When working with Group Policy, which has several
moving parts, learning some tools to troubleshoot the application of
group policies will help save you administrative time and hassle.
The built-in tools focus
on predicting how your policy settings will be applied and how to find
out the results on how the policy was applied. The tools are the Group
Policy Modeling Wizard (GPMW) and three tools for generating the RSOP:
the Group Policy Results Wizard (GPRW), GPResult.exe,
and the RSOP snap-in. Ultimately, these tools will allow you to see the
Group Policy order of precedence in action. You can see which policies
were applied to the system and which polices "win."
In addition, since Group Policy relies on the network, all the tools you use to test the network—from ping
to name resolution—still apply when troubleshooting Group Policy. For
example, you can run the RSOP tool, which will inform you if a policy
was not applied. If you check your GPO and it is all correct, this will
generally indicate it's a network or replication issue.
1. Use the Group Policy Modeling Wizard
The GPMW allows you to preview
your group policies. The tool models the results of group policies
before they are deployed. This tool compiles reports based on what is
configured at the site, domain, and OU levels for both computer and user
objects. Based on the rules for applying group policies, the tool will
give you a snapshot at what policies will be applied. GPMW can also show
you how any security or WMI filtering will affect the application of
group policies.
The GPMW is located in the
GPMC, and you can find it in the Sites container. It is important to
note that the GPMW evaluates only the theoretical RSOP based on all GPOs
and filtering set via AD. It does not take into account any physical
issues on the network that may affect GPO application.
To create a model, perform the following:
In the GPMC right-click Group Policy Modeling, and select Group Policy Modeling Wizard.
On the welcome page, click Next.
Select the domain controller you will use to process the requests for modeling, and click Next.
Determine
what you want to model. You can choose an individual user, individual
computer, or a whole scope (domain or OU) for either a user or a
computer. You can also model a combination of any of these. For example,
you could model just one user for user settings and an entire domain
for computer objects. After you have selected your target, click Next.
You
also have the ability to simulate a slow network or a loopback address
in the Advanced Simulation dialog box, make your selection, and click
Next.
In
the Alternate Active Directory Paths dialog box, you have the ability
to choose other locations for the simulation. (You may not see this
dialog box option, based on what choices you made in step 3.) Make your
selection, and click Next.
You can also simulate changes to a user's security group. After you make your selection, click Next.
Like with users, you can also simulate changes to a computer's security groups. After you make your selection, click Next.
The WMI Filters For Users setting allows you to control which filters are used. After you make your selection, click Next.
The
WMI Filters For Computers setting allows you to control which filters
are used for your computer accounts. After you make your selection,
click Next.
On the summary screen, review your selections, and click Next to create the model.
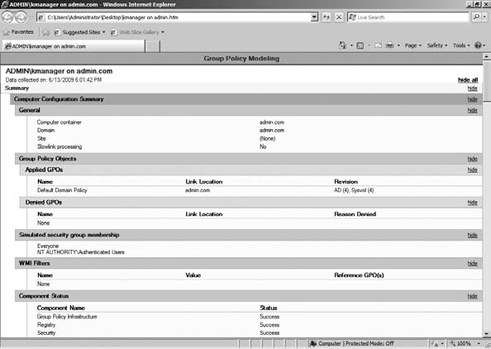
When
the model is done being created, click Finish to see the report. The
report is saved under the Group Policy Modeling node. You can rerun the
model at any time by right-clicking the model and selecting Re-run. Figure 1 shows an example of the report.
2. Use Tools to See the RSOP
Several tools will allow you
to see the RSOP. One of the tools is built into the GPMC. The Group
Policy Results Wizard is similar to the GPMW, and it is also located in
the GPMC. To run the GPRW, go the Sites container, and perform the
following steps:
Right-click Group Policy Results, and select Group Policy Results Wizard.
On the welcome page, click Next.
You can select the local computer or a remote computer. Make your selection, and click Next.
Select
the user account you want to see the RSOP for, and click Next. It is
important to note that you will see only users who have already logged
onto the system.
Review the summary screen, and click Next.
After the wizard runs successfully, click Finish to return to the GPMC and view the report.
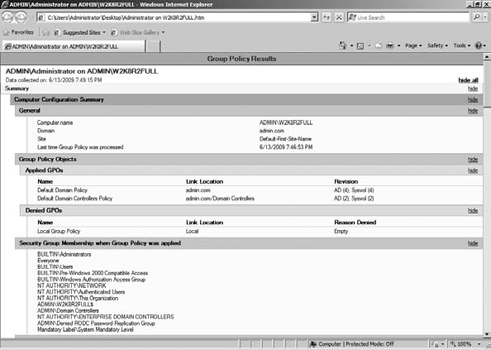
The
report is saved under the Group Policy Modeling node. You can rerun the
model at any time by right-clicking the report and selecting Re-run
Query. Figure 2 shows an example of the report.
The second tool is a command-line tool called GPResult.exe.
This tool will allow you to see the results of Group Policy either for
the local system and current user or for remote systems and other users.
Like many other commands, several switches/parameters are available
providing additional information. You can pipe the results to a text
file and utilize the command in batch files or scripts.
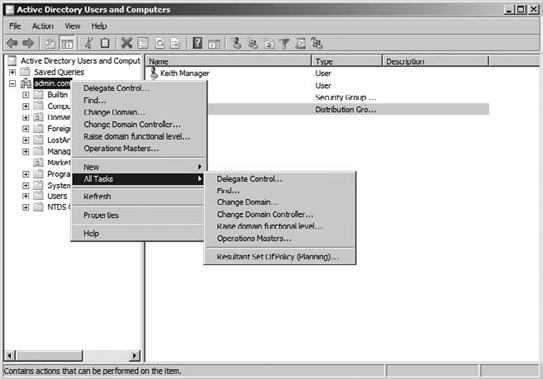
Lastly, the Resultant Set
of Policy snap-in is available by loading the Microsoft Management
Console (MMC) and adding it. You can also find the tool in the Active
Directory Users And Computers tool, as shown in Figure 3.
This tool is similar to the
GPRW, but it is able to display the results of multiple GPOs. This is a
great tool to troubleshoot your GPOs if the GPMC is not currently
available. The tool also has two modes: planning mode and logging mode.
The main difference between
the modes is how you are provided the RSOP. Planning mode, which is
similar to the GPMW, simulates the processing of Group Policy. Logging
mode queries a specific computer's WMI database, which is collected when
Group Policy is applied. You can view user information with this tool
only if the user has logged onto the system. Additionally, you will see
only those policies that have been processed by the system.
Both modes have benefits.
The main benefit of planning mode is that it generates a report based on
what settings will be processed before they are processed. Planning
mode allows you to simulate behaviors and troubleshoot your group
policies before you apply them into production. The main benefit of
logging mode is accuracy since the report is based on what has actually
been processed.
NOTE
When you are working
with Group Policy, one of the popular debates is how many settings to
make per GPO. Do you create one GPO with all of your desired settings,
or do you create more GPOs with a few settings? Well, the answer to the
question is one of the favorites in all of IT administration: it
depends.
Seriously, you do not want to
create one GPO for every individual setting or create one massive GPO
with all the settings. The answer lies in balance, performance, how
often you make changes, and how you delegate administration.
Generally speaking, if your
group policies do not change, you can consolidate your policies into
fewer GPOs, which will increase client processing time. However, this
method sometimes can be hard to track changes and troubleshoot. Another
method is to create GPOs based on the settings they are processing and
segment if they are computer-based or user-based settings. For example,
create a GPO for just the security settings of a computer, and create
another for the security settings for the users. Although this method
will cause more client-side processing, it does help mitigate frequent
changes to your group policies.