Cookie-Handling
Cookies
are small files that get written to your computer, as part of your
user’s profile, while you are browsing websites on the Internet. They
are used to store information about your visit to the website and
usually contain information to make your browsing experience more
feature rich. While their intent is for good purpose, there are several
security issues related to cookies. Cookies can be used to track your
actions with the browser, even after you’ve left the website that wrote
the cookie. Cookies often contain private information, such as credit
card and other financial information, as well as personal preferences
and usernames and passwords configured for various sites. Worthy
websites that store private information usually encrypt the private
data, but often they use weak encryption to keep the processing times to
a minimum. This encryption can often be cracked relatively easily.
A cookie gets used, for
example, when you personalize a home page—with a greeting that calls you
by name, your chosen background color, and additional content that you
choose to have on your personalized home page. These choices are stored
in a cookie on your computer, and when you return to the personalized
web page, the web server reads the cookie from your computer and
dynamically constructs your custom web page. These cookies are referred
to as persistent cookies because they remain on your computer after you close your browser.
Another example of how a
cookie is used is the e-commerce shopping cart. As you peruse a website
and select things to purchase, your selected items are written into a
cookie on your computer. That way, when you go to the checkout, the
website knows what you’ve selected. These cookies are usually deleted
when you leave the website and are referred to as session cookies.
Tip
Session cookies are temporary and are deleted from your computer after you leave the website.
Persistent cookies
remain on your computer, even after you close your browser. These are
generally considered to be the more dangerous of the two to have lying
around on your computer.
Two other types of cookies are as follows:
First-party cookies— Cookies written by the website you specifically went to.
Third-party cookies—
Cookies written by some entity other than the website you chose to
visit. This is often the result of the desired website selling
advertising and tracking access to some marketing company.
You
can access the configuration for the cookie handling by accessing the
top half of the Privacy tab in Internet Options (from the File menu or
the command bar: Tools > Internet Options). Here, by clicking the Settings
button, you can identify websites that are always allowed to or
restricted from ever using cookies. You can import settings from an
Internet Explorer Privacy Preference file. By clicking the Advanced
button, you can configure the cookie handling policy for first-party
and third-party cookies, as well as enable or disable session cookies.
Typical configuration is to allow first-party cookies and session
cookies and block third-party cookies. The forth button on this tab
resets the configuration parameters back to their default settings.
So, session cookies clean
themselves up, and we block all third-party cookies. To minimize the
risk of some tracking cookies or exposure of private information stored
in encrypted cookies, you would be prudent to periodically delete all
cookies.
Caution
Cookies Anyone?
When you delete cookies, useful information that gets fed to websites
is lost. This information could include username, password, credit card
information, and more. Losing this information could be problematic for
some users. You may need to re-enter that information the next time you
visit the website. Understand the type of data you use in cookies from
your browsing habits and requirements and then decide whether you really
want to delete this data.
We see how to delete cookies in a
few more pages when we look at clearing the browsing history, cached
content, cookies, forms data, and saved passwords.
ActiveX Opt-In
ActiveX
is what is called “mobile code.” Mobile code is a small program that
gets downloaded to each and every client that connects to a website and
is then executed on the client computer. ActiveX controls provide
feature-rich browsing that enhances the browsing experience. These
controls can be infected with malware before being downloaded, and bad
guys can attack and take control of these processes.
By default, IE7 disables
almost all ActiveX controls and requires explicit user consent before
they can be accessed. This way, you allow, or “opt in,” to only the
approved and desired ActiveX controls. This protective behavior of IE7
reduces what is called the “attack surface” of your computer.
ActiveX
controls are add-ons to the browser. You can access the configuration
for ActiveX controls by accessing the Programs tab in Internet Options
(from the File menu or the command bar: Tools > Internet Options). By
clicking the Manage
add-ons button, you can sort and learn more about the add-ons that are
available on your computer. You can also download new add-ons or enable,
disable, or delete any of the installed add-ons.
Alert
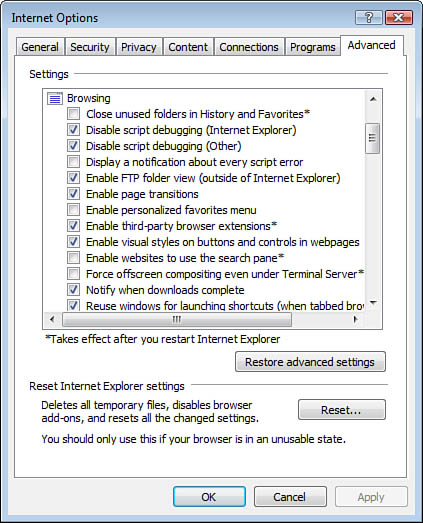
Another area to configure how Internet Explorer handles mobile code is on the Advanced tab of the Internet Options dialog box. Figure 7
shows where you configure numerous security controls, like digital
certificate verification processing and displaying notification for
script errors.
The Security Status Bar
The Security Status Bar (SSB) is
built into the address bar at the top of the browser. It provides visual
indications to the user to identify various security considerations.
During normal browsing, the SSB changes color and displays a lock and
messages regarding security reports that are available for the websites.
These messages indicate a level of trust for the website.
Note
Check Your Websites
Users should always review the entire uniform resource locator (URL) in
the address bar to verify that they are actually connected to the
website they believe they are.
These features rely on
the Phishing filter being enabled. (It is enabled by default on
Internet, Local Intranet, and Restricted Sites zones.)
When the address bar is white,
there is no information about the website, but the connection is not
encrypted. The user should not enter any private data, like a username,
password, credit card number, or any other financial data.
When the address bar is green,
the website is using an encrypted channel, and the identity of the
website has been verified through the use of digital certificates. After
you have confirmed that the URL is accurate, it is relatively safe to
submit private data.
When the address bar is yellow,
the website is considered suspicious. The name on the digital
certificate does not match the name of the website, or there may be some
other digital certificate validation error. The website may contain
content that resembles that of a phishing website. Either disconnect
from the website or proceed with caution if you know and trust the
website.
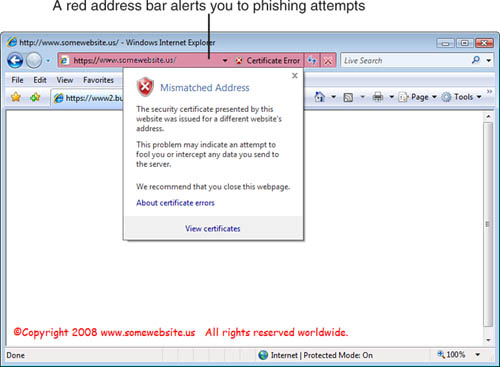
When the address bar is red, the
website is believed to be a known phishing site. The website has been
reported to Microsoft as fraudulent, and there may be verification
errors with the digital certificate. It is recommended that you should
not proceed or submit any information to this website. If you choose to
proceed, the SSB turns red and you can click to view the security
warning, as shown in Figure 8.
Tip
The presence of a gold
lock on the SSB indicates that the connection to the website is
encrypted. By double-clicking the lock, you can access a security report
for the secured website.