Creating a Network Policy for Noncompliant Clients
After a network policy has
been made for compliant clients, an equivalent policy needs to be
created for noncompliant clients. The process is similar, with a few
changes as follows:
1. | From the Network Policy MMC tool, navigate to Policies, Network Policies from the node pane.
|
2. | Right-click the Network Policies node, and choose New.
|
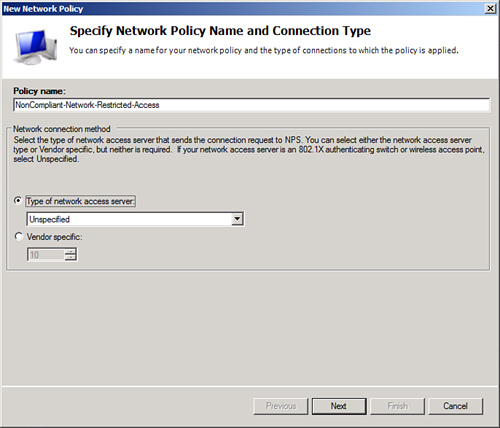
3. | On the Specify Network Policy Name and Connection Type page, shown in Figure 6, enter a descriptive policy name, such as NonCompliant-Network-Restricted-Access, and click Next (leave the type of server as Unspecified).
|
4. | On the Specify Conditions page, click the Add button.
|
5. | Select Health Policies from the list, and click the Add button.
|
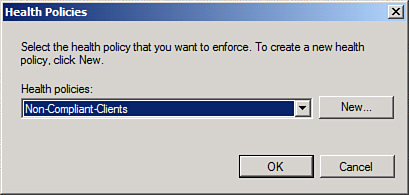
6. | From the list of health policies, choose the NonCompliant-Clients policy previously created, as shown in Figure 7, and click OK.
|
7. | Click Next to continue.
|
8. | On the Specify Access Permission page, shown in Figure 8, select the Access Granted option button, and click Next to continue.
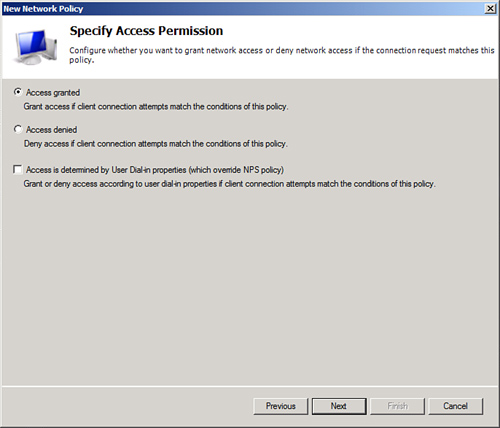
Note
It
might seem counterintuitive to select the Access Granted option button
for a noncompliant network policy. It’s important to note, however, that
this simply means that the access is granted to the policy itself, not
to the network. If the Access Granted option is not selected, the policy
will not work.
|
9. | On
the Configure Authentication Methods page, select only the Perform
Machine Health Check Only check box and deselect any other ones. Click
Next to continue.
|
10. | On the Configure Constraints page, leave the defaults in place, and click Next.
|
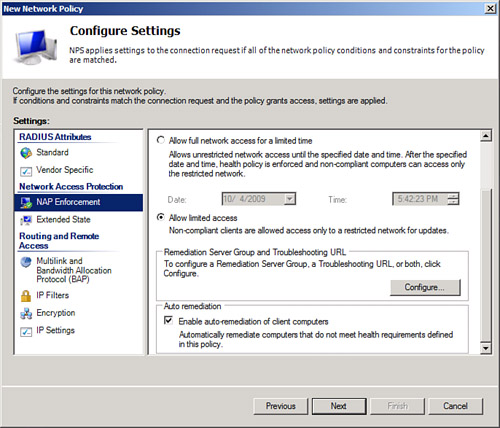
11. | On the Configure Settings page, select NAP Enforcement and select the Allow Limited Access option button, as shown in Figure 9.
If auto remediation will be enabled (allowing the server to access
other servers such as WSUS or DNS), then check the Enable
Auto-remediation of Client Computers check box. Click Next to continue.
|
12. | Click Finish to complete the wizard.
|
After all five steps have
been performed on the NPS system, the individual services can be
integrated with the NPS system to restrict clients based on the health
and network policies that were created. This includes the DHCP Server
role and the services that control 802.1X and RRAS for VPN. In this
example, we will configure the DHCP role to block clients based on the
SHV that we created in the earlier steps.
Configuring a DHCP Server to Restrict Client Leases Based on the NPS Policy
After the NPS policies
have been created, the DHCP server and DHCP scope used can be configured
to use NAP settings to validate the client health before granting IP
addresses. In the example we’ve been using so far, this would restrict
only those clients with a valid and up-to-date antivirus application
from getting a DHCP address.
To configure the DHCP scope for NPS, do the following:
1. | On the DHCP server, open the DHCP MMC tool (Start, All Programs, Administrative Tools, DHCP).
|
2. | Navigate to SERVERNAME, IPv4, Scope Name.
|
3. | Right-click Scope Name, and choose Properties.
|
4. | Select the Network Access Protection tab, and click the Enable for This Scope option button, as shown in Figure 10. Click OK to save the changes.
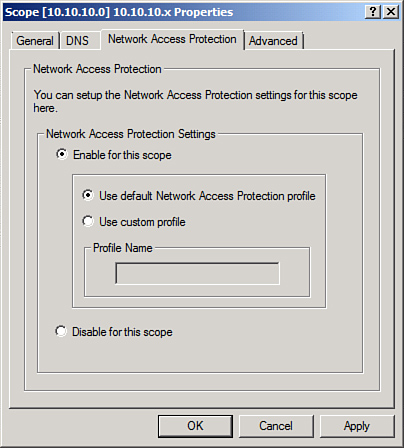
|
After enabling NAP on a
Scope, individual scope options can be configured for noncompliant
clients. These scope options appear under the User Class named Default
Network Access Protection Class, as shown in Figure 11.
By not configuring any scope options, the clients effectively have no
DHCP access to resources. Or, in a different example, you could
configure the clients to use an alternate DNS server for remediation.
Scope options can be configured by right-clicking on the Scope Options
node under the Scope Name and choosing Configure Options. Click the
Advanced tab to view the classes and options.
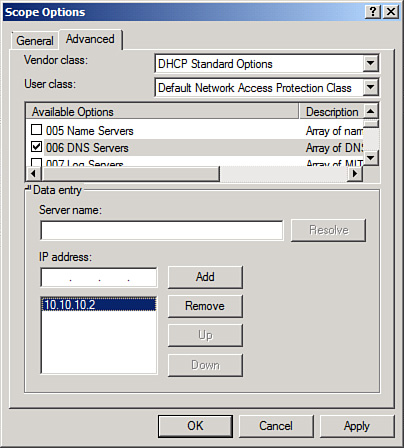
Note
The default User Class is used
for compliant NAP clients—the Default Network Access Protection Class
is used for noncompliant clients.