Windows Vista introduced one of the most controversial—and potentially most effective—security changes
in User Account Control (UAC). In short, UAC intercedes whenever a user
or program attempts to perform a system administrative task and asks
for the consent of a computer administrator before commencing what could
be risky business. As implemented in Windows Vista, UAC took a lot of
heat because some users saw it as intrusive, annoying, or both—and many
Windows Vista users ended up turning off UAC altogether.
Microsoft has
made considerable changes to UAC in Windows 7. Users, whether logged on
with an administrator account or a standard account, see far fewer
prompts than in Windows Vista. In Windows 7, standard users can view
Windows settings (in Device Manager, for example) without requiring
elevation. (They'll still need administrative credentials to make
changes, however.) Standard users can install updates and drivers from
Windows Update, pair Bluetooth devices, and reset the network
adapter—all tasks that require elevation in Windows Vista—without a peep
from UAC in Windows 7. In other cases, such as with certain file
operations and installing programs
from Internet Explorer, several prompts are merged. In addition,
Windows 7 provides more flexibility in configuring UAC to work the way
you want; in Windows Vista, unless you dig into Local Security Policy,
UAC is either on or off. For more information about changes to UAC in Windows 7, read the TechNet article "What's New in User Account Control" at w7io.com/1522.
To understand why UAC is
effective, you need to look at security before Windows Vista. Computer
security experts have long espoused least privilege,
a rule that states that you give only enough access for a person to
perform his or her job. (This basic security tenet is sometimes referred
to as LUA, an acronym that, depending upon whom you ask, stands for
"limited user account," "least user access," "least-privileged user
account," or something similar.) In earlier versions of Windows, by
default all accounts are set up as administrator accounts, with full
privileges to do anything on the computer—including the ability to
easily and inadvertently install viruses and perform other harmful
tasks. This is a clear violation of LUA, and security experts
recommended setting up users with limited accounts (comparable to
standard accounts in Windows 7). Because these accounts have fewer
rights and more restrictive permissions, users and programs running with
limited accounts can do less damage. As it turns out, however, using a
limited account in Windows XP is practically impossible, primarily
because most applications of the day were written with the assumption that users would have full administrative privileges, and those programs don't run properly (or at all) when you start them from a limited account.
By contrast, in Windows 7,
accounts after the first one are nonadministrator standard accounts by
default; although they can carry out all the usual daily computing
tasks, they're prevented from performing potentially harmful operations.
These restrictions apply not just to the user; more importantly, they
also apply to any programs launched by the user. Even administrator
accounts run as so-called "protected
administrator" accounts, in which they run with standard-user
privileges except when they need to perform administrative tasks. (This
is sometimes called Admin Approval Mode.)
Newer, security-aware
programs are written so that they don't require administrator privileges
for performing everyday tasks. Programs that truly need administrative
access (such as utility programs that change computer settings) request
elevation. And what about those older programs—many still in use—that
require administrator privileges? Windows 7 has several ways of making
most of them work properly. In one way or another, the program is made
to act as if it's being run by an administrator. One method, for
example, is file and registry virtualization (also known as data
redirection). When a program attempts to write to (and subsequently read
from) a file or registry key on which only administrators have write
access, Windows instead uses a file or key within the current user's
profile. In some cases, a program must be marked as requiring elevation,
in which case it triggers a UAC prompt each time it runs—and then
actually runs using an administrator's credentials.
1. What Triggers UAC Prompts
The types of actions
that require elevation to administrator status (and therefore display a
UAC elevation prompt) include those that make changes to systemwide
settings or to files in %SystemRoot% or %ProgramFiles%. Among the
actions that require elevation are the following:
Installing and uninstalling applications
Installing device drivers that are not included in Windows or provided through Windows Update
Installing ActiveX controls
Changing settings for Windows Firewall
Changing UAC settings
Configuring Windows Update
Adding or removing user accounts
Changing a user's account type
Configuring Parental Controls
Running Task Scheduler
Restoring backed-up system files
Viewing or changing another user's folders and files
Within Windows, you
can identify in advance many actions that require elevation. A shield
icon next to a button or link indicates that a UAC prompt will appear if
you're using a standard account.
You'll notice that, if you log on with an administrator account (and if you leave the default UAC settings unchanged), you'll see fewer consent prompts than you do with Windows Vista. That's because the default setting prompts only when a program tries to install software
or make other changes to the computer, but not when you make changes to
Windows settings (even those that would trigger a prompt for a standard
user with default UAC settings). Windows uses auto-elevation
to elevate without prompting certain programs that are part of Windows.
Programs that auto-elevate are from a predefined list, they must be
digitally signed by the Windows publisher, and they must be stored in
certain secure folders.
|
The changes Microsoft
made to User Account Control in Windows 7 represent a tradeoff between
convenience and security. Some researchers have argued that the decision
to automatically elevate certain tasks is a security hole. As they
demonstrated with sample code, a program can inject itself into one of
these tasks, allowing it to execute with no warning if you are logged on
using a Protected Administrator account.
Is this a
fundamental weakening of Windows security? In our opinion, no. Instead,
it's a sobering illustration of a simple fact: User Account Control
isn't a security silver bullet. It's one layer of a defense-in-depth
strategy.
Some Windows users
assume that UAC consent dialog boxes represent a security boundary. They
don't. They simply represent a place for
an administrator to make a trust decision. If a bad guy uses social
engineering to convince you that you need his program, you've already
made a trust decision. You'll click at least a half-dozen times to
download, save, and launch the bad guy's program. A UAC consent request
is perfectly normal in this sequence, so why wouldn't you click one more
time?
If this scenario
bothers you, the obvious solution is to adjust UAC to its highest level.
This matches the default settings of Windows Vista and disables the
Windows 7–specific auto-elevate behavior. (For details on how to do
this, see Section 15.8.3 on Section 15.8.2.)
If a program tries to use this subterfuge to sneak system changes past
you, you'll see an unexpected consent dialog box from the system. But as
soon as you provide those elevated credentials, the code can do
anything it wants.
A better alternative is to log on using a standard
account, which provides a real security boundary. A standard user who
does not have the administrator password can make changes in her own
user profile only, protecting the system from unintended tampering. (For
more information, see Section 15.8.4 on Section 15.8.3 and Section 16.2.5 on Section 16.2.5.)
Even running as a
standard user doesn't provide complete protection. Malware can be
installed in your user profile, without triggering any system alarms. It
can log your keystrokes, steal your passwords, and send out e-mail
using your identity. Even if you reset UAC to its highest level you
could fall victim to malware that lies in wait for you to elevate and
then does its own dirty work alongside you.
As we said, enabling UAC
is only one part of a multi-layered security strategy. It works best
when supplemented by a healthy skepticism and up-to-date antivirus
software.
|
2. Dealing with UAC Prompts
At logon, Windows
creates a token that is used to identify the privilege levels of your
account. Standard users get a standard token, but administrators
actually get two: a standard token and an administrator token. The
standard token is used to open Explorer.exe (the Windows shell), from
which all subsequent programs are launched. Child processes inherit the
token of the process that launches them so that, by default, all
applications run as a standard user—even when you're logged on with an
administrator account. Certain programs request elevation to
administrator privileges; that's when the UAC prompt is displayed. If
you provide administrator credentials,
Windows then opens the program using the administrator token. Note that
any processes that the successfully elevated program opens also run as
administrator.
As an
elevation-requesting application attempts to open, UAC evaluates the
application and the request and then displays an appropriate prompt. As
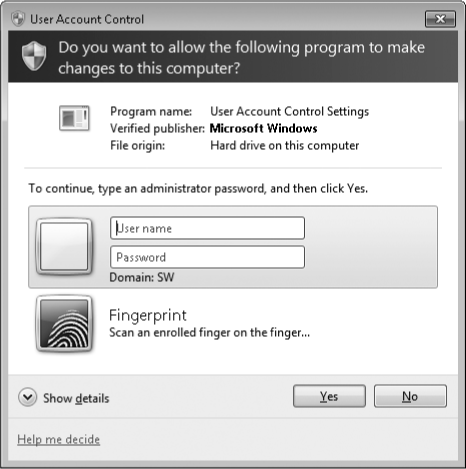
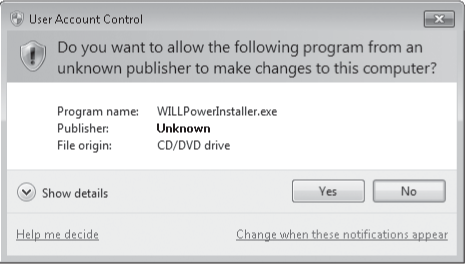
an administrator, the most common prompt you're likely to see is the consent prompt, which is shown in Figure 1. Read it, check the name of the program, click Yes, and carry on.
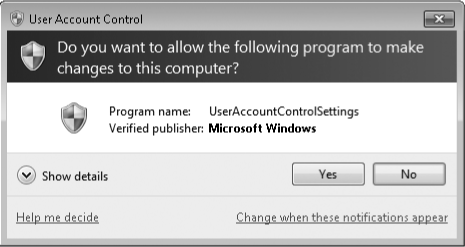
If you use a standard account, when a program requires elevation, you'll see the credentials prompt, which is shown in Figure 2.
If the user is able to provide the credentials (that is, user name and
password, smart card, or fingerprint, depending on how logon
authentication is Configured on the computer) of an administrator, the
application opens using the administrator's access token.
You'll encounter other UAC prompts as well. A colored
background near the top of the prompt dialog box provides a quick
visual clue to the type of program that's requesting elevation:
Red background and red shield icon
Identifies an application from a blocked publisher or one that is
blocked by Group Policy. Be extremely wary if you see one of these.
Yellow-orange background and red shield icon Identifies an application (signed or unsigned) that is not yet trusted by the local computer. (See Figure 3.)
Blue-green background Identifies an administrative application that is part of Windows. (See Figures Figure 1 and Figure 2.)
Gray background Identifies an application that is Authenticode signed and trusted by the local computer.
By default, the UAC dialog box sits atop the secure desktop, a separate process that no other application can interfere with. (If the secure
desktop wasn't secure, a malicious program could put another dialog box
in front of the UAC dialog box, perhaps with a message encouraging you
to let the program proceed. Or a malicious program could grab your
keystrokes, thereby learning your administrator logon password.) When
the secure desktop is displayed, you can't switch tasks or click the
windows on the desktop. (In fact, they're not really windows. When UAC
invokes the secure desktop, it snaps a picture of the desktop, darkens
it, and then displays that image behind the dialog box.)
|
There's a delay before the secure desktop appears
On some systems, you have to wait a few seconds before the screen darkens and the UAC prompt appears on the secure
desktop. There's no easy way to solve the slowdown, but you can easily
work around it. In User Account Control Settings (described in the next
section, Section 15.8.3), you can take it down a notch. The setting below the default provides the same level of UAC protection (albeit with a slight risk that malware could hijack the desktop), except that it does not dim the desktop.
|
Note:
If an application
other than the foreground application requests elevation, instead of
interrupting your work (the foreground task) with a prompt, UAC signals
its request with a flashing orange taskbar button. Click the taskbar button to see the prompt.
It becomes natural
to click through dialog boxes without reading them or giving them a
second thought. But it's important to recognize that security risks to
your computer are real, and that actions that trigger a UAC prompt are potentially
dangerous. Clearly, if you know what you're doing and you click a
button to, say, set the Windows Update settings, you can blow past that
security dialog box with no more than a quick glance to be sure it was
raised by the expected application. But if a UAC prompt appears when
you're not expecting it—stop, read it carefully, and think before you
click.
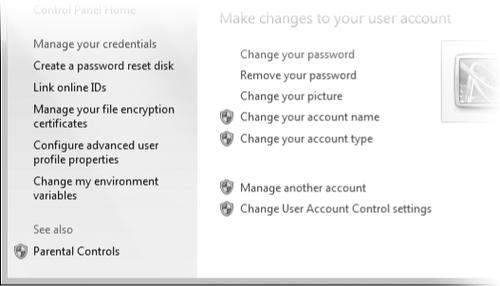
3. Modifying UAC Settings
User Account Control is not for everybody, but in Windows 7 you can tone
it down without disabling it altogether. To review your options and
make changes, in the Start menu search box or in Control Panel, type uac and then click Change User Account Control Settings. A window similar to the one shown in Figure 4 appears.
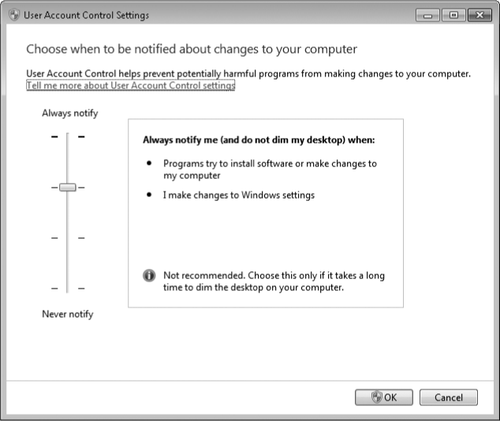
Your choices in this
window vary slightly depending on whether you use an administrator
account or a standard account. (Specifically, the second option from the
top is different.) For standard accounts, the top setting is the
default; for administrator accounts, the second setting from the top is
the default. Table 1 summarizes the available options.
To make changes, move the
slider to the position you want. Be sure to take note of the advisory
message in the bottom of the box as you move the slider. Click OK when
you're done—and then respond to the UAC prompt that appears! Note that,
when you're logged on with a standard account, you can't select one of
the bottom two options, even if you have the password for an
administrator account. To select one of those options, you must log on
as an administrator and then make the change.
Table 1. User account Control Settings
| Slider Position | Prompts when a program tries to install software or make changes to the computer | Prompts when you make changes to Windows settings | Displays prompts on a secure desktop |
|---|
| Standard user account | | | |
| Top (Default) |

|

|

|
| Second |

|

| |
| Third |

| | |
| Bottom (Off) | | | |
| Administrator account | | | |
| Top |

|

|

|
| Second Default) |

| |

|
| Third |

| | |
| Bottom (Off) | | | |
|
User Account Control settings don't stick
If you find that nothing
happens when you make a change in User Account Control settings, be
sure that you're the only one logged on to your computer Simultaneous
logons using Fast User Switching can cause this problem
|
|
Users of the
Professional, Enterprise, and Ultimate editions of Windows 7 can use the
Local Security Policy console to modify the behavior of UAC. Start
Local Security Policy (Secpol.msc), and open Security Settings\Local
Policies\Security Options. In the details pane, scroll down to the
policies whose names begin with "User Account Control " For each policy,
double-click it and click the Explain tab for information before you
decide on a setting. With these 10 policies, you can make several
refinements in the way UAC works—including some that are not possible in
the User Account Control Settings window. For details about each of
these policies, see "UAC Group Policy Settings" at w7io.com/1523.
|
Regardless of
your UAC setting, the shield icons still appear throughout Control
Panel, but you won't see UAC prompts if you've lowered the UAC
protection level. Clicking a button or link identified with a shield
immediately begins the desired action. Administrators run with full administrator privileges; standard users, of course, still have only standard privileges.
Warning:
Don't forget that UAC
is more than annoying prompts. Only when UAC is enabled does an
administrator run with a standard token. Only when UAC is enabled does
Internet. Explorer run in a low-privilege Protected Mode. And, of
course, only when UAC is enabled does it warn you when a rogue
application attempts to perform a task with systemwide impact. For these
reasons, we urge you not to select the bottom option in User Account
Control Settings, which turns off UAC completely.
4. Working Around UAC Without Disabling It
Although the UAC prompts
are sometimes intrusive, that's the point. First, they provide a
not-so-subtle reminder that what you're about to do has a systemwide
effect. But most importantly, UAC prevents a malicious application from
silently installing without your knowledge. Most spyware, viruses, and
other malware get installed as a direct, albeit unintended, result of a
user action, such as clicking a link. When you click a link that you
think is going to display some pretty pictures, wouldn't you be pleased
to have UAC tell you that it's attempting to install a program?
One misperception about
UAC is that it doesn't let you do certain things, or that it "locks you
out" of your own computer. In fact, UAC doesn't prevent anything—all it
does is inform you when an application requires administrator access.
Remember that, even when you're logged on with an administrator account,
you ordinarily run as a standard user. Need to run something that
requires full administrator privileges? Simply respond to the prompt.
(If you find that you can't access certain folders and files, it's
likely that the restriction is imposed by NTFS permissions—which are
only tangentially related to UAC.)
Most people encounter lots
of UAC prompts while setting up a new computer, configuring it, and
installing programs. After that, they seldom see a prompt from UAC and
forget that it's even there. But if you frequently tweak your computer's
settings or install new programs, consider these tricks for running
into fewer prompts:
Use an administrator Command prompt window Because child processes inherit the access token of the process that opens them, programs that you run from an administrator
command prompt run as an administrator without further prompting.
You'll need to respond to just a single prompt when you open the Command
Prompt window. Then you can enter commands, open Microsoft Management
Console (MMC) consoles, start programs, and edit the registry without
further prompting.
To open an administrator Command Prompt window, use one of these methods:
In the Start menu search box, type cmd.
Then press Ctrl+Shift+Enter. (This little-known shortcut is equivalent
to right-clicking a shortcut and clicking Run As Administrator.)
Create
a shortcut to Cmd.exe. Open the shortcut's properties dialog box and,
on the Shortcut tab, click Advanced. Select Run As Administrator.
Naturally, you can run only programs for
which you know the name and location of the executable file, as well as
any required command-line parameters. (You can often glean this
information by examining an application's shortcut.) Also note that
Windows Explorer, Internet Explorer, and Control Panel do not run as
administrator, even when started from an administrator
command prompt. (You can run Control Panel applications if you know the
command line; it's just the main Control Panel window that does not run
with elevated privileges.)
Run as a standard user As a standard user, you'll probably encounter fewer
elevation prompts than you do as an administrator. In this situation,
many applications refuse to run or they run with limitations. (For
example, they might not display all settings or they might not save
settings you make.) On occasions when you do need to use such an
application with full capabilities, right-click and choose Run As
Administrator. Or, in the Start menu search box, type the program name
and press Ctrl+Shift+Enter.
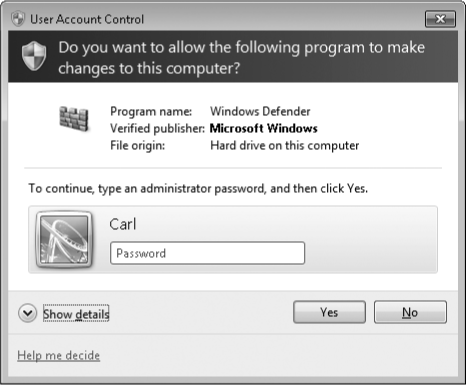
Use a fingerprint reader
If you ordinarily use a standard user account—always a good
practice—and you're required to type the password for your administrator
password when UAC presents a credential prompt (see Figure 5),
you'll find it easier to use biometric authentication, such as a
fingerprint reader. With this inexpensive peripheral (included as a
standard feature on many business-class notebook PCs), you can simply
swipe your finger instead of typing a lengthy password.