The situation often arises where confidential or
sensitive content in an organization needs to be protected. Many ways
exist to protect data in corporate enterprises, but one of the
challenges facing administrators is not always
how to protect content, but more often what data to protect.
Administrators rely on end users to identify content that should be
protected based on either company policy, or the user’s recognition of
the sensitivity of particular data.
Often, the data content is not
only important, but may also be of a confidential nature. One way to
enable users to protect data that they know is confidential is to train
them on the usage of EFS. EFS is a file encryption technology that
allows end users to store data content on NTFS volumes in encrypted
format. EFS is a user-specific technology, meaning that once a file has
been encrypted while a user is logged in with a particular username,
only that logged-on username can be used to read or decrypt the file.
Enabling EFS is as easy as
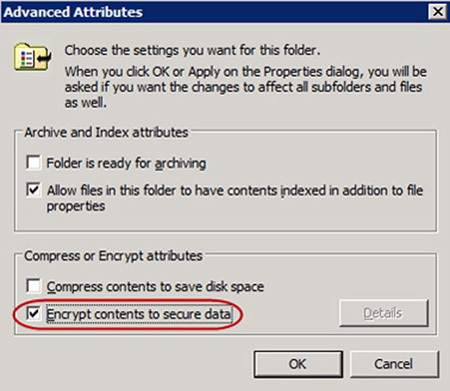
checking a box. Each file and folder on an NTFS volume has an attribute
that is used to enable encryption. See Figure 1
for an example of this attribute at the folder level. Once you have
enabled a folder for EFS, all files placed into that folder will
automatically be encrypted. EFS is a not a new technology, but Microsoft
has enhanced some aspects of it with the release of Windows Server 2008
R2. One of the key
areas of change for EFS revolves around the introduction of support for
new algorithms, as we will discuss in the next section.
EFS keys and algorithms
EFS utilizes both
symmetric and asymmetric key technology to encrypt and secure data on
NTFS volumes. A symmetric key is a single key which can quickly be used
to encrypt or decrypt larger amounts of data. Symmetric keys are often
used to encrypt content because of the speed advantage they have over
key pairs. EFS utilizes symmetric keys to secure data content.
Asymmetric key pairs are a
complimentary pair of keys. One of the keys is used to encrypt while the
other to decrypt. Asymmetric keys are slower when dealing with large
amounts of data, and so, are not used in EFS to secure data, but are
instead used to secure the symmetric key. So, ultimately, it is a
combination of keys that are used by EFS to secure a user’s data in the
file system; a single key to encrypt the data content and a key pair to
secure the single key.
In earlier iterations of
EFS, Microsoft has employed industry standard encryption algorithms such
as Triple DES (3DES) and Data Encryption Standard X (DESX). As
encryption standards have developed and improved, Microsoft has
continued to update EFS to support the newer protocols, as was evident
with the release of Windows XP SP1. From Windows XP SP1, forward EFS
began utilizing Advanced Encryption Standard (AES) as its primary
encryption mechanism.
The newest version of EFS,
included with Windows Server 2008 R2 and Windows 7, has followed in the
same footsteps as the preceding versions and has been improved to
reflect the algorithm standards that exist today. The following
represent the algorithms supported by the Windows Server 2008 R2
iteration of EFS:
Advanced Encryption Standard
Secure Hash Algorithm (SHA)
Elliptic Curve Cryptography (ECC)
Smart card-based encryption
A critical addition to the
preceding list is the new support for ECC. Many environments today are
required to comply with stricter regulatory requirements. The addition
of ECC allows for these high-security environments to comply with Suite B
encryption requirements as set forth by the National Security Agency.
Today, Suite B compliance is utilized by United States government
agencies to protect classified information.
EFS and policy enforcement
With
additional compliance regulations existing in many environments today,
administrators often need a mechanism to control the enforcement of
certain security policies. In Windows 7 and Windows Server 2008 R2, you
have the capability to control the way EFS behaves in the Local Computer
Policy on the machine. Utilizing the Local Computer Policy, you have
the ability to enforce ECC as well as configure other settings such as
if Smart Cards are required for EFS usage. Since Local Computer Policy
settings are administrated individually on each computer, it makes it
very difficult to use these settings in a larger environment.
The most common way to
enforce policy onto large groups of machines in an AD environment is by
utilizing Group Policy. In order to address EFS policy enforcement on a
broader scale, Microsoft has incorporated settings into Group Policy to
allow the capability to control and enforce settings centrally for new
EFS components. You will file EFS settings within a Group Policy under Computer Configuration | Policies | Windows Settings | Security Settings | Public Key Policies | Encrypting File System.
In Suite B
compliance environments, the usage of RSA encryption algorithms is not
allowed and only ECC may be used for EFS. Group Policy has three ECC
pertinent settings, Allow, Require, and Don’t Allow, which are displayed
in Figure 2.
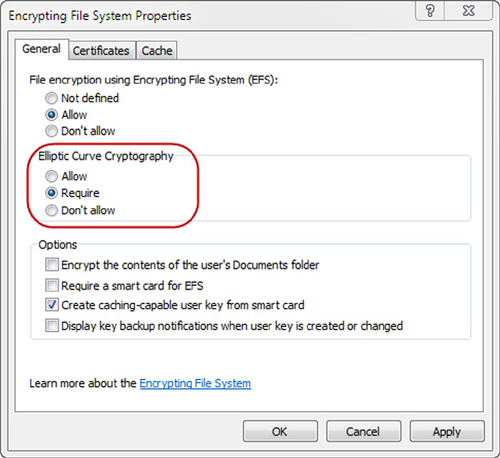
The Allow setting simply allows
the use of ECC, but does not enforce it. This means that both RSA and
ECC are available when this setting has been configured. If you are in
an environment that requires Suite B compliance, Allow is not an
appropriate setting. Instead, you would want to select the second radio
button for Require. Require prevents the use of RSA and enforces that
ECC be the only protocol in use with EFS. The final setting of Don’t
Allow blocks the usage of ECC, thus all EFS key sets will be generated
utilizing RSA.
Cipher.exe
Cipher.exe is a command that
has existed for some time, and essentially embodies a command prompt
version of the file system GUI exposure of EFS, but with a little more
dynamism. Since administrators are often looking for a faster and more
manageable way to perform mundane or repetitive tasks, Cipher.exe fits
well into an administrator’s toolbox.
Cipher.exe can help
to reduce the administrative burden associated with EFS by allowing bulk
EFS actions to be performed against the file system. It has the
capability to target files and folders and force encryption or decryption
throughout directory structures. Instead of having to move files into a
designated folder manually for them to be encrypted, Cipher.exe allows
targeting for encryption via the command prompt. Additionally, it can
also be used to assist with other EFS administrative tasks such as key
management tasks. One such task includes the generation of new user
keys, another includes updating encrypted files with new user encryption
keys.
With Cipher.exe, two
switches exist that allow the administrator to request new EFS keys: /K
and /R. /K will allow an administrator to create a new certificate and
key, while /R allows an administrator to generate a new recovery
certificate and key.
Since
Windows 2008 R2 has introduced the capability to generate keys based on
the ECC algorithm, Microsoft has enabled the specification of the ECC
protocol and key length with the new /ECC:length
switch. The new ECC switch can be used in conjunction with the /K and
/R switches to allow the administrator to impact key generation in two
ways: first, ECC keys will be generated, and second, the key length for
the ECC keys can be specified. The options for the ECC key length
include 256, 384, and 521 key lengths. ECC keys can only be used with
self-signed certificates.