Authorization Manager
Authorization Manager (AzMan.msc) is now included with Windows Vista. Windows Authorization Manager (AzMan)
is an application Role-Based Access Control (RBAC) framework for
applications that integrate the AzMan framework. AzMan provides a
Role-based MMC user interface and development interfaces. AzMan has the
following benefits for application administrators and developers:
Common RBAC Administration
An easy-to-use, common, role-based administrative experience;
administrators learn fewer authorization models and require less
training.
Natural Role-based Development Model Easy to integrate with native or managed applications; provides broad RBAC management and enforcement functionality.
Flexible Authorization Rules Offers the ability to define membership through dynamic Lightweight Directory Access Protocol (LDAP) queries or custom rules.
Centralized Administration Multiple applications can be managed centrally and leverage common application groups.
Flexible Storage Options Policy can be stored in Active Directory, XML files, or SQL Server.
Platform Integration and Alignment
Offers support for platform features such as Active Directory groups
and attributes and Windows security auditing, as well as assurance of
proper integration of system access control objects such as the NT
access token and better alignment for future Windows access control
features and products.
Reduced Software Development and Maintenance Costs
Developers avoid the expense or tradeoffs of custom access control.
AzMan does the expensive work of a full-featured authorization solution,
including a complete RBAC model, policy storage (within Active
Directory, SQL, or XML), an MMC user interface, built-in application
group support, rule and query support, integrated system auditing, and
performance optimizations.
Enhanced Security
Platform technologies are rigorously tested, broadly used, and
continually refined. A common RBAC model leverages administrators’
existing knowledge, resulting in fewer access control mistakes.
Previously,
developers had to create a custom user interface for enabling
administrators to control security features of an application.
Alternatively, organizations had to rely on developers to make changes
to the code to enforce authorization restrictions. AzMan provides
abstractions that allow developers to integrate low-level application
operations and preserve the ability of application administrators to
define roles and tasks without requiring code changes.
Authorization
Manager is also included with Windows Server 2003 and can be installed
on Windows XP computers. For more information about Authorization
Manager, refer to the Windows Server 2003 Help and Support.
Network Access Protection Client
Most
networks have perimeter firewalls to help protect the internal network
from worms, viruses, and other attackers. However, attackers can
penetrate your network through remote access connections (such as a VPN)
or by infecting a mobile PC, and then spreading to other internal
computers after the mobile PC connects to your local area network (LAN).
Windows Vista, when connecting to a Windows Server Code-Name “Longhorn” infrastructure, supports Network Access Protection (NAP)
to reduce the risk of attackers entering through remote access and LAN
connections using Windows Vista’s built-in NAP client software. If a
Windows Vista computer lacks current security updates, virus signatures,
or otherwise fails to meet your requirements for a healthy computer,
NAP can block the computer from reaching your internal network.
However, if a computer
fails to meet the requirements to join your network, the user doesn’t
have to be left frustrated. Client computers can be directed to an
isolated quarantine network to download updates, antivirus signatures,
or configuration settings required to comply with your health
requirements policy. Within minutes, a potentially vulnerable computer
can be protected and once again allowed to connect to your network.
NAP is an
extensible platform that provides an infrastructure and API for
health-policy enforcement. Independent hardware and software vendors can
plug their security solutions into NAP so that IT administrators can
choose the security solutions that meet their unique needs. NAP helps to
ensure that every machine on the network makes full use of those custom
solutions.
Microsoft will also release NAP client support for Windows XP SP2. For more information about Network Access Protection, see http://www.microsoft.com/technet/itsolutions/network/nap/default.mspx.
Web Services for Management
Web Services for
Management (WS-Management) makes Windows Vista easier to manage
remotely. An industry-standard web services protocol for protected
remote management of hardware and software components,
WS-Management—along with the proper software tools—allows administrators
to remotely run scripts and perform other management tasks. In Windows
Vista, communications can be both encrypted and authenticated, limiting
security risks. Microsoft management tools such as Systems Management Server (SMS) 2003 use WS-Management to provide safe and secure management of both hardware and software.
Crypto Next Generation (CNG) Services
Cryptography
is a critical component of Windows authentication and authorization
services, which use cryptography for encryption, hashing, and digital
signatures. Windows Vista delivers Crypto Next Generation (CNG) services, which was requested by many governments and organizations.
CNG allows new algorithms to be added to Windows for use in Secure
Sockets Layer/Transport Layer Security (SSL/TLS) and Internet Protocol
security (IPsec). Windows Vista also includes a new security processor
to enable trust decisions for services such as rights management.
For
organizations that are required to use specific cryptography algorithms
and approved libraries, CNG is an absolute requirement.
Data Execution Prevention (DEP)
One of the most commonly used techniques for exploiting vulnerabilities in software is the buffer overflow
attack. A buffer overflow occurs when an application attempts to store
too much data in a buffer, and memory not allocated to the buffer is
overwritten. An attacker might be able to intentionally induce a buffer
overflow by entering more data than the application expects. A
particularly crafty attacker can even enter data that instructs the
operating system to run the attacker’s malicious code with the
application’s privileges.
Perhaps the most
well-known buffer overflow exploit in recent years is the CodeRed worm,
which exploited a vulnerability in an Index Server Internet Server
Application Programming Interface (ISAPI) application shipped as part of
an earlier version of Microsoft Internet Information Server (IIS) to
run malicious software. The impact of the CodeRed worm was tremendous,
and could have been prevented by the presence of Data Execution
Prevention (DEP).
DEP marks sections of
memory as containing either data or application code. The operating
system will not run code contained in memory marked for data. User
input—and data received across a network—should always be stored as
data, and would therefore not be eligible to run as an application.
32-bit versions of
Windows Vista include a software implementation of DEP that can prevent
memory not marked for execution from running. 64-bit versions of Windows
Vista work with the 64-bit processor’s built-in DEP capabilities to
enforce this security at the hardware layer, where it would be very
difficult for an attacker to circumvent.
Note
DEP
provides an important layer of security for protection from malicious
software. However, it must be used alongside other technologies, such as
Windows Defender, to provide sufficient protection to meet business
requirements. |
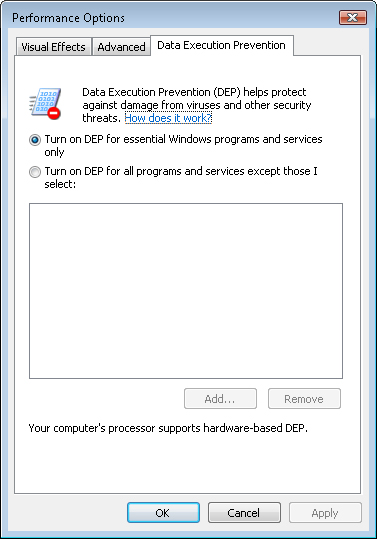
As Figure 2
shows, DEP is enabled by default in both 32- and 64-bit versions of
Windows Vista. By default, DEP protects only essential Windows programs
and services to provide optimal compatibility. For additional security,
you can protect all programs and services.
Address Space Layout Randomization (ASLR)
Address Space Layout Randomization (ASLR)
is another defense capability in Windows Vista that makes it harder for
malicious code to exploit a system function. Whenever a Windows Vista
computer is rebooted, ASLR randomly assigns executable images (.dll and
.exe files) included as part of the operating system to one of 256
possible locations in memory. This makes it harder for exploit code to
locate and therefore take advantage of functionality inside the
executables.
Windows Vista also
introduces improvements in heap buffer overrun detection that are even
more rigorous than those introduced in Windows XP SP2. When signs of
heap buffer tampering are detected, the operating system can immediately
terminate the affected program, limiting damage that might result from
the tampering. This protection technology is enabled for operating
system components, including built-in system services, and can also be
leveraged by ISVs through a single API call.
New Logon Architecture
Logging onto Windows
provides access to local resources (including EFS-encrypted files) and,
in Active Directory environments, protected network resources. Many
organizations require
more than a user name and password to authenticate users. For example,
they might require multifactor authentication using both a password and
biometric identification or a one-time password token.
In Windows XP and
earlier versions of Windows, implementing custom authentication methods
required developers to completely rewrite the Graphical Identification
and Authentication (GINA) interface. Often, the effort required did not
justify the benefits provided by strong authentication, and the project
was abandoned. Additionally, Windows XP only supported a single GINA.
With Windows Vista,
developers can now provide custom authentication methods by creating a
new Credential Provider. This requires significantly less development
effort, meaning more organizations will offer custom authentication
methods for Windows Vista.
The new
architecture also enables Credential Providers to be event-driven and
integrated throughout the user experience. For example, the same code
used to implement a fingerprint authentication scheme at the Windows
logon screen can be used to prompt the user for a fingerprint when
accessing a particular corporate resource. The same prompt also can be
used by applications that use the new credential user interface API.
Additionally,
the Windows logon user interface can use multiple Credential Providers
simultaneously, providing greater flexibility for environments that
might have different authentication requirements for different users.
Rights Management Services (RMS)
Microsoft Windows
Rights Management Services (RMS) is an information-protection technology
that works with RMS-enabled applications to help safeguard digital
information from unauthorized use both inside and outside your private
network. RMS provides persistent usage policies (also known as usage
rights and conditions) that remain with a file no matter where it goes.
RMS persistently protects any binary format of data, so the usage rights
remain with the information—even in transport—rather than merely
residing on an organization’s network.
RMS works by
encrypting documents and then providing decryption keys only to
authorized users with an approved RMS client. To be approved, the RMS
client must enforce the usage rights assigned to a document. For
example, if the document owner has specified that the contents of the
document should not be copied, forwarded, or printed, the RMS client
will not allow the user to take these actions.
In Windows Vista,
RMS is now integrated with the new XML Paper Specification (XPS) format.
XPS is an open, cross-platform document format that helps customers
effortlessly create, share, print, archive, and protect rich digital
documents. With a new print driver that outputs XPS, any application can
produce XPS documents that can be protected with RMS. This basic
functionality will significantly broaden the range of information that
can be protected by RMS.
The
2007 Microsoft Office system provides even deeper integration with RMS
through new developments in Microsoft SharePoint. SharePoint
administrators can set access policies for the SharePoint document
libraries on a per-user basis that will be inherited by RMS policies.
This means that users who have “view-only” rights to access the content
will have that “view-only” access (no print, copy, or paste) enforced by
RMS, even when the document has been removed from the SharePoint site.
Enterprise customers can set usage policies that are enforced not only
when the document is at rest, but also when the information is outside
the direct control of the enterprise.
While the Rights
Management Services components are built into Windows Vista, they can
only be used with a rights management infrastructure and an application
that supports RMS, such as Microsoft Office. The RMS client can also be
installed on Windows 2000 and later operating systems.
Multiple Local Group Policy Objects
As
an administrator, you can now apply multiple Local Group Policy objects
to a single computer. This simplifies configuration management, because
you can create separate Group Policy objects for different roles and
apply them individually, just as you can in with Active Directory Group
Policy objects. For example, you might have a Group Policy object for
computers that are members of the Marketing group, and a separate Group
Policy object for mobile computers. If you need to configure a mobile
computer for a member of the Marketing group, you can simply apply both
local Group Policy objects, rather than creating a single local Group
Policy object that combines all of the settings.