GPO Filtering
Applying GPOs can be tricky
and the design of the Active Directory forest, domains, sites, and OU
hierarchy play a major part in this. One of the most important
considerations when designing the Active Directory OU hierarchy within a
domain is to understand how the domain administrators plan to manage
the domain computers and users with group policies.
In many cases, even with
the most careful planning of the Active Directory infrastructure, GPOs
will be applied to computers and/or users that do not necessarily need
the settings contained within that GPO. To better target which computer
and user objects a particular GPO applies to, Microsoft has built in a
few different mechanisms to help filter out or include only the
necessary objects to ensure that only the desired computers or users
actually apply the policy. The mechanisms that control or filter how a
policy will be applied are as follows:
GPO Security Filtering
GPO security filtering is the
“group” in Group Policy. Many administrators can get frustrated when
having to explain the fact that Group Policy applies to computers and
users but not to groups. In fact, the GPO security filtering is where
administrators can define which users, computers, or members of security
groups will actually apply the group policy.
By default, GPOs apply to the
Authenticated Users security group, which includes all users and
computers in the domain. The scope of GPO application is then segmented
based on the location of the
Group Policy links. It can be segmented even further by removing the
Authenticated Users group from the GPO security filtering, as shown in Figure 5, and replacing it with a custom security group.
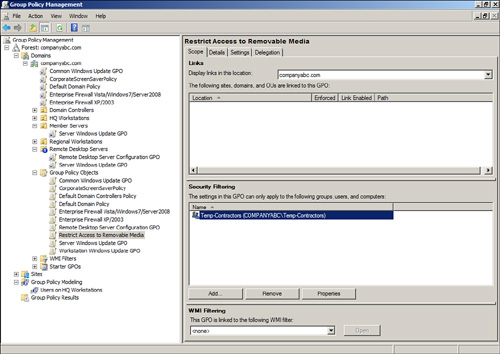
When the security
filtering of a GPO is configured to apply to a custom security group,
only the members of that group, whether users, other groups, or computer
objects, will actually apply that particular policy. Last but not
least, it is most important to always keep the group membership current;
otherwise, the application of Group Policy might be incomplete or
incorrect.
GPO WMI Filtering
GPO WMI filtering is a
Group Policy concept introduced in Windows XP and Windows Server 2003. A
WMI filter is a query that is processed by computer objects only and
can be used to include or exclude particular computer objects from
applying a GPO that includes the WMI filter. An example of a WMI filter
could be a query that includes only computer objects with an operating
system version of “6.1*,” which includes all Windows 7 and Windows
Server 2008 R2 systems. Of course, it is important to state that WMI
filters will not be processed by legacy Windows 2000 or older systems.
The security filtering must also meet the criteria for the GPO to be
processed. WMI filters work great when the Active Directory hierarchy
is relatively flat, but maintaining computer group membership can be
tedious.
GPO Status
GPOs are applied to computer and user objects. Within a
particular GPO, the settings available are segmented into two distinct
nodes, including the Computer Configuration node and the User
Configuration node.
Configuring or changing the GPO status, shown in Figure 6,
enables administrators to change the GPO as follows:
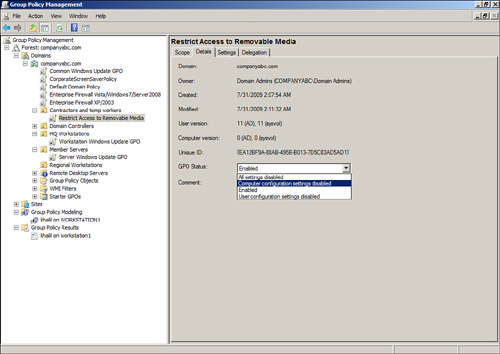
This function of a GPO can be a
very effective tool in troubleshooting GPOs as well as optimizing GPO
processing. As an example, if a GPO only contains configured settings in
the Computer Configuration node, if any user objects are located in
containers linked to that particular GPO, the GPO will still be
processed by the user to check for any configured settings. This simple
check can add a few seconds to the entire GPO processing time for that
user, and if many GPOs are processed, it could increase the logon,
logoff, or refresh interval by minutes or more. As a troubleshooting
tool, if a user or computer is not receiving the
desired end result of a set of applied policies, disabling a node or the
entire policy can aid an administrator in identifying the suspect GPO
causing the undesired result.