Understanding Distinguished Names
Active Directory Domain
Services (AD DS) uses the Lightweight Directory Access Protocol (LDAP).
Every object in AD DS is uniquely identified with a distinguished name
(DN). The DN identifies the object, domain, and Organizational Unit (OU)
or container where it’s located.
Figure 1
shows the Active Directory Users and Computers (ADUC) console with the
properties of a user account in the pearson.pub domain. It’s in the East
OU, which is in the Sales OU.
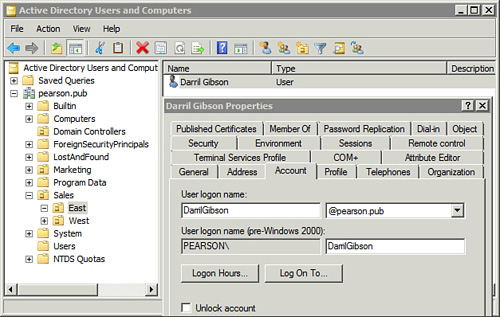
The DN for the user account shown in the figure is
cn=Darril Gibson, ou=East, ou=Sales, dc=pearson, dc=pub
Note
DNs are not case sensitive. You
can use the same case shown in ADUC, or any combination of upper- and
lowercase characters. For example, the following DN is the same, even
though it doesn’t match the case shown in ADUC:
cn=darril gibson, ou=east, ou=sales, dc=pearson, dc=pub
DS commands (such as dsadd, dsmod,
and so on) need the DN to identify the object to create, modify, or
delete. When the DN is used within a command, it must be enclosed within
quotes if it includes spaces. The following table shows the common
components of a DN used with DS commands.
| DN Component | Description |
|---|
| CN | CN
is short for common name. It’s used to indicate the common name of an
object (such as the user’s account name) or the name of a container
(such as the Users or Computers containers). Notice in Figure 7-1 that the account name is Darril Gibson (with a space) but the user logon name is DarrilGibson (with no space). | | OU | OU
is short for Organizational Unit. When multiple OUs are listed, the top
level is listed last. For example, the Sales OU is the top-level OU in Figure 7-1 and is listed as the last OU and closest to the domain.
Note
Nested OUs often give people the most trouble when building the DN. An
easy check is to see whether the top-level OU is next to the domain
component (dc) and the last child OU is listed first.
| | DC | DC
is short for domain component. Notice that each portion of the DC must
be separate. This is incorrect and results in an error: dc=pearson.pub.
It must be separated as dc=pearson, dc=pub. |
Note
Although there are many more DN
components that can be used with LDAP, the three shown in the preceding
table are the ones you need to know for the DS commands.
You can use spaces in some
places in the DN command or omit them. For example, you can use spaces
after the commas to separate the DN components. You also can use spaces
before the equal signs (but not after the equal signs in some commands).
They will be interpreted the same. The following table shows both valid
usage of spaces and one example, which causes errors.
| Valid? | DN Component | Description |
|---|
| Valid | "cn=Joe,ou=east,ou=sales,dc=
pearson,dc=pub"
| No spaces | | Valid | "cn=Joe, ou=east, ou=sales,
dc=pearson, dc=pub"
| Spaces after the commas | | Valid | "cn =Joe, ou =east,
ou =sales, dc =pearson,
dc =pub"
| Spaces after the commas and before the equal (=) signs | | Error | "cn = Joe, ou = east,
ou = sales, dc = pearson,
dc = pub"
| Spaces after the equal (=) sign results in errors in many commands |
Tip
Avoid commas before and after
the equal (=) sign to prevent potential problems. However, it’s common
to use spaces after the commas for readability. Just remember that if
any spaces are used, the entire DN must be enclosed in quotes. Adding Objects with dsadd
You can add objects with the dsadd command. The basic syntax is
Some common object types you
can add are users, computers, groups, and OUs. The following table shows
the syntax to create specific accounts. Each of these commands creates
an account in the pearson.pub domain, in the East OU nested in the Sales
OU.
Note
The dsadd
command creates accounts using the same case you use in the command. In
other words, you can create an account named joe or an account named
Joe, depending on the case you use in the DN. If the DN is lowercase,
the account is built with lowercase.
| dsadd Command | Comments |
|---|
Add a user.
dsadd user dn [-pwd password]
C:\>dsadd user "cn=Joe,
ou=east,ou=sales,dc=pearson,
dc=pub"
C:\>dsadd user "cn=joe2,
ou=east,ou=sales,dc=pearson,
dc=pub" -pwd P@ssw0rd
| Adds a user account. The example adds a user account named Joe to the sales\east OU.
If you don’t include a
password, the account is disabled by default. If you include the
password, but it doesn’t meet the password complexity requirements, the
account is disabled.
However, if you include the password and it meets complexity requirements, the account is enabled (as shown in Figure 2). | Add a group.
dsadd group dn -secgroup
{yes | no} -scope { l | g
| u }
C:\>dsadd group "cn=IT Admins,
ou=east,ou=sales,dc=pearson,
dc=pub" -secgrp yes -scope g
C:\>dsadd group "cn=IT
Admins2, ou=east, ou=sales,
dc=pearson, dc=pub"
C:\>dsadd group "cn=dl_
printer, ou=east, ou=sales,
dc=pearson, dc=pub" -scope l
| You can add security groups (with -secgroup yes) or distribution groups (with -secgroup no). You add different scopes with the -scope switch. Create domain local groups (with -scope l), create global groups (with -scope g), and create universal groups (with -scope u).
Tip
The dsadd group command defaults to a global security group so you can omit the -secgroup and -scope switches.
The examples add two global security groups (IT Admins and IT Admins2) and one domain local security group (dl_printer). | Add a computer.
dsadd computer dn
C:\>dsadd computer "cn=PC-1,
ou=east, ou=sales,
dc=pearson, dc=pub"
| The example command creates a computer named PC-1 in the sales\east OU. |
Tip
You can also identify different
properties for any of these objects. For a full listing of the
properties for any of the objects, use the help command as dsadd user /?, dsadd group /?, or dsadd computer /?.
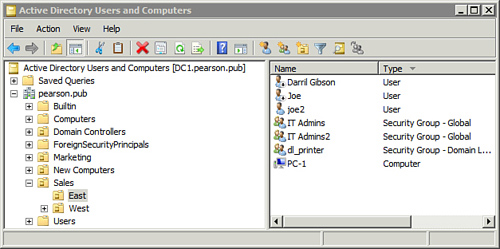
Figure 2
shows ADUC with the accounts created in the previous table. Notice that
the Joe account is disabled because a password wasn’t given. The down
arrow icon in the user icon indicates that it is disabled. Also, notice
that Joe starts with an uppercase J because that’s how the command was
entered, and the joe2 account starts with a lowercase j.
|