Managing Device
Installation
Another powerful control
within a GPO that you have over users is the management device
installations. This has been a security concern for years. How do you
keep users from using USB thumb drives and USB CD/DVD burners to take
copies of confidential data and programs away from the office? I have
heard of companies actually gluing the USB mouse and keyboard into the
USB ports and then filling all other USB ports with glue just to prevent
the use of USB thumb drives that could be used to steal confidential
data. Not exactly the perfect solution, but one that addresses the
security vulnerability. But now what do you do if the mouse or keyboard
fails?
Windows Vista and
Windows Server 2008 have addressed and solved this problem through new
GPO settings that can control what types of devices can be installed by
users, by administrators, or both. These Device Installation GPO
settings can be configured on a Windows Vista or Windows Server 2008
computer under Computer Configuration > Administrative Templates >
System > Device Installation > Device Installation Restrictions,
as shown in Figure 6.
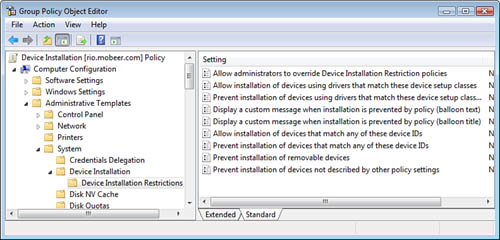
Standard users are not
allowed to install many devices. However, by default, they can install a
handful of devices, like USB thumb drives.
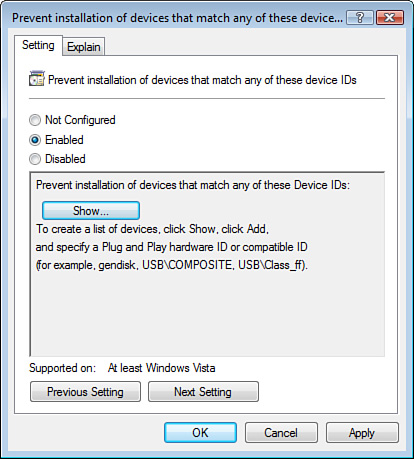
Devices are identified by
Setup Classes (a Registry key) or by Device IDs (a more descriptive
label for the devices). By using these identification values, you can
configure Prevent Installation policies to include USB thumb drives and
other types of devices, as shown in Figure 7.
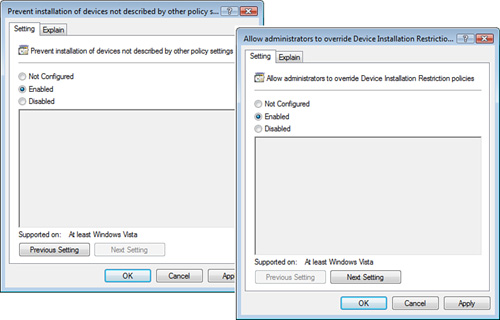
You can configure a GPO to
establish a default Prevent Installation of Devices Not Described by
Other Policy Settings policy, and then you can configure Allow
Installation policies only for specific devices that you want users to
be able to install.
The Prevent Installation of
Devices Not Described by Other Policy Settings policy setting disallows
even an administrator from installing restricted devices. If you need
to allow administrators to install restricted devices, you must enable
the Allow Administrators to Override Device Installation Restriction
Policies, as shown in Figure 8, and link it to the appropriate AD container (site, domain, or
OU).