1. Protocol Filters
The Windows Firewall and the RRAS Basic Firewall
are not the only options available for restricting incoming traffic.
Several options exist that can be used to permit and/or block traffic by
setting protocol filters. TCP/IP Filters can be set directly on the
network connection. Routing and Remote Access Policies provide an option
to set remote access protocol filters. IPSec policies can be
established that block or permit access to specific ports. Unlike the
Windows Firewall, the RRAS Basic Firewall protocol filters are not
stateful. Protocol filters can be set for incoming and outgoing traffic.
1.1. TCP/IP Filters
Basic protocol filters can be established on any
TCP/IP interface. These packet filters are static filters and only
operate to filter inbound TCP/IP communications based on port or
protocol IP number. If TCP/IP filters are configured, all traffic is
dropped except for what is sent to the ports and/or protocol IP numbers
specified in the interface. In this way, filtering occurs by exception;
either it is not used at all, or only those ports defined in the filter
are listening for incoming traffic.
To create packet filters on an interface, begin
by opening the interface Properties page. Click Start, then select and
open Control Panel. Select and open "Network connections," then
right-click on the desired network interface and click Properties. Click
the Advanced button. Select the Options tab and click the Properties
button. You will see the screen shown in Figure 1.
Select Enable TCP/IP Filtering (All Adapters).
For each box (TCP Ports, UDP Ports, and IP Protocols), leave the default
Permit All or select Permit Only. If Permit Only is
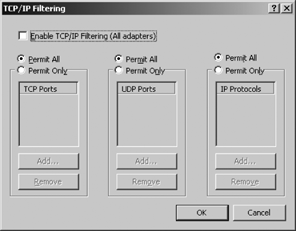
selected, click the Add button and enter a port
to allow and then click OK. Repeat the process until all required ports
have been selected and appear in the boxes.
By
default, TCP/IP filters will block all communications with the
exception of those protocols you configure. Before enabling filtering,
ensure that you understand what ports are required. |
|
1.2. Routing and Remote Access Protocol Filters
In addition to providing a basic firewall service, protocol filters can be added to an RRAS
routing interface, or to an RRAS remote access policy. To set remote
access protocol filters, create a remote access policy or configure
filters for an existing policy. The policy should establish parameters
for connectivity. Adding inbound and outbound filters is an additional
configuration item. Packet filters can be configured for inbound and
outbound traffic, and can be set to pass all traffic except packets
defined in filters, or to discard all traffic except packets allowed by
filters.
To configure protocol filters on a routing
interface, begin by opening the RRAS console and selecting the General
node. In the detail pane, right-click the interface on which to add a
filter and click Properties. Click the General tab and then click either
Inbound Filters or Outbound Filters. Select the filter action. Click
New to add a port to filter. On the "Add IP filter" page, select either
Source Network or Destination Network. Enter the IP address and subnet
mask. Use the drop-down Protocol box to select TCP, UDP, ICMP, Any, or
Other. Enter the required source and destination port. Click OK twice to
return to the General page. Repeat the process to add additional
filters.
1.3. Filtering Using IPSec
The IPSec protocol is built into the network
stack of Windows Server 2003. In addition to providing security for
communications between hosts on a LAN, IPSec can also be configured to
block or permit inbound and/or outbound communications. An IPSec policy
is composed of one or more rules, each of which can contain multiple
filters. Each IPSec filter defines a source and destination IP address,
and source and destination port or protocol ID. Therefore, in addition
to filtering based on port alone, IPSec can block communications based
on port and IP address combinations. A filter action determines whether
the specific packet is blocked or permitted. IPSec policies can be
simple (such as one that "blocks all traffic to port 23"), be a
combination of filters (such as "block all traffic except port 80
traffic from this specific range of IP addresses"), and be quite complex
(with multiple inbound and outbound filters).
All IPSec filters are static filters.
IPSec policies can be implemented locally, or applied via a Group Policy
if the computer is joined in a domain.
2. Which Firewall Services Should You Use?
With so many options for creating host-based
firewall services, which option should be used? Like most security
decisions, the answer is, "It depends." Many factors are likely to
influence this decision, but the most important deciding factors are
your specific business and security requirements. Use Table 1
to select a firewall service that meets all of your requirements. If
multiple services do so, in most cases the one that is simplest to
implement will be the best choice.
Table 1. Firewall services decision points
| Attribute | TCP/IP protocol filtering | Windows Firewall | IPSec | RRAS basic firewall | RRAS protocol filters |
|---|
| Implementation difficulty | Simplest | Simple | Complex | Simple to complex | Simple to complex |
| Direction of traffic that can be filtered | Inbound | Inbound | Inbound and outbound | Inbound and outbound | Inbound and outbound |
| Filters can be based on the IP address of the source | No | Yes (called exception scope) | Yes | Yes | Yes |
| Provides a DHCP allocator | No | The Windows Firewall used with ICS | No | Yes | Yes |
| DHCP range is configurable | N/A | No | N/A | Yes | Yes |
| Designed to be combined with NAT on the same system | No | The Windows Firewall used with ICS | No | Basic firewall plus NAT | No |
| Can be managed via Group Policy | No | Yes | Yes | No | No |
| Provides options for central management | No | Via Group Policy | Group Policy | IAS and remote access policies | IAS and remote access policies |
| Provides static filtering | Yes | Yes | Yes | Yes | Yes |
| Provides stateful filtering | No | Yes | No | Yes | No |
| Provides application layer filtering | No | No | No | No | No |