When you use SSL to secure a connection, third
parties that might be intercepting your transmission are unable to
access the content of that communication. This is especially important
today when many clients are accessing sensitive organizational
communication over insecure networks such as the wireless access point
at the local coffee shop. IT departments must often support operating
systems that do not support Microsoft Outlook. Alternative mail clients
often use either the IMAP4 or POP3 protocols to retrieve messages from
Exchange mailboxes, and you will learn how to configure that access in
this lesson. Autodiscover is an automatic configuration service designed
for recent versions of Outlook and mobile clients. In this lesson, you
will learn how to configure SSL certificates for use with Client Access
servers, the steps that you take to configure ActiveSync, what you need
to do to allow clients to use the IMAP4 and POP3 protocols to access
their mailboxes, and how to configure Autodiscover.
1. Client Access Server Certificates
Secure Sockets Layer
(SSL) certificates allow clients to establish an encrypted connection
to be established between a client and a Client Access server. SSL
certificates, also called server certificates,
also have the added benefit of verifying the identity of the Client
Access server to the client. When you install Exchange on a computer, it
installs a default self-signed certificate. As a trusted Certificate
Authority (CA) did not create or sign this certificate, the certificate
will be trusted only by other Exchange servers in the same organization,
not by any clients in the same organization. Administrators need to
take extra steps to get clients to trust these certificates, and it is
often easier to look for an alternative solution, such as getting a
certificate from an internal CA. The Exchange self-signed certificate
will have Subject Alternative Names (SANs) that correspond to the name
of the Exchange server, including the server name and the server’s fully
qualified domain name.
SANs are a
certificate functionality that allows a certificate to be mapped to
multiple fully qualified domain names. For example, Internet clients
might access a server as owa.contoso .com, and internal network clients
might access the same server as owa.contoso.internal. If the certificate
did not support SANs, the SSL certificate would support only one name,
and clients accessing
the server using the other name would encounter an error.
SSL certificates are
usually signed by an internal or a trusted third-party CA. Certificates
signed by trusted third-party CAs are trusted by both internal and
external clients, but obtaining these certificates can cost money.
Obtaining a certificate from an internal CA has no associated charge,
but clients outside your organization are unlikely to trust the
certificate. You obtain a certificate by running the New Exchange
Certificate Wizard and submitting the resulting certificate request file
to your CA of choice.
To run the New Exchange Certificate Wizard, perform the following general steps:
In
the Exchange Management Console (EMC), click on the Server
Configuration node and then click on New Exchange Certificate in the
Actions pane. This will launch the New Exchange Certificate Wizard.
Provide a friendly name for the certificate and click Next.
On
the Domain Scope page, specify whether you want to apply this
certificate to all subdomains using wildcards. This option allows you to
add subdomains at a later stage without having to update an existing
certificate.
On
the Exchange Configuration page, use the arrows to expand access so
that you can fill in details about the roles that you want the
certificate to service. For example, for a Client Access server where
you wanted to support Exchange Web Services, Outlook Anywhere, and
Autodiscover, you would expand and configure the settings, as shown in Figure 1.
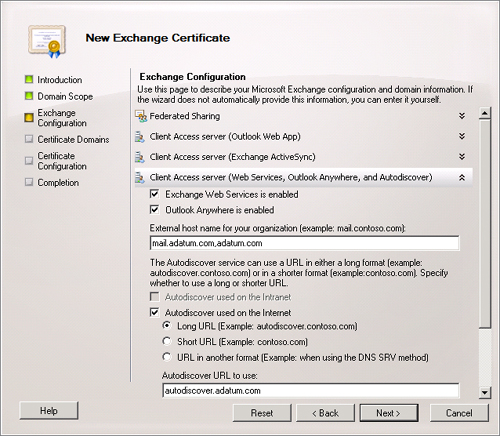
You
can use this page of the wizard to configure a request for all roles
the server holds. To do this, expand and complete each relevant section.
Review the Certificate Domains that the request will contain. On this page, you can add additional SANs.
On
the Organization and Location page, enter organization and location
information. You also specify the location to which the wizard should
save the certificate request file.
When an appropriate CA has
processed your certificate request, you can use the Complete Pending
Request option, available when the friendly name is selected within the
EMC, to install the newly requested certificate.
Once you have installed the
certificate, you will be able to assign services to the certificate.
Assigning services configures specific services on the Exchange server
to use the certificate for identification and secure communication. To
assign a specific certificate to Exchange services, perform the
following general steps:
In
the EMC, select the certificate by selecting the Server Configuration
node and then select the Exchange server where you installed the
certificate.
Select
the certificate and then click on Assign Services to Certificate in the
Actions pane. This will bring up the Assign Services to Certificate
Wizard. Select the servers where you want to assign the certificate.
On the Select Services page, as shown in Figure 2, select each service to which you want Exchange to assign the certificate.
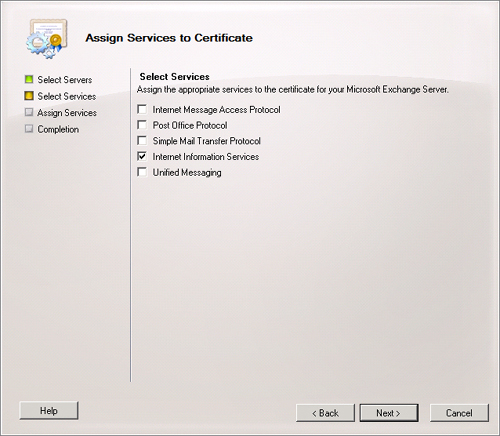
Note:
DIGITAL CERTIFICATES AND SSL
To learn more about using digital certificates and SSL with Client Access servers, consult the following reference on TechNet: http://technet.microsoft.com/en-us/library/dd351044.aspx.