12.2.5. Troubleshooting a VPN Client
If everything goes well,
you'll be able to connect to the VPN server right after you create the
connection. However, not everything always goes well. Instead, you may
need to do a little troubleshooting.
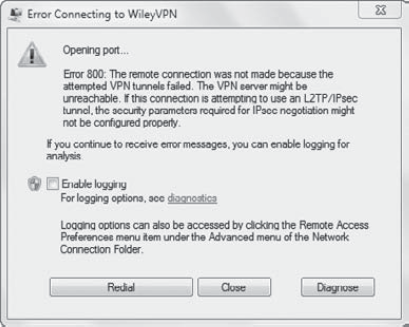
Figure 5
shows the error screen you'll probably see if you can't connect. By
default, it will try to redial or reconnect three times. However, if it
didn't work the first time, it probably won't work the second or third
time.
There are a few
important steps you can take. First, make sure you have Internet access.
Without Internet access, the VPN connection won't work. However, this
is the easiest problem to solve because the VPN connection will let you
know and prompt you to connect to the Internet.
If you have Internet access but still can't connect, you can try these extra steps.
Check the settings.
Enable logging.
Run diagnostics.
5.1. Check Settings
The logical first step is to
double-check the settings. Often the problem is just a simple issue of
entering the wrong IP address. You can do this by checking the
properties of the connection. If your VPN server has more specific
settings, you'll be able to configure them from these property pages.
You can access the VPN
connection properties with the following steps. Launch the Network and
Sharing Center. Click Change Adapter Settings. Right-click the VPN
connection and select Properties.
There are five tabs, and we
explore four of them in the following sections. The Sharing tab is more
important for home users than for enterprise users. It can be used to
enable Internet Connection Sharing (ICS). In other words, it can be used
to share its Internet connection.
5.1.1. VPN General Tab
You can access the General tab to change some of the basic properties you set when you created the connection. Figure 6
shows properties available on the General tab. The obvious thing to
check here is to ensure you have entered the correct IP address.
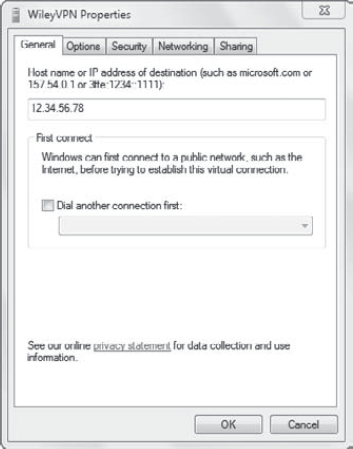
You can also
reconfigure how the VPN connects to the Internet. This should be
configured if the system isn't normally connected to the Internet. You
can select the Dial Another Connection First check box, and then select
one of the connections from the drop-down list box.
5.1.2. VPN Options Tab
The Options tab allows you to
set the options for the connection. Even though these options are
labeled as Dialing Options and Redialing Options, they also refer to the
VPN connection. In other words, even if you're using a broadband
connection and not dialing at all, these settings apply.
Figure 7
shows the Options tab with the default settings. If the system can't
connect on the first try, it will automatically attempt to retry three
more times. This gives the VPN server time to recover if multiple
clients are connected at the same time, stretching its resources.
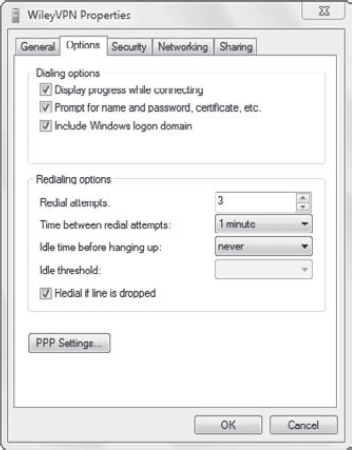
If you click the PPP Settings
button, you'll have the option of setting three advanced options. These
may be needed for some VPN servers:
Enable LCP Extensions. This is enabled by default.
Enable Software Compression.
Negotiate Multi-Link For Single-Link Connections.
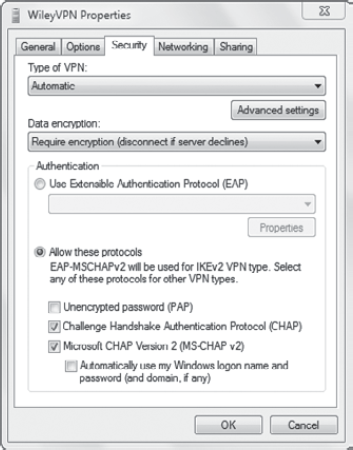
5.1.3. VPN Security Tab
The Security tab has
several important settings that you may need to configure. At the very
least, you should be aware of what can be configured here. Figure 8 shows the choices.
Type Of VPN refers to the
tunneling protocol used. As a reminder, Windows 7 supports IKEv2, SSTP,
PPTP, and L2TP. When it is set to Automatic (as shown), it will try each
of these protocols until it connects.
You can also select the
tunneling protocol to match what the VPN server is using. This will save
time on the connection. In addition, it will make the configuration
easier. For example, if you select IKEv2, it limits the authentication
choices to only the more advanced type of authentication needed by
IKEv2.
The Data Encryption setting
allows you to specify how the data is encrypted. This includes four
choices. The first choice is the default.
Require Encryption (Disconnect If Server Declines)
Maximum Strength Encryption (Disconnect If Server Declines)
Optional Encryption (Connect Even If No Encryption)
No Encryption Allowed (Server Will Disconnect If It Requires Encryption)
NOTE
If the VPN is
connecting over the Internet, it's highly recommended that you use
either Require Encryption or Maximum Strength Encryption. This ensures
that any data transmitted over the VPN tunnel is protected from
interception.
The bottom of the screen
shows the authentication protocols that you can select. As a reminder,
you use authentication to prove who you are. This is commonly done with
either a user name and password or a smart card.
If you're using a user name
and password, you should use Challenge Handshake Authentication Protocol
(CHAP) or Microsoft CHAP Version 2 (MS-CHAP v2). Password
Authentication Protocol (PAP) sends the credentials in clear text and
should be avoided. Again, your choice will depend on what the VPN server
expects. If multiple choices are selected on the client, Windows 7 will
attempt the more secure protocols first and continue down the list
until the connection completes.
If the VPN server is
configured to require smart cards or another stronger protocol, you
would select Use Extensible Authentication Protocol (EAP). This
drop-down list includes three Microsoft choices and several AuthorID
choices for third-party solutions. The three Microsoft choices are
Microsoft: Smart Card Or Other Certificate (Encryption Enabled)
Microsoft: Secured Password (EAP-MSCHAP v2) (Encryption Enabled)
Microsoft: Protected EAP (PEAP) (Encryption Enabled)
When you select any of these
settings, you can also click the Properties button. The Properties page
that appears will be different depending on what is selected. For
example, if you have selected Microsoft: Smart Card Or Other
Certificate, you'll see the screen shown in Figure 9. If you've selected Microsoft: Protected EAP (PEAP), you'll see a different screen.
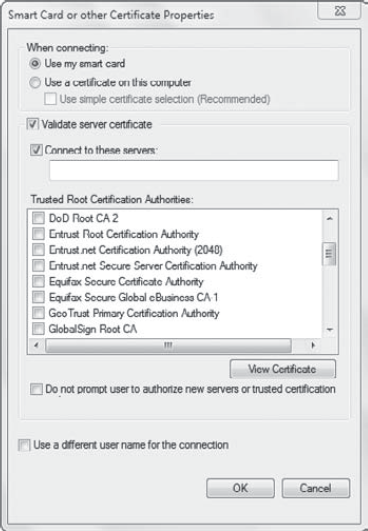
Notice that you can
configure this to use a smart card. You can also configure it to use a
certificate if needed by the VPN server.
5.1.4. VPN Networking Tab
The Networking tab allows
you to select or deselect protocols and services available to the VPN
connection. These include the protocols needed to connect to the VPN
server and the protocols needed after you connect.
Figure 10 shows the Networking tab with the default selections.
At least IPv4 or IPv6 is
needed for connectivity. Both are selected by default, which allows IPv6
to be used when it's available and IPv4 to be used when IPv6 isn't
available. It's possible to have an IPv6 connection over the Internet
and then use an IPv4 connection on the internal network.
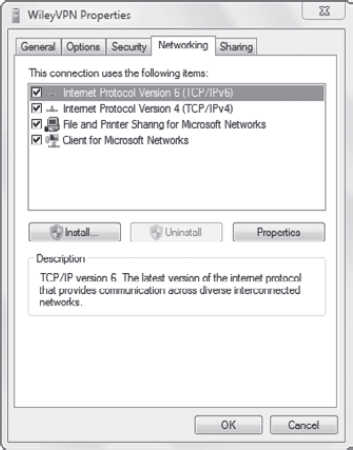
|
You can enable both IPv4 and
IPv6. IPv6 will be used when available (such as on the Internet), and
IPv4 will be used when IPv6 is not available.
|
|
File And Printer Sharing
For Microsoft Networks allows other computers in the network to access
resources on your computer. The Client For Microsoft Networks client is
needed to access resources on other computers.
5.2. Enable Logging
If you're unable to get the
VPN connection working by double-checking and reconfiguring the
settings, you can enable logging. Select the Enable Logging check box
(shown in Figure 5 earlier) and try to connect again. This will create logs that you can read to reveal more details on the problem.
|
The RAS logs can take up extra
resources and may impact the performance of your system if you leave
them running. Think of these as debugging logs. Turn them on when you
need them. However, remember to turn them off once you've resolved the
problem.
|
|
When you enable logging, log files are created in the %windir%\tracing directory. If the tracing
directory doesn't exist yet, it will be created when you enable
logging. There will also be additional entries enabled in the Security
Event log available from the Event Viewer.
Instead of selecting the Enable Logging check box from the error page, you can use the netsh
command to enable or disable logging. These commands need to be run
from an administrative command prompt to work completely. If you don't
run them with administrative permissions, all of the logs won't be
enabled.
This command will enable logging:
netsh ras diag set tracefacilities enable
This command will disable logging:
netsh ras diag set tracefacilities disable
5.3. Run Diagnostics
On the error page for the connection (shown earlier in Figure 5),
you can click the Diagnostics link. This will bring you to the Remote
Access Preferences dialog box with the Diagnostics tab selected, as
shown in Figure 11.
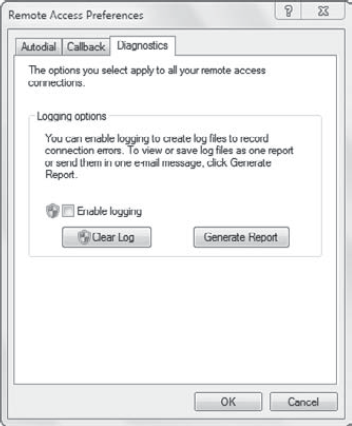
You can click the Generate
Report button to run detailed diagnostics on your system. This will
take a few minutes to complete. When it does complete, it will open the
report in Internet Explorer.
This report is quite
extensive. It retrieves data from more than 40 logs and puts them into
an HTML file. It performs several installation information checks,
performs several configuration checks, and records all of the results in
the file.
The data in this report is
rather deep. However, if you're troubleshooting a problem that is
eluding your best efforts, this report may give you exactly what you
need.
6. A Few Words about Teredo
Windows 7 supports Teredo,
and Teredo becomes very apparent when you are working with VPNs. Teredo
is a tunneling protocol that encapsulates IPv6 packets within IPv4. It
is intended to be a temporary bridge as all networks transition from
IPv4 to IPv6.
Teredo uses Teredo clients
and Teredo servers. In this context, Windows 7 will be the client.
Windows 7 clients use the server located at teredo.ipv6.microsoft.com as their Teredo server.
The server is used to detect
what type of NAT is between the client and the server so that Teredo can
determine how to encapsulate the packets.
Teredo can be in one of four possible states in Windows 7:
Qualified state
IPv6 traffic is able to flow into and out of the system over Teredo.
- Dormant state
Teredo is enabled but
not active. Applications that need to use IPv6 traffic can activate
Teredo. IPv6 traffic isn't sent while in the Dormant state.
- Probe state
When Teredo is
transitioning between the Dormant state and the Qualified state, it will
be listed as in the Probe state. During this time, it attempts to
contact a Teredo server. If it can't connect to a Teredo server, it will
enter the Offline state; but if it can connect, it will enter the
Qualified state.
- Offline state
This indicates that Teredo is not working. It could be placed in the Offline state by a command such as netsh int teredo set state disabled.
It will go into this state if it detects a domain controller indicating
it's in a managed environment (unless the state is set to enterprise
client). It can also go into this state if it is unable to transition
from a Dormant state to a Qualified state.
|
The state of Teredo in
Windows 7 isn't dependent on whether the system is joined to a domain.
It is dependent on whether it can detect a domain controller. If a
workgroup computer is in a network with a DC, Teredo will be in Offline
state once it detects the DC. On the other hand, if a user takes a
domain-joined laptop home, Teredo won't be able to detect the DC and the
state will change to Dormant.
|
|
You can use the netsh
command to manage the state of Teredo. The following commands may be
useful when you're working or troubleshooting issues with Teredo.
You can use this command to view the state of Teredo:
netsh int teredo show state
You'll see output similar to Listing 1.
Example 1. Output of the netsh int teredo show state command
C:\>netsh int teredo show state
Teredo Parameters
---------------------------------------------
Type : client
Server Name : teredo.ipv6.microsoft.com.
Client Refresh Interval : 30 seconds
Client Port : unspecified
State : dormant
|
You can use this command to disable Teredo:
netsh int teredo set state disabled
You can use this command to enable Teredo:
netsh int teredo set state enabled
You can use this command to enable Teredo even when a domain controller is present:
netsh int teredo set state enterpriseclient