IPSec Protocols
The
IPSec standards define two protocols that provide different types of
security for network communications: IP Authentication Header (AH) and
IP Encapsulating Security Payload (ESP). These protocols are discussed
in the following sections.
IP Authentication Header
The IP
Authentication Header protocol does not encrypt the data in IP packets,
but it does provide authentication, anti-replay, and integrity services.
You can use AH by itself or in combination with ESP. Using AH alone
provides basic security services, with relatively low overhead. AH by
itself does not prevent unauthorized users from reading the contents of
captured data packets. However, using AH does guarantee that no one has
modified the packets en route, and that the packets did actually
originate at the system identified by the packet’s source IP address.
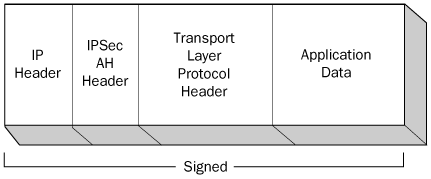
When a computer uses AH
to protect its transmissions, the system inserts an AH header into the
IP datagram, immediately after the IP header and before the datagram’s
payload, as shown in Figure 2.
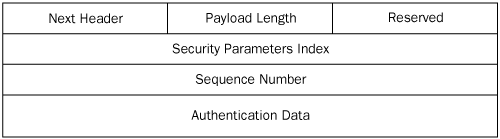
The contents of the AH header are shown in Figure 3, and the functions of the header fields are as follows:
Next Header
Contains a code specifying the protocol that generated the header
immediately following the AH header, using the protocol codes specified
by the IANA. If IPSec is using AH alone, this field contains the code
for the protocol that generated the datagram’s payload, which is usually
TCP, UDP, or ICMP.
Payload Length Specifies the length of the AH header.
Reserved Unused.
Security Parameters Index
Contains a value that, in combination with the packet’s destination IP
address and its security protocol (AH), defines the datagram’s security association.
A security association is a list of the security measures, negotiated
by the communicating computers, which the systems will use to protect
the transmitted data.
Sequence Number
Contains a value that starts at 1 in the first packet using a
particular security association, and is incremented by 1 in every
subsequent packet using the same security association. This field
provides IPSec’s anti-replay service. If an IPSec system receives
packets with the same sequence numbers and the same security
association, it discards the duplicates.
Authentication Data Contains an integrity check value (ICV)
that the sending computer calculates, based on selected IP header
fields, the AH header, and the datagram’s IP payload. The receiving
system performs the same calculation and compares its results to this
value.
Note
The ICV is the message authentication code. Its main purpose is to authenticate a message and verify its integrity. |
IP Encapsulating Security Payload
The
IP Encapsulating Security Payload (ESP) protocol is the one that
actually encrypts the data in an IP datagram, preventing intruders from
reading the information in packets they capture from the network. ESP
also provides authentication, integrity, and anti-replay services.
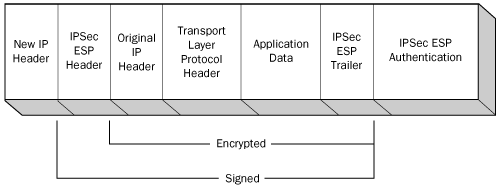
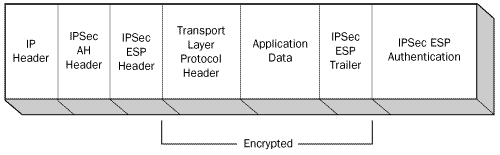
Unlike AH, which inserts only a header into the IP datagram, ESP inserts
a header and a trailer, which surround the datagram’s payload, as shown
in Figure 4.
The protocol encrypts all the data following the ESP header, up to and
including the ESP trailer. Therefore, someone who captures a packet
encrypted using ESP, could read the contents of the IP header, but could
not read any part of the datagram’s payload, including the TCP, UDP, or
ICMP header.
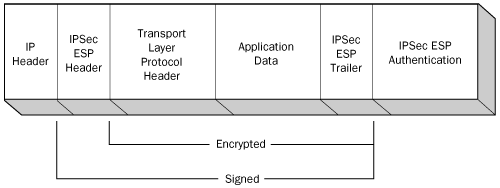
An IPSec packet can use
ESP by itself or in combination with AH. When a packet uses both
protocols, the ESP header follows the AH header, as shown in Figure 5.
Although AH and ESP perform some of the same functions, using both
protocols provides the maximum possible security for a data
transmission. When ESP computes its ICV, it calculates the value only on
the information between the ESP header and trailer; no IP header fields
are included in an ESP ICV. Therefore, it is possible for an attacker
to modify the contents of the IP header in an ESP-only packet, and have
those changes go undetected by the recipient. AH includes most of the IP
header in its ICV calculation, so combining AH with ESP provides more
protection than ESP alone.
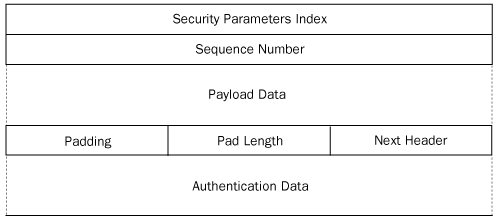
The contents of the ESP header are shown in Figure 6, and the functions of the header fields are as follows:
Security Parameters Index
Contains a value that, in combination with the packet’s destination IP
address and its security protocol (AH or ESP), defines the datagram’s security association.
Sequence Number—Contains a value that starts at 1 in the first packet
using a particular security association, and is incremented by 1 in
every subsequent packet using the same security association. This field
provides IPSec’s anti-replay service. If an IPSec system receives
packets with the same sequence numbers and the same security
association, it discards the duplicates.
Payload Data Contains the TCP, UDP, or ICMP information carried inside the original IP datagram.
Pad Length Specifies the number of bytes of padding the system added to the Payload Data field to fill out a 32-bit word.
Next Header
Contains a code specifying the protocol that generated the header
immediately following the ESP header, using the protocol codes specified
by the IANA. In virtually all cases, this field contains the code for
the protocol that generated the datagram’s payload, which is usually
TCP, UDP, or ICMP.
Transport Mode and Tunnel Mode
IPSec can operate in two modes: transport mode and tunnel mode.
To protect communications between computers on a network, you use
transport mode, in which the two end systems must support IPSec, but
intermediate systems (such as routers) need not. All the discussion of
the AH and ESP protocols so far in this lesson applies to transport
mode.
Tunnel mode is
designed to provide security for wide area network (WAN) connections,
and particularly virtual private network (VPN) connections, which use
the Internet as a communications medium. In a tunnel mode connection,
the end systems do not support and implement the IPSec protocols; the
routers at both ends of the WAN connection do this.
The tunnel mode communications process proceeds as follows:
Computers on one of the private networks transmit their data using standard, unprotected IP datagrams.
The
packets reach the router that provides access to the WAN, which
encapsulates them using IPSec, encrypting and hashing data as needed.
The router transmits the protected packets to a second router at the other end of the WAN connection.
The second router verifies the packets by calculating and comparing ICVs, and decrypts them if necessary.
The
second router repackages the information in the packets into standard,
unprotected IP datagrams and transmits them to their destinations on the
private network.
IPSec
also uses a different packet structure in tunnel mode. Unlike transport
mode, in which IPSec modifies the existing IP datagram by adding its
own headers, tunnel mode implementations create an entirely new datagram
and use it to encapsulate the existing datagram, as shown in Figure 7.
The original datagram, inside the new datagram, remains unchanged. The
IPSec headers are part of the outer datagram, which exists only to get
the inner datagram from one router to the other.