4. Implementing a Discovery Search
A discovery search is a multimailbox search that returns
email messages that meet specified conditions. By default, a discovery search
will search all mailboxes in an Exchange Server 2010 organization. You can,
however, specify the source mailboxes that you want to include in the search by
using the SourceMailboxes parameter of the
New-MailboxSearch EMS cmdlet.
Search results are saved in the mailbox Discovery Search Mailbox in a folder
with the same name as the search. Exchange Server 2010 Setup creates a mailbox
named Discovery Search Mailbox by default. Note that if you do not specify a
search query, the entire content of all the specified mailboxes is copied to the
target mailbox.
You can use the EMS or the Exchange Control Panel (ECP) in OWA to create a
discovery search. This article concentrates on server-side configuration and the
use of the New-MailboxSearch EMS cmdlet.
For example, you want to create the discovery search Adatum-ExchangeProject.
The search should return email messages that contain the words
“Adatum” and “Exchange project” and that are sent or
received from January 1, 2011, through December 31, 2011. The search runs
against all mailboxes on all Exchange 2010 Mailbox servers in the organization.
Full logging is enabled for the search. This search includes items that cannot
be indexed in Exchange Search. This last condition is specified by including the
IncludeUnsearchableItems switch in the command. By default, such items are not
included in search results. To create this search, you will enter the following
command:
New-MailboxSearch -Name "Adatum-ExchangeProject" -StartDate "1/1/2011" -EndDate
"12/31/2011" -TargetMailbox "Discovery Search Mailbox" -SearchQuery '"Adatum" and
"Exchange project"'-MessageTypes Email -IncludeUnsearchableItems -LogLevel Full
You can use the –MessageTypes parameter to specify the message types to
include in the search. Valid values can include one or more of the
following:
Email
Meetings
Tasks
Notes
Docs
Journals
Contacts
Instant Messaging (IM)
If you do not specify a message type, all message types are included.
4.1. Stopping, Restarting, or Removing a Discovery Search
You can stop, restart, or remove a discovery search from an OWA client or
from an Exchange Server 2010 client at any time. On the OWA client, click My
Organization, click Reporting, and then click Mailbox Searches. To stop a
search, select the search and then click the Stop Search icon. To start a
stopped search, select the search and then click the Restart Search icon.
When a warning appears stating that the existing search will be removed from
the target mailbox, click Yes. If you want to remove a search, select the
search and click the Remove Search icon (red cross).
The following EMS command stops the discovery search
Adatum-ExchangeProject:
Stop-MailboxSearch -Identity "Adatum-ExchangeProject"
The following EMS command starts the discovery search
Adatum-ExchangeProject:
Start-MailboxSearch -Identity "Adatum-ExchangeProject"
The following EMS command removes the discovery search
Adatum-ExchangeProject:
Remove-MailboxSearch -Identity "Adatum-ExchangeProject"
11.3.4.2. Modifying a Discovery Search
You can use commands based on the Set-MailboxSearch
EMS cmdlet to modify a discovery search. For example, the following command
modifies the discovery search Adatum-ExchangeProject to search mailboxes
belonging to members of the Accountants distribution group:
Set-MailboxSearch -Identity "Adatum-ExchangeProject " -SourceMailboxes "Accountants"
5. Placing a Mailbox on Legal Hold
Organizations are sometimes required to preserve
electronically stored information such as email messages that could be relevant
to litigation. An organization may decide preserve all email related to a
specific topic or all email sent to or by selected individuals. Relying on
individual users not to delete their email messages might not always work, and
suspending automatic deletion mechanisms might result in a large volume of
undeleted email. Manual archiving can increase administrative costs.
Exchange Server 2010 offers legal hold as a solution to this problem. Legal
hold enables you to place users on hold and keep their mailbox items in an
unaltered state. You can preserve mailbox items that may have been deleted by
users or automatically by MRM. You can enable discovery searches of items placed
on hold. Finally, legal hold is transparent to the user and does not affect user
experience.
Legal hold uses the Recoverable Items folder (sometimes known as the
dumpster). This folder is hidden from the default view of Outlook, OWA, and
other email clients. Items in the Recoverable Items folder are retained for the
deleted item retention period configured on the user’s mailbox database.
By default, the deleted item retention period is set to 14 days for mailbox
databases.
Items are purged permanently from the Recoverable Items folder on a first-in,
first-out basis when the folder’s storage quota is exceeded or if the item
has resided in the folder for a longer time than the deleted item retention
period. Items in the Recoverable Items folder are not included when calculating
a user’s mailbox quota.
The Recoverable Items folder contains the following three subfolders that
store deleted items in various states and thus facilitate legal hold:
Deletions
Items removed from the Deleted Items folder or hard-deleted from
other folders are moved to this subfolder and are visible to the
user when using the Recover Deleted Items tool in Outlook.
Purges
When a user deletes an item from the Recoverable Items folder the
item is moved to the Purges folder. Items that exceed the deleted
item retention period are also moved to the Purges folder. When the
mailbox assistant processes the mailbox, items in the Purges folder
are typically purged from the mailbox database. However, when you
place the mailbox user on legal hold, the mailbox assistant does not
purge items in this folder.
Versions
When a user who is placed on legal hold changes specific
properties of a mailbox item, the original item is preserved to meet
discovery obligations. A copy of the original mailbox item is
created before the changed item is created, and this copy is saved
in the Versions folder. This process is known as copy on
write.
A legal hold preserves deleted mailbox items and records changes made to
mailbox items. Deleted and changed items are returned in a discovery search.
Legal hold is typically implemented for compliance purposes.
You use commands based on the
Set-Mailbox EMS cmdlet to place a mailbox on legal hold or release a mailbox
from legal hold. Note that it may take up to an hour before the legal hold takes
effect.
The following command places the mailbox [email protected] on legal
hold:
Set-Mailbox [email protected] -LitigationHoldEnabled $true
The following command removes the legal hold on the mailbox
[email protected]:
Set-Mailbox [email protected] -LitigationHoldEnabled $false
6. Creating and Configuring Ethical Walls
An ethical wall is a zone of noncommunication
between distinct departments of a business or organization that prevents
conflicts of interest that might result in the inappropriate release of
sensitive information. Exchange Server 2010 uses transport rules configured on
Hub Transport servers to implement and configure ethical walls. Note that
ethical walls configured in an Exchange organization are concerned only with
email traffic and not with other methods of communication.
Typically, you implement an ethical wall by configuring a transport rule that
rejects messages sent between specified senders and recipients, such as from one
distribution group to another. When you create a transport rule to enforce an
ethical wall, you either specify conditions to define which recipients and
senders to prohibit from sending messages to each other or specify exceptions to
narrow the scope of the transport rule. If you do not specify conditions or
exceptions, the transport rule will block all messages sent to or from
recipients or senders in your organization. Remember also that for transport
rules to be applied to email messages, the messages must be routed by an
Exchange Server 2010 Hub Transport server.
You can create a transport rule
(and hence implement an ethical wall) by using either the EMC or the EMS. The
high-level procedure to use the Transport Rule Wizard in the EMC to create an
ethical wall is as follows:
Start the New Transport Rule Wizard.
On the Introduction page, specify a name and (optionally) a
description. Ensure that the Enable Rule check box is selected.
On the Conditions page in the Step 1. Select Condition(s) box, select
one or more conditions. Typically, for an ethical wall, you would select
Between Members Of Distribution List And Distribution List. For each
condition, in the Step 2. Edit The Rule Description By Clicking An
Underlined Value box, click each blue underlined word and supply the
values to apply to the condition.
On the Actions page, in the Step 1. Select Actions box, select Send
Bounce Message To Sender With Enhanced Status Code. This transport rule
action deletes the message and returns an NDR to the sender of the
message.
In the Step 2. Edit The Rule Description By Clicking An Underlined
Value box, click each blue underlined word and supply the values to
apply to the condition:
Specify the text to display in the Diagnostic Information For
Administrators (the bounce message) section of the NDR returned
to the sender of the rejected message.
Specify the delivery status notification (DSN) code you want
to display in the Diagnostic Information For Administrators
section of the NDR. Valid enhanced status code values are 5.7.1
and any value from 5.7.10 through 5.7.999.
Figure 7 shows the
completed Actions page.
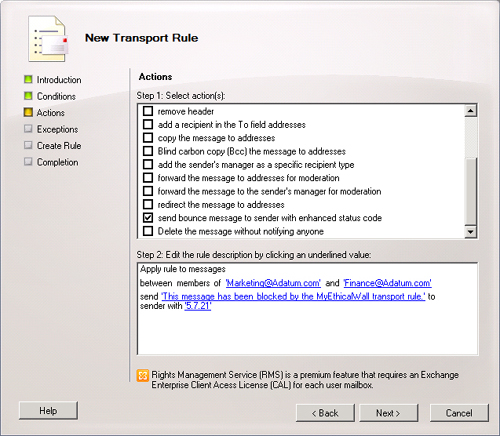
Optionally,
on the Exceptions page, select any exceptions you require and enter
values for these exceptions using the same procedure that you used to
enter values on the Conditions and Actions pages.
On the Create Rule page, review the Configuration Summary. If you are
satisfied with the configuration of the new rule, click New.
When the status of the new rule is shown as Completed, click
Finish.
You can also use the EMS to create an ethical wall. In this example, Trey
Research wants to prevent members of its Finance distribution group and its
Facilities distribution group from communicating. Trey’s Exchange
administrator, Don Hall, decides to implement an ethical wall between the two
groups by using a transport rule.
The RejectMessage transport rule action blocks messages sent to a prohibited
recipient and returns an NDR to the sender, so Don’s procedure uses the
RejectMessageReasonText parameter of the New-TransportRule
EMS cmdlet to implement this action. Don decides to use the
RejectMessageEnchancedStatusCode parameter and specify a custom DSN code
5.7.206. He then needs to associate this code with a custom DSN message. The DSN
message appears in the user information section of the NDR. In this case, the
default reason text “Delivery not authorized, message refused” is
used in the RejectMessageReasonText parameter.
Don also decides to create an exception to this policy that allows members of
the Managers distribution group, who may also belong to either of the two other
groups, to communicate. He uses the ExceptIfFromMemberOf predicate to implement
this exception.
The
first command Don enters on a Trey Research Hub Transport server configures the
ethical wall and defines the custom DSN code as follows:
New-TransportRule "Finance and Facilities Ethical Wall" -Enabled $true -BetweenMemberOf1
[email protected] -BetweenMemberOf2 [email protected]
-ExceptIfFromMemberOf [email protected] -RejectMessageReasonText "Delivery not
authorized, message refused." -RejectionMessageEnhancedStatusCode 5.7.206
Don specifies the text that should be displayed when a message is returned
with the custom DSN code by entering the following command:
New-SystemMessage -DsnCode 5.7.206 -Internal $true -Language En -Text "A message was
sent that violates Trey Research policy. Direct e-mail communication between the Finance
department and the Facilities department is prohibited unless the e-mail is sent by either
departmental manager. For more information, please contact Don Hall at System Support."