A file system
is by definition a hierarchical structure of folders that house files
and secure those files through a series of access control lists (ACLs)
and access control entries (ACEs) that define the type of permissions
that are granted or denied to those same folders and files. This means
that in the Windows Server 2008 R2 world, the primary methodology for
securing folders and their files is the use of permissions.
Permissions come in two
varieties: share-level permissions and NTFS permissions. If you think
about it, this makes perfect sense. When you create a folder in the file
system, there is a default set of permissions that are assigned to the
folder. The system itself, the user who created the folder, and the
local Administrators group on the server where the folder was created
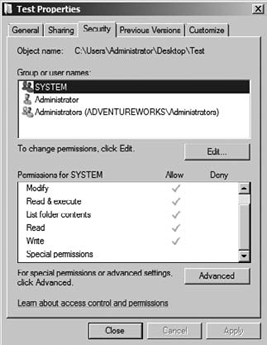
all need some level of access to the folder, as shown in Figure 1.
NTFS permissions are assigned
when the folder is created but can be edited at any time by a user or
group member who has the permission to change permissions on the folder.
NTFS folder permissions come in two types called standard permissions and special permissions.
Standard permissions come in the form of Full Control, Modify, Read
& Execute, List Folder Contents, Read, and Write. Each of these
permissions can be either allowed or denied. Because you have the option
to allow or deny permissions on a folder in an NTFS file system, you
have incredible flexibility over the level of access on a given folder.
In addition to the standard
permissions, there are also special permissions that can be set on each
folder or file. Special permissions do more than simply provide access
to the folder on which they are applied. They provide the basis for
folder ownership as well as the ability to change permissions for a
folder and the hierarchy that could exist beneath the folder in the file
system.
1. Set Standard NTFS Permissions
Setting or changing standard NTFS permissions is a straightforward process. Follow these steps to get started:
Locate the desired folder.
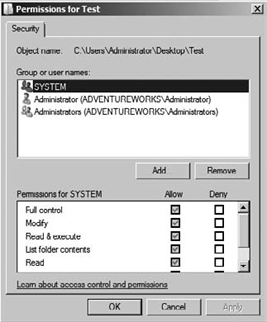
At this point, you can select
an existing user or group from the list of users and groups that have
existing permissions, or you can click the Add button to add new users
or groups to which permissions may be assigned.
You can add users and groups
from the local accounts available on the physical machine or from the
Active Directory database if the folder resides on a server that is part
of an Active Directory forest. In the event that you are interested in
removing permissions, you can simply select the user or group account
from the list of users and groups and then click the Remove button, as
illustrated in Figure 2.
Please keep in mind that not
just anyone can add, change, or remove NTFS permissions on a folder. You
need to have permissions to a folder in order to change its
permissions. The permissions to change permissions or take ownership of a
folder are special permissions.
2. Set Special NTFS Permissions
Like with standard
permissions, adding or changing special permissions is a fairly
straightforward process. Follow these steps to get started:
Locate the desired folder.
Click the Advanced button.
At this point, the Advanced Security Settings dialog box for this folder is displayed, as shown in Figure 3.
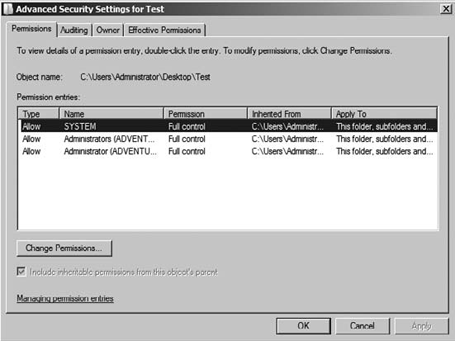
On the Permissions tab, you can
click Change Permissions and add, edit, or remove the special
permissions. Note the check boxes at the bottom of the window to include
inheritable permissions from this object's parent and to replace all
child object permissions with inheritable permissions from this object.
NTFS file systems have a system of inheritance that is built in to the
file system. This means that permissions added higher up in the file
system hierarchy can flow down to the folders that are beneath them in
the hierarchy. This is valuable when you want to assign permissions to
users or groups to a section of the NTFS file system. It can also
present some interesting challenges when you are trying to figure out
exactly what permissions a given user or group has been granted on a
given folder. To help with this issue, you can use the Effective
Permissions tab in the Advanced Security Settings dialog box as shown in
Figure 4.
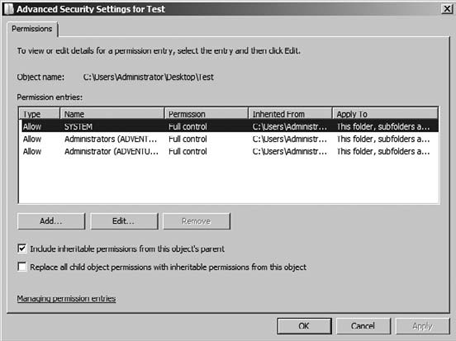
3. View Effective NTFS Permissions
To view the effective NTFS permissions, follow these steps:
Locate the desired folder.
Click the Advanced button.
Select the Effective Permissions tab.
Select the user or group whose effective permissions you want to view.
Click OK to view them, as shown in Figure 5.
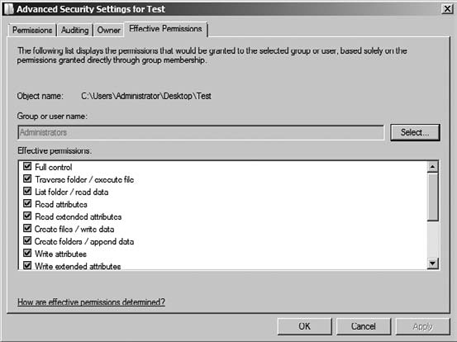
Notice in Figure 5
that on the Effective Permissions tab you can view both standard and
special permissions for the user or group that you select. This can be a
very valuable tool to aid you in determining the permissions on an NTFS
folder.
4. Take Ownership of an NTFS Folder
By now you may have noticed that
a set of default permissions is given to each folder created in an NTFS
file system. There is a special set of permissions given to the creator
of an NTFS folder. These permissions can be defined as "ownership" of
the folder. The owner of the folder has full control of the folder and
both its standard and special permissions. The Administrators group is
also given special permissions, including the permission to take
ownership of the folder. This means that at any given point in time
anyone in the Administrators group might choose to take ownership of an
NTFS folder and thus take control of its associated permissions. In
order to take ownership of a folder, though, you need to have that
special permission assigned to your user or group. If you do not have
permissions to take ownership of a folder, you cannot simply "force"
your way to ownership. By the same token, if you are the owner, you can
deny the ability to take ownership to all parties with the exception of
yourself. Now that's control!
If you have the permission to take ownership, the process works like this:
Locate the desired folder.
Click the Advanced button.
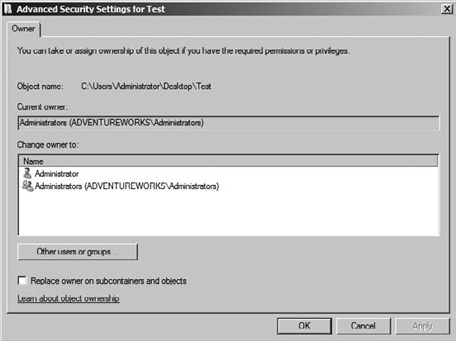
Notice that when you click
Edit, the current owner is displayed, and the users or groups that can
take ownership are displayed in the Change Owner To box. It is also
important to consider the Replace Owner On Subcontainers And Objects
check box. If you take ownership of a folder, you also have the option
to take ownership of the folders beneath it in the hierarchy. This may
be desirable if your intent is to take control of a section of the file
system.
NTFS folder and file
permissions are a great way to control permissions to a local resource.
The problem you will have is that in a network environment the users are
almost never sitting at the server where the resources are located. How
do you provide access and permission controls for folders that are not
on the same physical system that the user is on? You share them!