IPSec for Securing
Network Traffic on the Local LAN
Now that you understand how you can securely control a
user’s access to resources, you must consider the path between the user
and resource server. Is it secure? How certain are you? If a bad guy
has a sniffer running on the network, he can conceivably capture 100% of
the data as it flows between the resource server and user. So much for
permissions, huh? Vista has a tool to defend against this theft of your
data while it’s in transit over the LAN. It is called IPSec.
Alert
Internet
Protocol Security, or IPSec, is an authenticated, encrypted channel between
two computers. The IPSec protocol is built into all Microsoft operating
systems since Windows 2000, including Windows Vista.
IPSec
is not available for use on Windows NT, Windows 9x, or Me.
Remember
that IPSec uses UDP port 500. This port must be opened in any firewalls
between the client and server computers that run IPSec.
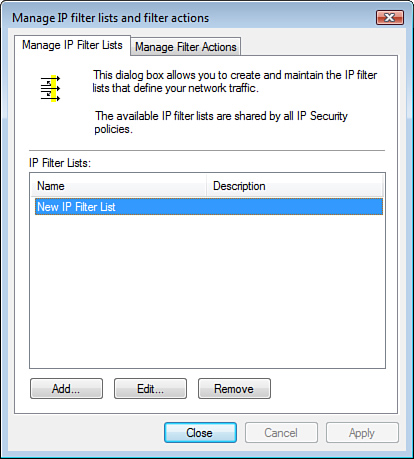
As you can see in Figure 6, the IPSec policy is configured as filter lists and filter
actions. A filter list defines what type of network traffic to apply the
IPSec filter action to. The filter action is the detail of what type of
security the IPSec policy implements after it has filtered and
identified the desired network traffic.
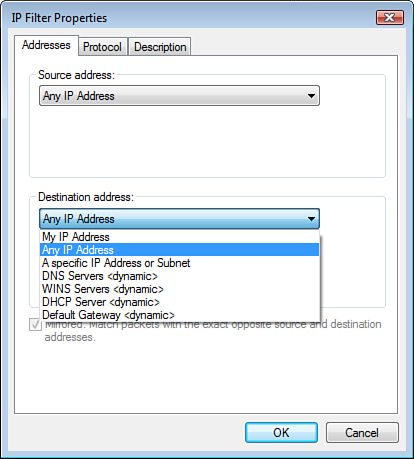
Filter lists include
settings to filter traffic by source and destination IP address,
protocol type, or IP protocol port number, as shown in Figure 7.
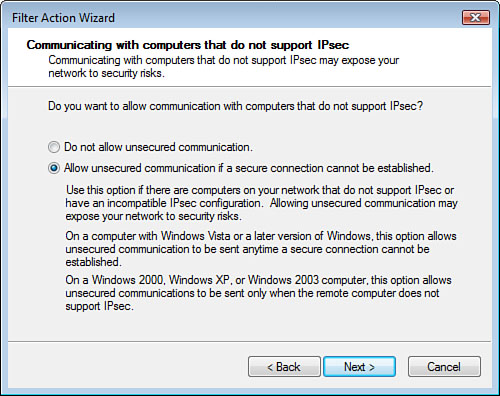
Alert
Filter
actions configuration includes settings for whether the IPSec Policy is
to be mirrored (for inbound and outbound traffic), what type of
encryption to be used, what type of integrity validations are to be
performed, and the type of authentication to be used.
In
addition to these settings, the filter action is used to specify
whether the security settings are for all traffic that matches the
filter list or only the sessions where both client and server can
negotiate an agreeable IPSec configuration, as shown in Figure 8.