1. Forest Trusts
With the release of
Windows Server 2003, Microsoft made a previously unavailable function
available to administrators. Forest trusts allow an administrator to
connect two forests and establish a trust between them at the forest
level. This is a big change from the previous iteration, which allowed
this only on the domain level. Forest trusts can be either one-way,
two-way, or transitive. In a two-way transitive forest, each forest
trusts the other completely. Forest trusts offer several benefits, such
as simplified resource access, improved authentication, improved
security, and improved administrative overhead.
It's important to note that,
unlike domain trusts (discussed next), forest trusts can be created only
between two forests. They cannot be extended or joined to a third. This
function is slightly limiting; however, this is utilized for security
purposes and for administrative reasons. By accident, an administrator
could easily end up making all components of a multitiered forest trust
each other completely!
2. Domain Trusts
Just like at the forest level,
administrators have the ability to create trusts between domains,
albeit with a lot more flexibility and power than at the forest level.
In Windows Server 2008,
three different trust types are available between domains in order to
aid in the sharing of resources: realm trusts, external trusts, and
shortcut trusts. Each of these types of trusts has various optional
permissions and allowances. You will need to be familiar with them
before you begin planning your infrastructure design.
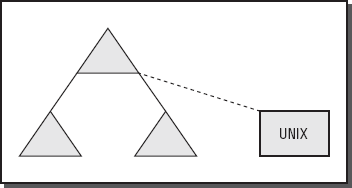
External trusts
You can create an external trust
to form a one-way or two-way, nontransitive trust with domains outside
of your forest. External trusts are sometimes necessary when users need
access to resources located in a Windows NT 4.0 domain that doesn't
support Active Directory. Figure 1 illustrates this.
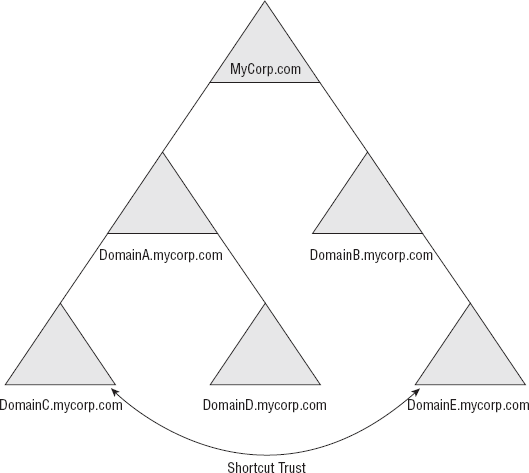
Shortcut trusts
Sometimes when you
have a complex Active Directory forest, the "shortest path" between two
servers is not as idyllic as you might desire. If, for instance, a
particular domain is nested four tiers down in your tree and it wants to
access resources in another domain that is four tiers down in another
tree, it will have to go up four levels and then down four levels of
authentication in order to access the resources it requires.
This is quite inefficient.
There is another option. By using Kerberos, you can create a transitive
trust between the two domains that allows one domain to directly access
another, without having to traverse up and down their various trees.
This is a shortcut trust.
It's quite a useful trick, and it can save a lot of time. Keep in mind
that once you create a shortcut trust, Windows Server 2008 will default
to the shortest path it can to reach the desired server. This means
there may come an occasion where a shortcut trust exists between a
server and another server somewhere else in the network infrastructure.
Undesired performance compromises can result if the server authenticates
through its shortcut and then through another machine's trust. Because
of this, it's best to use shortcut trusts in moderation. However, you
can see a figurative example of a shortcut trust in Figure 2.
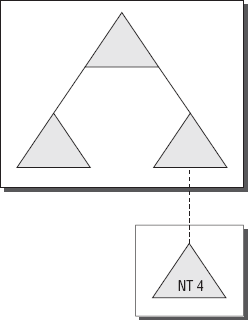
Realm trusts
Since the whole world
doesn't use Windows servers, it's a pretty good thing that Windows
Server 2008 has a way to accommodate this. That way is a realm trust.
Realm trusts are designed to give Unix users the ability to
authenticate and have a relationship with a Windows server. This means
the users on another operating system can have access to your files and
resources. However, Unix realm trusts are one-way trusts and are not
transitive, as illustrated in Figure 3.