Mobile users often need to have access to an internal
network even when they aren't at the company. Many companies use
different types of remote access solutions to support them.
Whereas the
administrators are responsible for designing, implementing, and
maintaining the remote access servers, desktop administrators are
required to support the end users. If you're the desktop administrator,
you'll want to have a good understanding of all the pieces. This section
covers the following topics:
Remote access overview
Creating a dial-up connection
Creating a VPN connection
Adding a certificate
Troubleshooting a VPN client
A few words about Teredo
1. Remote Access Overview
Remote access allows users
to connect to the company's internal network while they are away from
the network. They can be traveling, working at a remote customer's site,
or working from home. Users can connect with a dial-up connection or a
virtual private network connection.
A VPN connection allows a user
to connect to a private network over a public network. The majority of
the time, the public network is the Internet. Some VPN connections that
connect offices use leased lines instead of the Internet as the public
network.
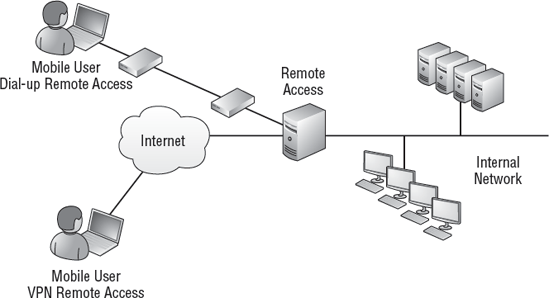
Consider Figure 1.
This shows two types of remote access connections. At the top left, the
user is connecting to the remote access server using dial-up. The
client needs to have a modem and access to phone lines. Similarly, the
remote access server has a modem and access to phone lines.
The second mobile user
(at the bottom left) is connecting using a VPN. The client first
connects to the Internet. Once connected to the Internet, the client can
then connect to the remote access server. The remote access server must
have a public IP address and a connection to the Internet.
NOTE
The terms remote access server and VPN server are sometimes confusing. Remote access server is generic, indicating that it provides remote access. However, VPN
server is specific, indicating that remote access is provided using a
VPN connection. In other words, a VPN server may also be called a remote
access server. However, a remote access server that provides only
dial-up access isn't a VPN server.
VPN connections use
tunneling protocols. These tunneling protocols include encryption and
provide additional protection for the connection. Windows 7 supports the
following four tunneling protocols:
- Internet Key Exchange version 2 (IKEv2)
IKEv2 is the newest
tunneling protocol and was introduced with Windows 7 and Windows Server
2008 R2. It can also go through a NAT server and provides an additional
choice over PPTP. Windows Vista, Windows Server 2008 servers, or older
versions do not support IKEv2.
- Secure Shell Tunneling Protocol (SSTP)
SSTP was introduced
with Windows Vista and Windows Server 2008. It uses SSL to encrypt the
traffic as HTTPS traffic. It can go through a NAT server, providing an
additional choice if your VPN server is located behind a NAT server.
SSTP provides better security than PPTP and supports both IPv4 and IPv6.
You can use SSTP with clients running Microsoft Windows Vista, Windows
Server 2008, or later versions.
- Layer 2 Tunneling Protocol (L2TP)
L2TP was developed by
combining the strengths of Microsoft's PPTP with the strengths of
Cisco's Layer 2 Forwarding (L2F) protocol. It encrypts data using IPSec
(and is shown as L2TP/IPSec) and supports both IPv4 and IPv6. The only
drawback is that IPSec can't go through a network address translation
server. If the VPN had to go through a NAT, the previous recommendation
was to use PPTP. You can use L2TP/IPSec with clients running Microsoft
Windows 2000 or later versions.
- Point-to-Point Tunneling Protocol (PPTP)
PPTP is the oldest
of the four protocols. It encrypts data using Microsoft Point-to-Point
Encryption (MPPE). PPTP is not supported on IPv6. While PPTP is still
used, you can expect it to be used less often in the future. You can use
PPTP with clients running Microsoft Windows 2000 or later versions.
|
When taking the exams,
remember that PPTP does not support IPv6. If your clients must go over
IPv6, you will not be able to use PPTP. IKEv2 is the most likely choice
for Windows 7 clients connecting to a Windows Server 2008 R2 server.
|
|
IKEv2, L2TP/IPSec, and SSTP provide several important security protections:
Data confidentiality by encrypting the data
Data integrity (ensures the data hasn't been modified)
Data authentication (verifies the hosts)
IKEv2 and SSTP both require
the use of a Public Key Infrastructure to issue certificates. IPSec will
work without a certificate using a pre-shared key, but the use of a
certificate is highly recommended.
When you create a VPN
connection, it will default to Automatic for the tunneling protocol. In
other words, you don't have to choose which tunneling protocol the
server is using. Windows 7 will attempt to connect to a VPN server using
the different tunneling protocols in the following order:
Windows 7 also supports a neat
feature with IKEv2 connections called MOBIKE, or VPN Reconnect. MOBIKE
allows clients to reconnect easily a broken VPN connection without user
interaction.
This can be very useful for
mobile clients that have unreliable connections. When they reconnect,
the original security association is retained instead of creating a new
one. This requires only about a tenth of the traffic and results in a
quick reconnection for the clients.
2. Creating a Dial-up Connection
The Set Up A New
Connection Or Network choice on the Network and Sharing Center includes
several wizards to create connections.
One choice is Connect To A
Workplace. You can use this wizard to create either a dial-up or a VPN
connection. When you select this choice, you'll be prompted either to
use your Internet connection to connect via a VPN or to dial directly.
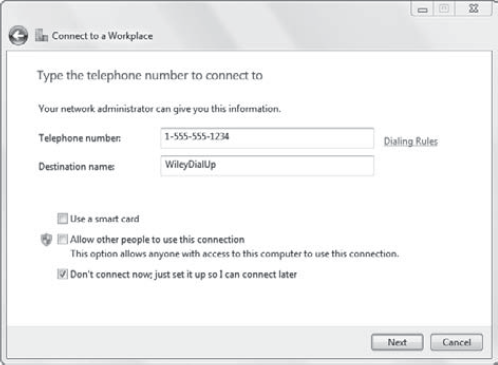
If you choose to dial directly,
you'll be prompted to pick a modem (if you have more than one), and then
you'll see a screen similar to Figure 2. You enter the phone number of the remote access server and the name of the connection on this screen.
If your company requires
the use of a smart card, you can check the Use A Smart Card check box.
You can also select the Allow Other People To Use This Connection check
box. This will make the profile available for all users who can log on
to the computer.
The Dialing Rules link
allows you to configure rules that may be required. For example, you may
need to dial 9 to get an outside line or use specific carrier codes for
long-distance or international calls.
Launch the Network and Sharing Center. Click Start => Control Panel => Network and Internet => Network and Sharing Center. Click Set Up A New Connection Or Network. Select Connect To A Workplace. Click Next. If
you have existing connections, you'll be prompted to use one of them or
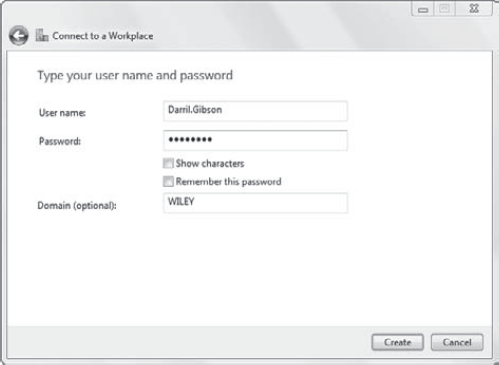
create a new one. Select No, Create A New Connection, and click Next. Select Dial Directly. If you have more than one modem, you will see a list of modem choices. Select a modem. Type the telephone number and the connection name in the Telephone Number and Destination Name text boxes. Select Don't Connect Now; Just Set It Up So I Can Connect Later. Click Next. Enter
your user name and password in the User Name and Password text boxes.
If your network is using a domain, enter the domain name. Your display
will look something like the following graphic.
Click Create to create the connection. You can then click Connect Now to test it or click Close.
|
After you create a dial-up
connection, it will show up in several places. Two links are available
directly from the Network and Sharing Center.
- Connect To A Network
You can select the dial-up connection from here and click Connect to connect to the remote access server.
- Change Adapter Settings
You can select the dial-up connection from here and select Start This Connection to connect to the remote access server.
Figure 3 shows the screen you'll see when you choose either of these methods.
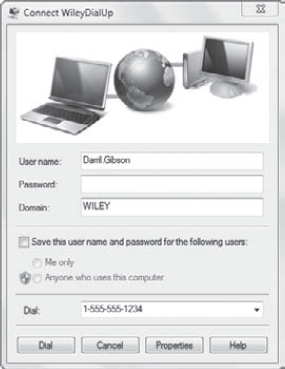
If you didn't save the
password, you can enter it and then click Dial. You can also access
advanced properties for the connection by clicking the Properties
button.