Introducing the Public Key Infrastructure
A public key infrastructure
is a collection of software components and operational policies that
govern the distribution and use of public and private keys, using
digital certificates. To protect data transmitted over a network,
computers use various types of encryption to encode messages and create
digital signatures that verify their authenticity. For one computer to
encrypt a message and another computer to decrypt it, both must possess a
key.
Understanding Secret Key Encryption
Encryption is
essentially a system in which one character is substituted for another.
If you create a key specifying that the letter A should be replaced by
Q, the letter B by O, the letter C by T, and so forth, any message you
encode using that key can be decoded by anyone else who has that key.
This is called secret key encryption,
because you must protect the key from compromise. For computer
transactions, this simple type of encryption is all but useless, because
there is usually no practical way to distribute the secret key to all
recipients. After all, if the object is to send an encrypted message to a
recipient over the network, it would hardly be appropriate to first
send the secret encryption key in an unsecured message.
For encryption on a data network to be both possible and practical, computers typically use a form of public key encryption. In public key encryption,
every user has two keys, a public key and a private key. As the names
imply, the public key is freely available to anyone, while the private
key is carefully secured and never transmitted over the network. The way
the system works is that data encrypted with the public key can only be
decrypted with the private key, and conversely, data encrypted with the
private key can only be decrypted using the public key. It is the
protection of the private key that guarantees the security of messages
encrypted using this system.
Encrypting Data
If someone wants to send you a message making sure that no one but you
can read it, that person must obtain your public key and use it to
encrypt the message. The person can then transmit the message to you
over the network, secure in the knowledge that only you possess the
private key needed to decrypt it. Even if an intruder were to intercept
the message during transmission, it would still be in its encrypted
form, and therefore impenetrable. Once you receive the message and
decrypt it using your private key, you could reply to it by using the
other party’s own public key to encrypt your response, which only that
person can decrypt, using the private key.
Digitally Signing Data
If you want to send someone a message and have them be absolutely sure
that it came from you, you can digitally sign it by using your private
key to encrypt all or part of the data. Anyone receiving the message can
then decrypt the encoded data using your public key. The fact that your
public key successfully decrypted the message proves that you sent it,
because only your private key could have encrypted it. This not only
prevents other users from impersonating you by sending messages in your
name, it also provides the recipient with proof that you sent the
message, so that you cannot repudiate it later.
Note
It
is usually not practical to encrypt an entire message for the purpose
of digitally signing it. Instead, most PKI systems create a hash from
the message and then encrypt the hash using the private key. A hash is a digital summary of the message created by removing redundant bits according to a specialized hashing algorithm. |
Verifying Data
When you want to be certain that the message you are sending to a
recipient is not modified en route, you can use a hashing algorithm to
create a hash from the message, and then encrypt both the message and
the hash using your private key. When the message arrives at its
destination, the recipient’s computer decrypts the message using your
public key, and then uses the same hashing algorithm to create a hash
from the incoming message. If the hash included with the message matches
the hash calculated by the receiving system, the message is verified as
being unchanged since its transmission.
Using Certificates
For
public key encryption to be a reliable form of communication, there has
to be a verifiable mechanism for the distribution of public keys.
Otherwise, an imposter could distribute a public key using another
person’s name, and receive encrypted messages intended for that person,
which the imposter could decrypt using the corresponding private key. To
distribute public keys, Windows Server 2003 and most other systems
supporting a PKI use digital certificates. A digital certificate is a document that verifiably associates a public key with a particular person or organization.
|
A digital certificate
contains the public key for a particular entity, such as a user or an
organization, plus information about the entity and about the
certification authority (CA) that issued the certificate. The
Telecommunication Standardization Sector of the International
Telecommunication Union (ITU-T) has published a standard called X.509
(03/00), “The Directory: Public-key and Attribute Certificate
Frameworks,” which defines the format of the certificates used by most
PKI systems, including Windows Server 2003. In addition to the public
key, every digital certificate contains these attributes:
Version Identifies the version of the X.509 standard used to format the certificate Serial number A value assigned by the CA that uniquely identifies the certificate Signature algorithm identifier Specifies the algorithm that the CA used to calculate the certificate’s digital signature Issuer name Specifies the name of the entity that issued the certificate Validity period Specifies the period during which the certificate is valid Subject name Specifies the name of the entity for which the certificate is issued
Most certificates also contain other attributes, which are specific to the certificates’ intended functions.
|
To use public key encryption, you must obtain a certificate from an administrative entity called a certification authority (CA).
A CA can be a third-party company that is trusted to verify the
identities of all parties involved in a digital transaction, or it can
be a piece of software on a computer running Windows Server 2003 or
another operating system. The type of CA you use for your organization
depends on who is involved in the secure transactions.
Obtaining a certificate
from a CA can be manual, with the user explicitly requesting that a CA
issue a certificate, or automatic, with an application requesting and
obtaining a certificate in the background as part of its normal
function. No matter how the process occurs, the CA issues a public key
and a private key as a matched pair. The private key is stored on the
user’s computer in encrypted form, and the public key is issued as part
of a certificate. The certificate is essentially a carrier for the
public key and related information, and facilitates the distribution of
the key to the people that need it.
Using Internal and External CAs
For a certificate to be
useful in securing a digital transaction, it must be issued by an
authority that both parties to the transaction trust to verify each
other’s identities. When you are designing your own PKI for your
network, you can deploy your own certificate authorities, or use a
third-party CA, or both. Your choice typically depends on whether the
parties involved in the transaction work for the same company or
different ones.
If you want to ensure
that internal communications in your organization are secure, you would
be best served by installing your own CAs. Windows Server 2003 includes
Certificate Services, a service that functions as a CA. All the users in
your organization can usually trust a CA run by the company to verify
other users’ identities. However, if your organization engages in
digital transactions with other companies, an internal CA is typically
not useful, because the other companies are not going to trust your own
CA to verify your identity.
For securing external
transactions, the best practice is to obtain certificates from a neutral
third-party organization that functions as a commercial certification
authority. Companies such as Thawte and VeriSign, Inc., are examples of
commercial CAs that are trusted throughout the IT industry.
|
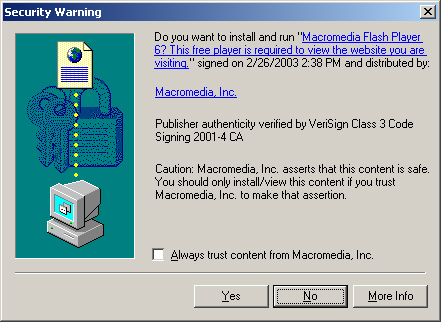
For
a Windows operating system user, one of the most common occasions for
encountering certificates occurs when you download software from the
Internet and Microsoft Internet Explorer displays a dialog box, like the
one in the following illustration, that prompts you to confirm that you
want to install the software. This dialog box specifies the
manufacturer of the software and indicates whether the download includes
a certificate that verifies the source of the download.
If a certificate is
included, it contains the software manufacturer’s public key, which your
computer uses to decrypt the download’s digital signature. If
decryption is successful, you know that the software you downloaded was
digitally signed using the private key corresponding to the public key
in the certificate. As long as you trust the authority that issued the
certificate to verify the software manufacturer’s identity, you know
that the download came from the manufacturer and was not tampered with
en route.
|
Understanding PKI Functions
With a Windows Server 2003 PKI in place, network administrators can perform the following tasks:
Publish certificates
Certificate Services can create certificates and publish them on a Web
site or in Active Directory, where clients, such as users, computers,
and applications, can retrieve them.
Enroll clients
Enrollment is the term used to describe the process by which a client
requests and receives a certificate from a certification authority. When
a client requests a certificate, the CA (or the CA administrator)
verifies the client’s identity, and then issues a certificate in the
client’s name.
Use certificates Once
a client requests and receives a certificate, the client can use it to
secure its communications in various ways, depending on the capabilities
of the certificate and the functions for which it was issued.
Renew certificates
Certificates are typically valid for a finite period. At the end of
that period, the client must either renew the certificate with the CA or
stop using it.
Revoke certificates
When a CA administrator explicitly revokes a certificate, the CA adds
it to a certificate revocation list (CRL). The CA publishes this list at
regular intervals, to inform the other systems on the network of
certificates that they should no longer honor.
Practice: Viewing a Certificate
In this practice,
you install the Macromedia Shockwave Player software on a computer
running Windows Server 2003. During the installation procedure, you can
display the certificate that verifies the identity of the software’s
publisher.
1. | Log on to Windows Server 2003 as Administrator.
|
2. | Click Start, point to All Programs, and then click Internet Explorer. A Microsoft Internet Explorer window appears.
|
3. | From the Tools menu, select Internet Options, and then click the Security tab.
|
4. | Move the Security Level For This Zone slider to Medium, and then click OK.
Changing the Security Level prevents the Internet Explorer
Enhanced Security Configuration feature from blocking access to the
Certificate Services Web page.
|
5. | In the Address text box, type http://sdc.shockwave.com/shockwave/download, and then press Enter. The Macromedia Shockwave & Macromedia Flash Player Download Center page appears.
|
6. | Click the Install Now button. The Security Warning dialog box appears.
This dialog box specifies that you are about to install the
Shockwave Player software and states that the computer has confirmed the
authenticity of the publisher.
|
7. | Click the Macromedia, Inc., hyperlink. The Certificate dialog box appears with the General tab active.
Notice that the software uses a certificate supplied by VeriSign,
which provides assurance that the software comes from the specified
publisher and has not been modified.
|
8. | Click the Details tab.
This tab displays a list of all the certificate’s attributes.
|
9. | Click
OK to close the Certificate dialog box, and then click Yes in the
Security Warning dialog box. The software installation proceeds.
|
10. | Close Internet Explorer after the installation completes.
|