Understanding Certificate Enrollment and Renewal
The actual process by
which CAs issue certificates to clients varies, depending on the types
of CAs you have installed. If you have installed enterprise CAs, you can
use auto-enrollment,
in which the CA receives certificate requests from clients, evaluates
them, and automatically determines whether to issue the certificate or
deny the request. If you have installed stand-alone CAs, you cannot use
auto-enrollment, so you must arrange for an administrator to monitor the
CA (using the Certification Authority console) for incoming requests
and to make decisions about whether to issue or deny the requests.
Using Auto-Enrollment
Auto-enrollment
enables clients to automatically request and receive certificates from a
CA with no manual intervention from administrators. To use
auto-enrollment, you must have domain controllers running Windows Server
2003, an enterprise CA running on Windows Server 2003, and clients
running Microsoft Windows XP Professional. You control the
auto-enrollment process using a combination of group policy settings and
certificate templates.
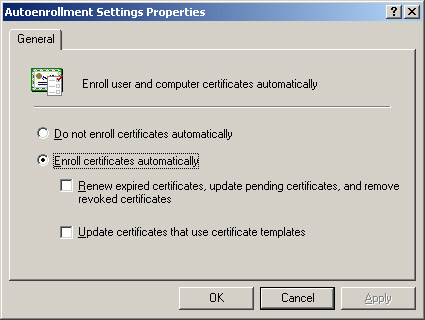
By
default, Group Policy Objects (GPOs) contain settings that enable
auto-enrollment for all user and computer objects in a domain. You
configure these settings by opening the Autoenrollment Settings policy,
located in the Windows Settings\Security Settings\Public Key Policies
folder in both the Computer Configuration and User Configuration nodes
in the Group Policy Object Editor. In the Autoenrollment Settings
Properties dialog box (see Figure 1),
you can disable auto-enrollment entirely for the objects receiving
these GPO settings. You can also enable the objects to renew and update
their certificates automatically.
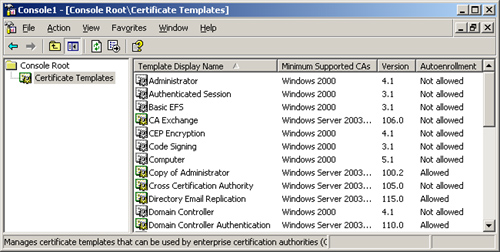
The other mechanism
you can use to control auto-enrollment is built into the certificate
templates that define the properties of specific certificate types. To
manage certificate templates, you use the Certificate Templates snap-in,
as shown in Figure 2.
Using this tool, you can specify the validity and renewal periods of
specific certificate types and choose cryptographic service providers
for them. Using the Security tab for a particular template, you can also
specify which users and groups are allowed to request certificates
using that template.
When
a client requests a particular type of certificate, the CA checks the
properties of the client’s Active Directory object to determine if the
client has the permissions needed to receive the certificate. If the
client has the appropriate permissions, the CA issues the certificate
automatically.
Using Manual Enrollment
Stand-alone CAs cannot use
auto-enrollment, so when a stand-alone CA receives a certificate
request from a client, it stores the request in a queue until an
administrator decides whether to issue the certificate. To monitor and
process incoming requests, administrators use the Certification
Authority console, as shown in Figure 3.
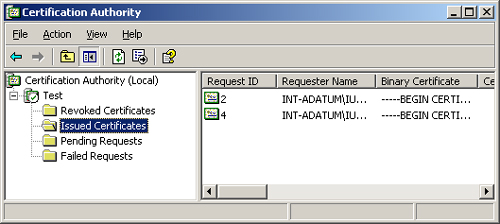
In the
Certification Authority console, incoming certificate enrollment
requests appear in the Pending Requests folder. After evaluating the
information in each request, an administrator can choose to issue or
deny each request. Administrators can also view the properties of issued
certificates and revoke certificates as needed.
Manually Requesting Certificates
In some cases, the
process of requesting a certificate and receiving it from a CA is
invisible to both the client and the administrator. Certain applications
might request certificates and receive them in the background, then
proceed to function in the normal manner. In other cases, however, users
must explicitly request certificates, using one of the tools that
Windows Server 2003 provides.
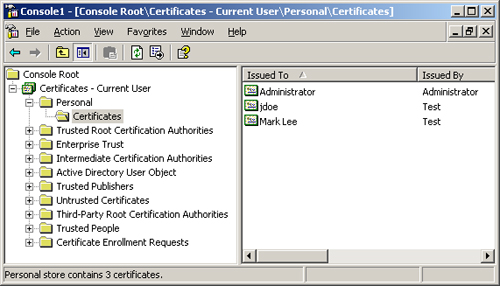
Using the Certificates Snap-in
The Certificates snap-in (see Figure 4)
is a tool that you can use to view and manage the certificates of a
specific user or computer. The snap-in’s main display consists of
folders that contain categories for all the certificates accessible to
the designated user or computer. If your organization uses enterprise
CAs, the Certificates snap-in also enables you to request and renew
certificates using the Certificate Request Wizard and Certificate
Renewal Wizard.
Off the Record
The
Certificates snap-in is limited to use with enterprise CAs because the
snap-in reads certificate information for the user or computer from
Active Directory, and clients of stand-alone CAs are not expected to
have access to Active Directory resources. |
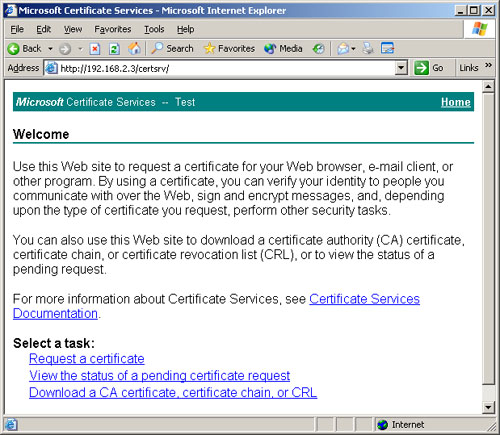
Using Web Enrollment
When you install
Certificate Services on a computer running Windows Server 2003, you have
the option of installing the Certificate Services Web Enrollment
Support module as well. To function properly, this module requires you
to have IIS installed on the computer first, along with support for ASP.
Selecting this module during the Certificate Services installation
creates a series of Web pages on the computer running the CA (see Figure 5); these pages enable users to submit requests for particular types of certificates.
Tip
You
can also install the Certificate Services Web Enrollment Support module
on a server running Windows Server 2003 that is not a CA, enabling you
to integrate this module into existing Web servers. |
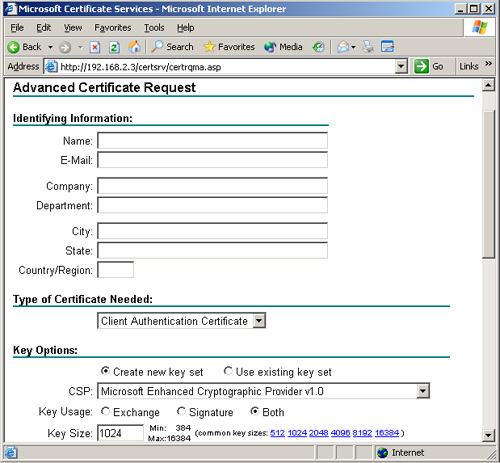
The Web
Enrollment Support interface is intended to give internal or external
network users access to stand-alone CAs. Because stand-alone servers do
not use certificate templates, the requests submitted by clients must
include all the necessary information about the certificates being
requested and about the users of the certificates. When clients request
certificates using the Web Enrollment Support interface, they can select
from a list of predefined certificate types or create an advanced
certificate request in which they specify all the required information
in a Web-based form (see Figure 6).
Off the Record
The
Web Enrollment Support interface can generate requests for most
certificate types, but not for certificates that are exclusive to
enterprise CAs, such as smart card logon certificates. |
Revoking Certificates
Several conditions
can prompt an administrator to revoke a certificate. If a private key is
compromised, or an unauthorized user has gained access to the CA, or
even if you want to issue a certificate using different parameters, such
as longer keys, you must revoke the certificates that are no longer
usable. A CA maintains a CRL, which it publishes to clients on a regular
basis. Enterprise CAs publish their CRLs in the Active Directory
database, so clients can access them using the standard Active Directory
communication protocol, called Lightweight Directory Access Protocol
(LDAP). A stand-alone CA stores its CRL as a file on the server’s local
drive, so clients must access it using an Internet communications
protocol, such as Hypertext Transfer Protocol (HTTP) or File Transfer
Protocol (FTP).
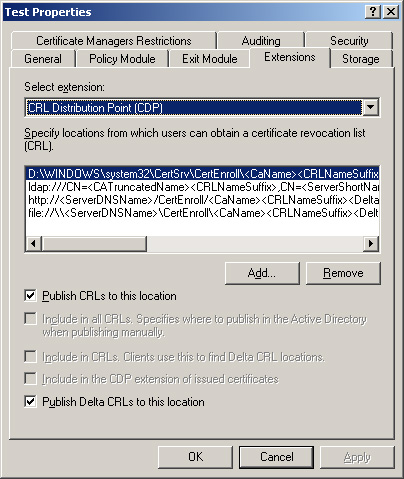
Every certificate contains
the path to the CA’s distribution point for CRLs. You can modify this
path in the Certification Authority console by displaying the Properties
dialog box for the CA, and then clicking the Extensions tab (see Figure 7).
However, if you plan to modify a CA’s CRL distribution point, you must
do so before it issues certificates. When an application authenticates a
client using a certificate, it checks the CRL distribution point
specified in the certificate, to make sure that the certificate has not
been revoked. If the CRL is not at its specified distribution point, the
application rejects the certificate.
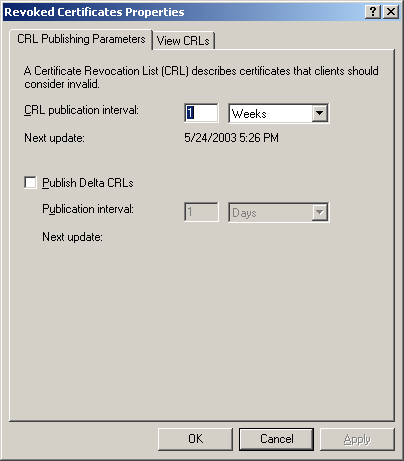
By
selecting the Revoked Certificates folder in the Certification
Authority console and then displaying its Properties dialog box (see Figure 8), you can specify how often the CA should publish a new CRL, and also configure the CA to publish delta CRLs. A delta CRL
is a list of all certificates revoked since the last CRL publication.
In organizations with large numbers of certificates, using delta CRLs
instead of base CRLs can save a great deal of network bandwidth. For
example, rather than publishing a base CRL every week, you can choose to
publish delta CRLs weekly, and publish the base CRLs monthly.