a security mechanism comes when you combine
different types of filters to create a composite solution. For example,
you might want to open up the Telnet port (port 23) so that
administrators can remotely manage the company Web servers from home,
using the Internet. However, leaving this port open is an invitation for
unauthorized Internet users to access your servers for their own
illicit reasons. By adding a filter that limits port 23 access to only
your administrators’ IP addresses, you add a measure of protection to
the network.
Windows Server 2003 Packet Filtering
Windows
Server 2003 contains two packet filtering implementations, one of which
is integrated into the TCP/IP client itself, and the other into the
Routing and Remote Access service (RRAS). You can use either or both to
filter specific types of traffic entering the computer.
Using TCP/IP Packet Filtering
The TCP/IP client in
all the current versions of the Microsoft Windows operating system
(including Windows Server 2003, Microsoft Windows XP, and Microsoft
Windows 2000) includes a rudimentary packet filtering capability that
you can use to specify what types of traffic are permitted to reach the
TCP/IP protocol stack on the computer. This packet filtering
implementation is relatively limited. You cannot filter out ICMP traffic
and you cannot create exclusive filters. Exclusive filters enable you
to specify the ports and protocols that you want to prevent from
entering the system. TCP/IP client packet filtering is only inclusive:
it can only specify the ports and protocols you want to allow in.
To configure the packet filtering capabilities of the TCP/IP client, use the following procedure:
1. | From the Control Panel, display the Network Connections window.
|
2. | Select one of the connections in the window, and display its Properties dialog box.
Each network interface has its own independent packet filtering
implementation. You can create separate filters for each interface,
providing different degrees of access to each network connection.
|
3. | Display the Internet Protocol (TCP/IP) Properties dialog box for the connection.
|
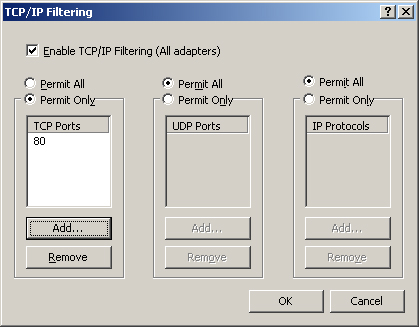
4. | Click Advanced, click the Options tab, and then click Properties. The TCP/IP Filtering dialog box appears, as shown in Figure 2.
|
In
this dialog box, you can specify the TCP ports, UDP ports, and IP
protocols that packets must use if they are to access the TCP/IP stack.
In each case, you must use the standard code numbers to reference the
ports and protocols. The port numbers are listed in Table 1, and the protocol codes are listed in Table 2. (For the complete, updated list, refer to the IANA Protocol Numbers online database at http://www.iana.org/assignments/protocol-numbers.)
Table 2. Protocol Codes
| Protocol | Protocol Code |
|---|
| Internet Protocol (IP) | 0 |
| Internet Control Message Protocol (ICMP) | 1 |
| Transmission Control Protocol (TCP) | 6 |
| User Datagram Protocol (UDP) | 17 |
Note
Although the codes for the IP and ICMP protocols are listed in Table 12-2,
and you can specify them in the TCP/IP Filtering dialog box, they are
both useless under normal conditions. The TCP/IP client cannot filter
ICMP traffic, so specifying code 1 in the dialog box has no effect.
Specifying code 0 indicates that you are permitting IP datagrams to
contain other IP datagrams, which under normal conditions is not
possible. |
Using Routing and Remote Access Service Packet Filtering
Windows Server
2003 RRAS includes a packet filtering mechanism that is more capable
than that of the TCP/IP client, but you can only use it when you have
configured Windows Server 2003 to function as a router. As with the
TCP/IP client packet filtering mechanism, you can create different
filters for each network interface on the computer. However, in RRAS
packet filtering, there are a number of capabilities that TCP/IP client
filtering does not have, such as the following:
Creating filters based on the IP addresses, protocols, and port numbers of a packet’s source or destination
Creating inclusive or exclusive filters
Creating filters for ICMP messages, specified by the message type and code values
Creating multiple filters of the same type