The Windows approach to security is discretionary:
each securable system resource—each file or printer, for example—has an
owner, who has discretion over who can and cannot access the resource.
Usually, a resource is owned by the user who created it. If you create a
file, for example, you are the file's owner under ordinary
circumstances. (Computer administrators, however, can take ownership of resources they didn't create.)
Note:
To exercise full discretionary control over individual files, you must store those files on an NTFS volume. For the sake of compatibility, Windows 7 supports the FAT and FAT32 file
systems used by early Windows versions and many USB flash drives, and
the exFAT file system used on some removable drives. However, none of
the FAT-based file systems support file permissions.
To determine which users have access to a resource, Windows assigns a security identifier (SID) to each user
account. Your SID (a gigantic number guaranteed to be unique) follows
you around wherever you go in Windows. When you log on, the operating
system first validates your user name and password. Then it creates a security access token.
You can think of this as the electronic equivalent of an ID badge. It
includes your user name and SID, plus information about any security
groups to which your account belongs. Any program you start gets a copy of your
security access token.
With User Account Control (UAC) turned on, administrators who log on get two security access tokens—one that has the privileges of a standard user, and one that has the full privileges of an administrator.
Whenever you attempt
to walk through a controlled "door" in Windows (for example, when you
connect to a shared printer) or any time a program attempts to do so on
your behalf, the operating system examines your security access token
and decides whether to let you pass. If access is permitted, you notice
nothing. If access is denied, you get to hear a beep and read a refusal
message.
|
Windows security relies on the use of
a security identifier (SID) to identify a user. When you create a user
account, Windows assigns a unique SID to that account. The SID remains
uniquely associated with that user account until the account is deleted,
whereupon the SID is never used again—for that user or any other user.
Even if you re-create an account with identical information, a new SID
is created.
A SID is a variable-length value that contains a revision level, a 48-bit identifier authority value, and a number of 32-bit subauthority values. The SID takes the form S-1-x-yl-y2-….S-1 identifies it as a revision 1 SID; x is the value for the identifier authority; and y1, y2, and so on are values for subauthorities.
You'll sometimes see a SID in a security dialog box (for example, on the Security tab of
a file's properties dialog box) before Windows has had time to look up
the user account name. If a SID on a Security tab doesn't change to a
name, it's because it's a SID for an account that has been deleted; you
can safely delete it from the permissions list because it'll never be
used again. (If you have a multiboot system, it could be the SID for an
account in another installed operating system. If that's the case, you
should not delete it.) You'll also spot SIDs
in the hidden protected operating system folder \Recycler (each SID you
see in this folder represents the Recycle Bin for a particular user)
and in the registry (the HKEY_USERS hive contains a key, identified by SID,
for each user account on the computer), among other places. The easiest
way to determine your own SID is with the Whoami command-line utility.
For details, see Section 16.1.3 on Section 16.1.3.
Not all SIDs are unique
(although the SID assigned to your user account is always unique). A
number of commonly used SIDs are constant among all Windows
installations. For example, S-1-5-18 is the SID for the built-in Local
System account, a hidden member of the Administrators group that is used
by the operating system and by services that log on using the Local
System account.
|
In determining whom to let pass and whom to block, Windows consults the resource's access control list
(ACL). This is simply a list of SIDs and the access privileges
associated with each one. Every resource subject to access control has
an ACL.
|
Each folder and each file on an NTFS-formatted volume has an ACL (also known as DACL, for discretionary access control list, and commonly called NTFS permissions).
An ACL comprises an access control entry (ACE) for each user who is
allowed access to the folder or file. With NTFS permissions, you can
control access to any file or folder, allowing different types of access for different users or groups of users.
To view and edit NTFS permissions
for a file or folder, right-click its icon and choose Properties. The
Security tab lists all the groups and users with permissions set for the
selected object, as shown below. Different permissions can be set for
each user, as you can see by selecting each one.
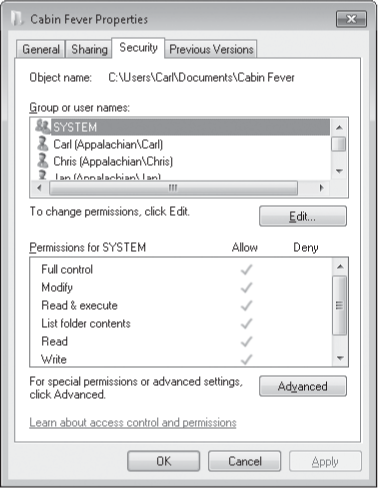
To make changes to the
settings for any user or group in the list, or to add or remove a user
or group in the list, click Edit. (Use caution. Setting NTFS permissions
without understanding the full consequences can lead to unexpected and
unwelcome results, including a complete loss of access to files and
folders. The permission-setting capabilities of the Sharing wizard
provide far greater flexibility and power than were possible in the
basic Windows XP interface. Before you delve into the inner workings of
NTFS permissions on the Security tab, be sure to try the Share With
command or the Sharing tab, both of which invoke the Sharing wizard
unless it has been disabled.)
The access granted by each permission type is as follows:
Full Control Users with Full Control can list contents of a folder, read and open files, create new files, delete files and subfolders, change permissions on files and subfolders, and take ownership of files. Modify Allows the user to read, change, create, and delete files, but not to change permissions or take ownership of files. Read & Execute Allows the user to view files and execute programs. List Folder Contents (folders only) Provides the same permissions as Read & Execute, but can be applied only to folders. Read Allows the user to list the contents of a folder, read file attributes, read permissions, and synchronize files. Write Allows the user to create files, write data, read attributes and permissions, and synchronize files. Special Permissions
The assigned permissions don't match any of the preceding permission
descriptions. To see precisely which permissions are granted, click
Advanced.
|
This manner of allowing and blocking access to resources such as files and printers is essentially unchanged since Windows NT. UAC, which was introduced in Windows Vista, adds another layer of restrictions based on user accounts. Although UAC is sometimes confused with (blamed for?) the restrictions imposed by discretionary access
control lists (described in the preceding paragraphs), it's actually
unrelated. UAC is a method of implementing the rule of least-privilege
user access—a fancy way of saying that a user account should have only
the minimum privileges
required to perform a task; this practice is intended to prevent
malicious programs from using the power of an account to do bad things.
With UAC turned on,
applications are normally launched using an administrator's standard
user token. (Standard users, of course, have only a standard user
token.) If an application requires administrator privileges, UAC asks
for your consent (if you're logged on as an administrator) or the
credentials of an administrator (if you're logged on as a standard user)
before letting the application run. With UAC turned off,
Windows works in the same (rather dangerous) manner as previous
versions: administrator accounts can do just about anything (sometimes
getting those users in trouble), and standard accounts don't have the
privileges needed to run many older programs.
Another feature that
first appeared in Windows Vista places one more doorway on the way to
object access. Somewhat like the discretionary ACLs used to secure file
objects, registry keys, and the like, in Windows 7 each securable object
has an Integrity
Level (IL) access control entry, which can be low, medium, or high.
(Objects that don't have an IL specified have an implicit value of medium.) Each process (program) is also marked with an IL: protected mode ("low rights")
Internet Explorer is low, standard processes are medium, and processes
that require elevation to administrator are high. A process can open an
object for write access only if its IL is equal to or higher than that of the object.
1. Permissions and Rights
Windows distinguishes two types of access privileges: permissions and rights. A permission
is the ability to access a particular object in some defined manner—for
example, to write to an NTFS file or to modify a printer queue. A right is the ability to perform a particular systemwide action, such as logging on or resetting the clock.
The owner of a
resource (or an administrator) assigns permissions to the resource via
its properties dialog box. For example, if you are the printer owner or
have administrative privileges, you can restrict someone from using a
particular printer by visiting the properties dialog box for that
printer. Administrators set rights via the Local Security Policy console.
(This console is available only in the Professional, Enterprise, and
Ultimate editions of Windows 7. In the other editions, rights for
various security groups are predefined and unchangeable.) For example,
an administrator could grant someone the right to install a device
driver.
Note:
In this book, as in many of the Windows messages and dialog boxes, privileges serves as an informal term encompassing both permissions and rights.
2. User Accounts and Security Groups
The backbone of
Windows security is the ability to uniquely identify each user. While
setting up a computer—or at any later time—an administrator creates a
user account for each user. The user account
is identified by a user name and is (optionally) secured by a password,
which the user provides when logging on to the system. Windows then
controls, monitors, and restricts access to system resources based on
the permissions and rights associated with each user account by the
resource owners and the system administrator.
Account type
is a simplified way of describing membership in a security group, a
collection of user accounts. Windows classifies each user account as one
of three account types:
Administrator
Members of the Administrators group are classifed as administrator
accounts. By default, the Administrators group includes the first
account you create when you set up the computer and an account named
Administrator that is disabled and hidden by default. Unlike other account types, administrators have full control over the system. Among the tasks that only administrators can perform are the following:
Create, change, and delete user accounts and groups
Install and uninstall programs
Configure automatic updating with Windows Update
Install an ActiveX control
Install or remove hardware device drivers
Share folders
Set permissions
Access all files, including those in another user's folder
Take ownership of files
Copy or move files into the %ProgramFiles% or %SystemRoot% folders
Restore backed-up system files
Grant rights to other user accounts and to themselves
Configure Parental Controls
Configure Windows Firewall
Standard user
Members of the Users group are classified as standard user accounts.
(In Windows XP, Users group members are called limited accounts.) Many
tasks that were available only to administrators in previous Windows
versions can be performed in Windows 7 by standard users. These
additional tasks do not affect overall system security, and their
prohibition in Windows XP and Windows 2000 made it impractical for most
people to run without full administrative privileges; in Windows 7—as in
Windows Vista—it makes sense to use a standard account. A partial list
of tasks available to standard user accounts includes
Change the password and picture for their own user account
Use programs that have been installed on the computer
Install system and driver updates using Windows Update
Install approved ActiveX controls
Configure a secure Wi-Fi connection
Refresh a network adapter and the system's IP address
View permissions
Create, change, and delete files in their document folders and in shared document folders
Restore their own backed-up files
View the system clock and calendar, and change the time zone
Set personalization options, such as themes, desktop background, and so on
Select a display dots-per-inch (DPI) setting to adjust text size
Configure power options
Log on in Safe Mode
View Windows Firewall settings
Guest Members of the Guests group are shown as guest accounts. Guest accounts have privileges
similar to standard accounts, with some limitations. A user logged on
with the Guest account (but not any other account that is a member of
the Guests group) cannot create a password for the account.
Note:
User accounts that are
not a member of the Administrators, Users, or Guests group do not appear
in User Accounts in Control Panel. There's seldom reason to set up an
account that doesn't belong to one of these groups, but if you do need
to work with such accounts, you must use one of the other user account
management tools.
Assigning an appropriate
account type to the people who use your computer is straightforward. At
least one user must be an administrator; naturally, that should be the
person who administers the computer. All other regular users should each
have a standard user account. Use a guest account if you have guests or
occasional users; that way, they can use your computer without gaining
access to your files.
|
Every
computer running Windows has a special account named Administrator.
Traditionally in Windows, Administrator has been the primary account for managing the computer. Like other administrator
accounts, the Administrator account has full rights over the entire
computer. There's one key difference in Windows 7: the Administrator
account is disabled by default.
In Windows 7, there's seldom a need to use the Administrator account instead of another
administrator account. With default settings in Windows, the
Administrator account does have one unique capability: it's not subject
to UAC, even when UAC is turned on for all other users. All other
administrator accounts (which are sometimes called Protected Administrator
accounts) run with standard-user privileges unless the user consents to
elevation. The Administrator account runs with full administrative
privileges at all times and never needs your consent for elevation. (For
this reason, of
course, it's rather risky. Any application that runs as Administrator
has full control of the computer—which means applications written by
malicious or incompetent programmers can do significant damage to your
system.) |
Security groups
allow a system administrator to create classes of users who share
common privileges. For example, if everyone in the accounting department
needs access to the Payables folder, the administrator can create a group
called Accounting and grant the entire group access to that folder. If
the administrator then adds all user accounts belonging to employees in
the accounting department to the Accounting group, these users will
automatically have access to the Payables folder. A user account can
belong to one group, more than one group, or no group at all.
In large networks based
on Active Directory domains, groups can be a valuable administrative
tool. They simplify the job of ensuring that all members with common
access needs have an identical set of privileges. We don't recommend
creating or using groups other than the built-in Administrators, Users,
and Guests groups on standalone and workgroup-based computers, however.
Permissions and rights
for group members are cumulative. That means that if a user account
belongs to more than one group, the user enjoys all of the privileges
accorded to all groups of which the user account is a member.
|
Windows stores information about user accounts
and security groups in a security database. Where the security database
resides depends on whether your computer is part of a workgroup or a domain.
A workgroup setup (or a standalone computer) uses only local user accounts and local groups. The security database on each computer stores the local user accounts and local
groups that are specific to that computer. Local user accounts allow
users to log on only to the computer where you create the local account.
Likewise, a local account allows users to access resources only on that
same computer.
The alternative is to set up the network as a domain. A Windows domain is a network that has at least one machine running Windows Server as a domain controller. A domain controller is a computer that maintains the security database, including user accounts and groups, for the domain. With a domain user account,
you can log on to any computer in the domain (subject to your
privileges set at the domain level and on individual computers), and you
can gain access to permitted resources anywhere on the network.
In general, if your computer
is part of a Windows domain, you shouldn't need to concern yourself
with local user accounts. Instead, all user accounts should be managed
at the domain controller. But you might want to add certain domain user accounts or groups to your local groups. By default, the Domain Admins group is a member of the local Administrators group, and Domain
Users is a member of the local Users group; members of those domain
groups thereby assume the rights and permissions afforded to the local
groups to which they belong.
|
3. Learning About Your Own Account with Whoami
Windows includes a
command-line utility called Whoami (Who Am I?). You can use Whoami to
find out the name of the account that's currently logged on, its SID,
the names of the security groups of which it's a member, and its
privileges. To use Whoami, open a Command Prompt window. (You don't need
elevated privileges.)
Then, to learn the name of the logged-on user, type whoami.
(This is particularly useful if you're logged on as a standard user,
but running an elevated Command Prompt window—when it might not be
obvious which account is currently "you.") If you're curious about your
SID, type whoami /user. To see a list of your account's group memberships, type whoami /groups /fo list. To learn which privileges are enabled for the logged-on account, type whoami /priv /fo list. For a complete list of Whoami parameters, type whoami /?.