Windows Internet Explorer 7 is installed by default
in Vista. Security has been enhanced like never before in this version
of the browser. The security features include
Pop-up blocker
Phishing filter
Protected Mode
Fix Settings for Me...
Cookie handling
ActiveX opt-in
Security Status Bar
Digital certificates
Clear the browsing history, cached content, cookies, form data, and saved passwords
Pop-Up Blocker
Pop-ups are extra windows
that appear when you visit a website. They are usually advertisements
and are often from an advertiser other than the website you intended to
visit. At best, they rob your bandwidth and show you advertisements that
you may or may not be interested in. At worst, they can be used to
download and install malware onto your computer. You can turn on the
pop-up blocker and configure it to block all pop-ups (High), most
pop-ups (Medium), or all but pop-ups from secure (SSL) websites (Low).
You can also add websites to an Allowed Sites list for the pop-ups if
you choose to.
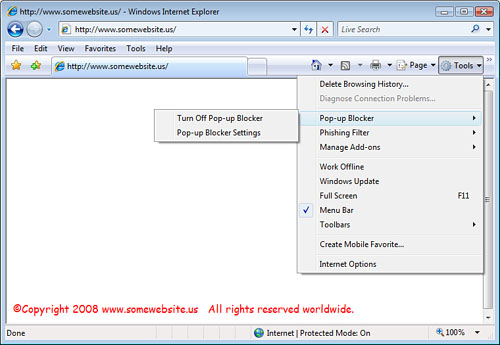
You enable the pop-up blocker by clicking Tools on the command bar, as shown in Figure 1.
From here, you can highlight Pop-Up Blocker and select Turn On Pop-up
Blocker, Turn Off Pop-Up Blocker, or configure Pop-Up Blocker Settings.
Typically, you should turn it on and configure it for Medium protection.
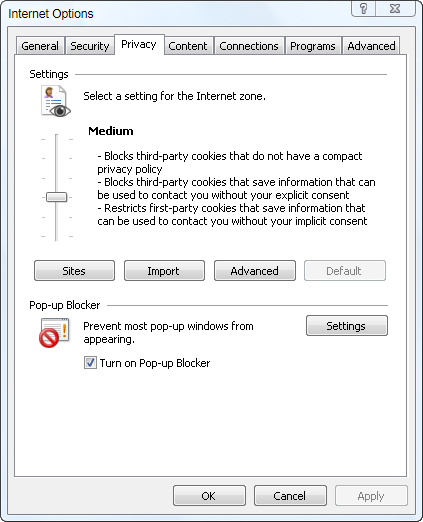
You
can also access the configuration for the pop-up blocker by accessing
the lower half of the Privacy tab in Internet Options (from the File
menu or the command bar: Tools > Internet Options). Figure 2 shows the Internet Options dialog box.
|
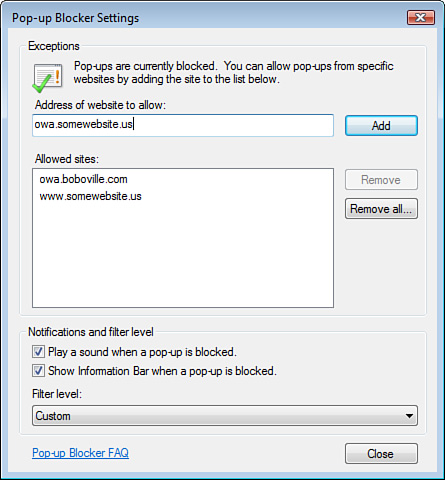
Some sites actually
have beneficial pop-ups, like your horoscope, or Outlook Web Access
Calendar Reminders. For any of these types of websites where you want
the pop-ups, simply select Tools > Pop-Up Blocker > Pop-Up Blocker Settings and add the website to the Allowed Sites list (as shown in Figure 3).
|
Phishing Filter
Phishing
is when a bad guy tricks you into visiting his bogus website so he can
do bad things to you, to your browser, and/or to your computer system.
This is usually accomplished by convincing you the website is legitimate
and is a website you should want to go to. Very often the bad guys
spoof a legitimate website, like your bank or credit card company, by
copying all the legitimate graphics and text, and then they send you an
email implying that you need to validate some information, or they have
some incredible offer for you. When you visit the bogus website, they
steal your passwords, credit card information, or can download malware
to your computer.
Internet Explorer 7 has a
built-in Phishing filter to help protect you from the bad things that a
phishing site can and will do to you. You can configure the Phishing
filter by selecting the Tools button on the command bar and selecting Check this Website
to check the domain name against a list of known phishing sites, Turn
On (or Off) the Phishing Filter, Report a website as illegitimate, or
configure the Phishing Filter settings. This last option opens the
Advanced tab of the Internet Options dialog box, where you can fine-tune
how the Phishing filter works.
The Phishing filter in IE7
is updated several times each hour and warns you when you attempt to
access a website that appears to be illegitimate or one that has been
reported as a phishing site.
Suspicious websites cause
the IE7 address bar (also called the Security Status Bar) to turn
yellow, as a warning to proceed with caution. The yellow warning
presents the site’s web page to you.
If the website is a known
phishing website, the address bar changes to red as a warning, and IE7
does not present the site’s web page to you. You must override IE7’s
warning to proceed to the potentially harmful website.
|
Ignoring the Phishing
filter’s warning and proceeding to the suspicious website might be a
really bad thing to do. The warning popped up for a reason, and very
often, the warning is correct. Proceed only if you are absolutely
certain that the website is known and trusted as safe.
You should also visually
confirm the address that you are connected to. Very often, the website
looks legitimate, and you may have gotten connected through what looked
like a trusted source, but the bad guys have redirected you to their
bogus, malicious website.
If you choose to
proceed, recognize that you may be compromising the security of your
computer and of your private information. If your computer is on a
network, like at home or in an office, you might be inviting the bad
guys into that network. This decision may be bigger than just you, your
computer, and your private information. You may be giving up the entire
network to the bad guys!
|
Alert
If
the website has been reported as a potential phishing website, and you
know or believe it is not a phishing website, you can choose to report
the website as a safe site by selecting I Don’t Think This Is a Phishing
Website from the warning.