By default, ActiveSync is configured to use
Integrated Windows authentication. This form of authentication works
fine if access to the server is over a trusted internal network, but is
not feasible for access over the Internet, which is where most Mobile
devices originate from.
Because of this limitation, a
form of authentication that can be sent across the Internet must be
used. This effectively limits the ActiveSync server to using Basic
authentication, which is supported by most web browsers and devices. The
problem with Basic authentication, however, is that the username and
password that the user sends is effectively sent in clear text, and can
be intercepted and stolen in transit. In addition, mail messages and
other confidential information are transmitted in clear text, a huge
security issue.
The solution to this
problem is to use what is known as Secure Sockets Layer (SSL) encryption
on the traffic. SSL encryption is performed using Public Key
Infrastructure (PKI) certificates, which work through the principle of
shared-key encryption. PKI SSL certificates are widely used on the
Internet today, any website starting with an https:// uses them, and the
entire online merchant community is dependent upon the security of the
system.
For
ActiveSync, the key is to install a certificate on the server so that
the traffic between the device and the server is protected from prying
eyes. There are effectively two options to this approach as follows:
Use a third-party certificate authority—
A common option for many organizations is to purchase a certificate for
ActiveSync (and other Exchange HTTP access methods such as OWA) from a
third-party trusted certificate authority (CA), such as VeriSign,
Thawte, or others. These CAs are already trusted by a vast number of
devices, so no additional configuration is required. The downside to
this option is that the certificates must be purchased and the
organization doesn’t have as much flexibility to change certificate
options.
Install and use your own certificate authority—
Another common approach is to install and configure Windows Server 2003
Certificate Services to create your own CA within an organization. This
gives you the flexibility to create new certificates, revoke existing
ones, and not have to pay immediate costs. The downside to this approach
is that no browsers or mobile devices will recognize the CA, and error
messages to that effect will be encountered on the devices unless the
certificates are trusted.
Installing a Third-Party CA on a CAS
If a third-party
certificate authority will be used to enable SSL on a CAS, a certificate
request must first be generated directly from the CAS. After this
request has been generated, it can be sent to the third-party CA, who
will then verify the identity of the organization and send it back,
where it can be installed on the server.
When deciding which CA to
use, keep in mind that Windows Mobile devices automatically trust the
certificate authorities of the following organizations:
If an internal CA will
be utilized, this section and its procedures can be skipped, and you
can proceed directly to the subsequent section titled “Using an Internal Certificate Authority for OWA Certificates.”
To generate an SSL certificate request for use with a third-party CA, perform the following steps:
1. | From the CAS, open IIS Manager (Start, All Programs, Administrative Tools, Internet Information Services [IIS] Manager).
|
2. | In
the console tree, expand SERVERNAME (local computer) – Web Sites,
right-click the OWA Virtual Server (typically named Default Web Site),
and click Properties on the shortcut menu.
|
3. | Select the Directory Security tab.
|
4. | Under Secure Communications, click the Server Certificate button.
|
5. | On the welcome screen, click Next to continue.
|
6. | From the list of options displayed, select Create a New Certificate, and click Next to continue.
|
7. | From the Delayed or Immediate Request dialog box, select Prepare the Request Now, But Send It Later, and then click Next.
|
8. | Type a descriptive name for the certificate, such as the one shown in Figure 1, leave the bit length at 1024, and click Next to continue.
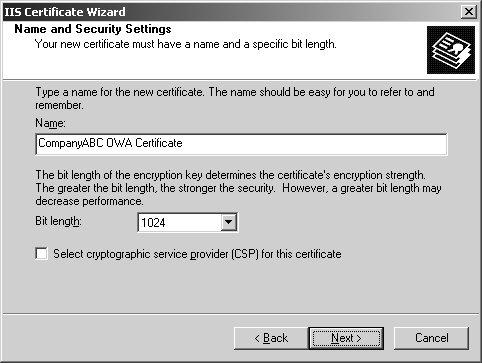
|
9. | Enter
the name of the organization and what OU will be associated with the
certificate. These fields will be viewable by external users, and should
accurately reflect the organizational structure of the requestor.
|
10. | Enter
a common name for the OWA website in the form of the FQDN. An example
of this is mail.companyabc.com. Click Next to continue.
Note
If the ActiveSync
site will be made accessible from the Internet, the common name of the
site needs to be made accessible from the Internet via a DNS A record.
|
11. | Enter
the appropriate information into the Geographical Information dialog
box, such as state, city, and country. Abbreviations are not allowed.
Click Next to continue.
|
12. | Enter a filename for the certificate request, such as C:\owacert.txt, and click Next to continue.
|
13. | In the Request File Summary dialog box, review the summary page for accuracy, and click Next to continue.
|
14. | Click Finish to end the Web Server Certificate Wizard.
|
After the certificate request has been generated, the text file, which will look similar to the one shown in Figure 2,
can then be emailed or otherwise transmitted to the certificate
authority via their individual process. Each CA has a different
procedure, and the exact steps need to follow the individual CA’s
process. After an organization’s identity has been proven by the CA,
they will send back the server certificate, typically in the form of a
file, or as part of the body of an email message.
The certificate then needs to be installed on the server itself. If it was sent in the form of a .cer
file, it can simply be imported via the process described next. If it
was included in the body of an email, the certificate itself needs to be
cut and pasted into a text editor such as Notepad and saved as a .cer file. After the .cer file has been obtained, it can be installed on the CAS using the following process:
1. | From the CAS, open IIS Manager (Start, All Programs, Administrative Tools, Internet Information Services [IIS] Manager).
|
2. | In
the console tree, expand SERVERNAME (local computer) – Web Sites,
right-click the OWA Virtual Server (typically named Default Web Site),
and then click Properties on the shortcut menu.
|
3. | Select the Directory Security tab.
|
4. | Under Secure Communications, click the Server Certificate button.
|
5. | On the welcome screen, click Next to continue.
|
6. | From
the Pending Certificate Request dialog box, select Process the Pending
Request and Install the Certificate, and click Next to continue.
|
7. | Enter the path and filename where the .cer file was saved to (the Browse button can be used to locate the file), and click Next to continue.
|
8. | Click Finish to finalize the certificate installation.
|
At this point in the
process, SSL communication to the CAS can be allowed, but forcing SSL
encryption for the ActiveSync traffic requires more configuration.