Using Group Policies
To configure a large
group of computers in a single operation, you can import a security
template into the Group Policy Object for a domain, site, or
organizational unit object in Active Directory. However, there are a few
cautions that you must observe when using group policies to deploy
security templates.
Group Policy Deployment Cautions
As with other
security settings, the configuration parameters you import into the
Group Policy Object for a specific container are inherited by all the
objects in that container, including other containers. Most networks use
different levels of security for computers performing various roles, so
it is relatively rare for administrators to apply a security template
to a domain or site object, because then all the computers in that
domain or site receive the same settings. At the very least, your domain
controllers should have a higher level of security than the other
computers on your network.
Tip
When
creating security templates for importation into group policies, the
best practice is to place your computers into organizational units
according to their roles and create individual templates for each
organizational unit. This way you can customize the security
configuration for each role, and modify the template for each role as
needed, without affecting the others. |
Another
consideration when importing security templates into Group Policy
Objects is the amount of data in the template itself. Every computer
running a Windows operating system in an Active Directory container
refreshes its group policy settings every 90 minutes, except for domain
controllers, which refresh their settings every five minutes. It is
possible for a security template to contain a large number of settings,
and the continual refreshing of large templates to a large fleet of
computers can generate a great deal of Active Directory traffic and
place a heavy burden on the network’s domain controllers.
Note
When
you look at the sizes of the pre-defined security templates included
with Windows Server 2003, it is easy to see which ones you should not
deploy using group policies. Most of the templates are less than ten
kilobytes, with the notable exceptions of the “DC Security.inf” and
“Setup Security.inf” templates, which are 127 and 784 kilobytes
respectively. |
Deploying Security Templates Using Group Policies
To deploy a security
template using group policies, you select an Active Directory object
that has a GPO and import the template into the GPO. The template’s
settings then become part of the GPO, overwriting any existing values.
The importation process proceeds as follows:
1. | Open the Active Directory Users And Computers console.
|
2. | Select
the domain or organizational unit object to which you want to apply the
template and, from the Action menu, choose Properties. The Properties
dialog box for that object appears.
|
3. | Click
the Group Policy tab, select a Group Policy Object from the Group
Policy Object Links list, and then click Edit. The Group Policy Object
Editor console appears.
Tip Instead
of using an existing Group Policy Object, you can also create a new one
by clicking New and then supplying a name for the GPO. |
|
4. | Under Computer Configuration, expand the Windows Settings subheading, and then click Security Settings.
|
5. | From the Action menu, select Import Policy. The Import Policy From dialog box appears (see Figure 1).
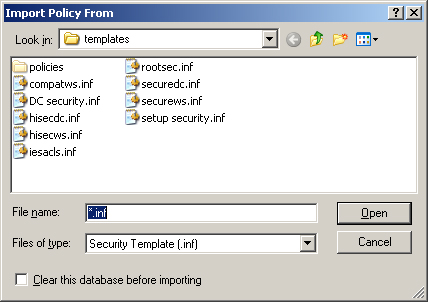
|
6. | Select
the security template file you want to import, and then click Open. The
settings in the template are imported into the Group Policy Object.
|
7. | Close the Group Policy Object Editor console, and then click OK in the Properties dialog box for the object you selected.
|
8. | Close the Active Directory Users And Computers console.
|
Using the Security Configuration And Analysis Tool
Security
Configuration And Analysis is an MMC snap-in that you can use to apply a
security template to the local computer interactively. However, in
addition to configuring the security settings for the computer, the
snap-in also provides the ability to analyze the current system security
configuration and compare it to a baseline saved as a security
template. This enables you to quickly determine whether someone has
changed a computer’s security settings and whether the system conforms
to your organization’s security policies.
As with the
Security Templates snap-in, Windows Server 2003 does not include a
shortcut to a Security Configuration And Analysis console, so you must
add the snap-in to a console yourself. When you do this for the first
time, the console contains nothing but the Security Configuration And
Analysis heading, as shown in Figure 2.

Analyzing a System
To
use the Security Configuration And Analysis snap-in, you must first
create a database that will contain a collection of security settings.
The database is the interface between the actual security settings on
the computer and the settings stored in your security templates. After
you create a database (or open an existing one), you then import a
security template of your choice. Once you have imported a template you
can proceed to apply the settings in that template to the computer or
analyze the computer’s current settings.
When you begin
the analysis by selecting Analyze Computer Now from the Action menu, the
system prompts you for the location of its error log file, and then
proceeds to compare the settings in the template to the computer’s
current settings. Once the analysis is complete, the console produces a
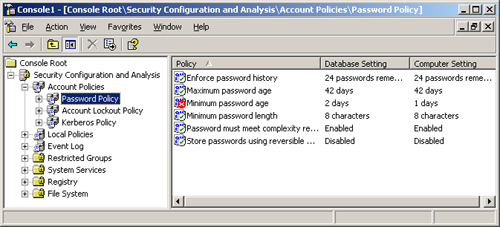
display similar to that of the Security Templates snap-in (see Figure 3), containing all the standard security settings found in a template.
The big difference
between the Security Templates console and this display, however, is
that the policies listed in the details pane have columns containing the
database settings and the computer settings. The Database Settings
column contains the values imported from the template you selected,
while the Computer Settings column contains the system’s current
settings. The comparison of the two values for each policy is reflected
in the flag on each policy name, as shown in Figure 4. The meanings of the flags are as follows;
X in a red circle Indicates that the policy is defined in both the database and on the computer, but that the configured values do not match
Green check mark in a white circle Indicates that the policy is defined in both the database and on the computer, and that the configured values do match
Question mark in a white circle
Indicates that the policy is not defined in the database and therefore
was not analyzed, or that the user running the analysis did not have the
permissions needed to access the policy on the computer
Exclamation point in a white circle Indicates that the policy is defined in the database, but does not exist on the computer
No flag Indicates that the policy is not defined in the database or on the computer
Changing Security Settings
As you examine the
elements of the database and compare the template values with those of
the computer, you might find discrepancies and want to make changes to
the computer’s configuration. There are several ways in which you can do
this, such as the following:
Apply the database settings to the computer
If you want to use the exact settings from the template that you
imported into the database, you can simply select Configure Computer Now
from the Action menu to apply them to the computer.
Modify the database settings You can double-click any policy in the console tree to display its Properties dialog box and modify its value in the database.
Caution
Modifying
a policy value in the Security Configuration And Analysis snap-in
changes the database value only, not the actual computer setting. For
the changes you make to take effect on the computer, you must either
apply the database settings to the computer using the Configure Computer
Now command or export the database to a new template and apply it to
the computer using any of the standard methods. |
Create a new template
You can select Export Template from the Action menu to create an
entirely new template from the settings currently in the database, and
then apply the template to the computer using any of the standard
methods.
Important
The
Export Template feature creates a new template from the current
database settings at the time you execute the command, not from the
computer’s current settings. |
Modify the computer’s settings manually You
can always modify the computer’s security settings directly by using a
member server’s Local Security Settings console (open the console by
selecting Local Security Policy from the Administrative Tools menu), by
modifying the appropriate Group Policy Object, or by manually
manipulating file system or registry permissions.
Using Secedit.exe
Secedit.exe is a
command prompt utility that can perform the same functions as the
Security Configuration And Analysis snap-in. The advantage of
Secedit.exe is that you can call it from scripts and batch files,
enabling you to automate your security template deployments. Another big
advantage of Secedit.exe is that you can use it to apply only part of a
security template to a computer, something that you cannot do with the
Security Configuration And Analysis snap-in or with Group Policy
Objects. For example, if you want to apply the file system’s permissions
from a template, but leave all the other settings alone, Secedit.exe is
the only way to do it.
To use Secedit.exe,
you run the program from the command prompt with one of the following
six main parameters, plus additional parameters for each function:
Configure
Applies all or part of a security database to the local computer. You
can also configure the program to import a security template into the
specified database before applying the database settings to the
computer.
Analyze
Compares the computer’s current security settings with those in a
security database. You can configure the program to import a security
template into the database before performing the analysis. The program
stores the results of the analysis in the database itself, which you can
view later using the Security Configuration And Analysis snap-in.
Import Imports all or part of a security template into a specific security database
Export Exports all or part of the settings from a security database to a new security template
Validate Verifies that a security template is using the correct internal syntax
Generaterollback Creates a security template that you can use to restore a system to its original configuration after applying another template.