The whole reason to build and administer a network is
to provide users with access to resources to make them more productive.
When this access fails, users get cranky, bosses get cranky, and an
administrator’s day just got worse. In the following sections you look
at permissions for folder and file access, access to printers, and ways
to provide secure access for LAN-based connections as well as for
remote-access clients.
Permissions
Permissions have always been a
target for the Microsoft Certification exams. Let’s run through a quick
review of how permissions work.
You basically have six
functional permissions:
R (Read)
W
(Write)
X (Execute—The ability to run
programs)
D (Delete)
P (Permissions—The ability
to change permissions on a file or folder)
O (Ownership—The ability to take
or assign ownership of a file or folder)
These permissions are combined
into practical combinations and can be assigned in two possible places:
Figure 1
shows, on the NTFS partition, at the folder and file level, the
permissions that can be granted; these permissions are described in Table 1.
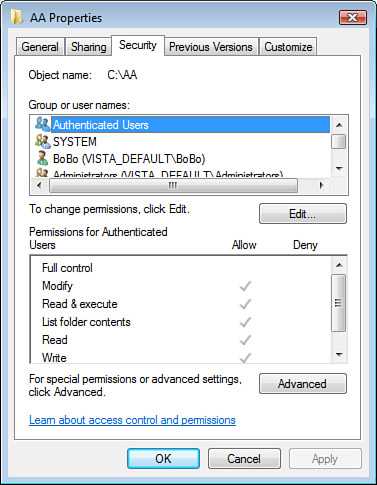
Table 1. NTFS Partition Folder/File Permissions
| NTFS Permissions | Functional Equivalent |
|---|
| Full Control | R W X D P O |
| Modify | R W X D |
| Read & Execute | R X |
| List folder contents | R X |
| Read | R |
| Write | W |
| Special Permissions | Any custom combination
of permissions |
Also notice in Figure 1 that there are Allow permissions and Deny
permissions. Deny permissions are all-powerful and dominate 100% of
Allow permissions that may be granted through other group memberships
for the configured Deny.
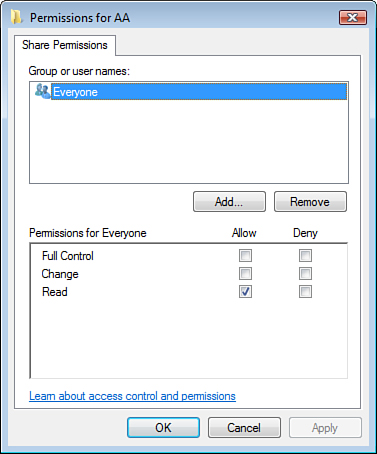
Only folders can be shared.
You cannot share a discrete file. Figure 2 shows, on a shared folder, the permissions
that can be granted; these permissions are described in Table 2.
Table
2. Share Permissions
| Share Permissions | Functional
Equivalent |
|---|
| Full Control | R W X D P O |
| Change | R W X D |
| Read | R X |
Alert
Notice that in
both cases, only the Full Control permission allows you to change the
Permissions (P) and the Ownership (O) of the folder or file.
Determining Effective
Permissions for the Interactive User
If you sit down at the
computer where the files and folder are, you are only subject to the
NTFS permissions as you try to access the files on the NTFS partition.
In this case you are a member of the Interactive group.
As a member of the Interactive
group, your user account and all the groups that you are a member of
(including the Interactive group) get compared to the Access
Control List (ACL) on the file or
folder you are accessing, where you may be granted different
combinations of Allow permissions and Deny permissions. Remember that
the Deny permissions are all powerful and overrule any Allow
permissions.
First, you add all the Allow permissions.
Next, you subtract any Deny permissions.
The permissions that
remain are your effective NTFS permissions and define your access level
when you are a member of the Interactive group.
Table 3
shows how to determine the effective permissions for an interactive user. User1
is a member of the Managers group, the Production group, and the Bad
Boys group. Because he is an interactive user, only NTFS permissions
apply to his access.
Table 3. Effective NTFS Permission
Exercise
| | File1.txt (NTFS) | Functional Equivalent |
|---|
| User1 | No permissions set | |
| Managers | Allow Modify | R W X D |
| Production | Allow Read | R X |
| Bad Boys | Deny W, D | -W -D |
| | Allow = | R W X D |
| | Deny = | -W -D |
| | Effective = | R X |
Microsoft has also added a tab to
the file and folder Advanced Properties to calculate the NTFS effective
permissions. This calculation does not include share
permissions.
Determining Effective
Permissions for the Network User
If you access files and
folders over the network from a remote computer, your access requests
must first pass through the share point, being subject to the
permissions that are managed by the Server service. Then you must still
access the files and folders on the NTFS partition. So you are subject
to both share permissions and NTFS permissions combined. In this case
you are a member of the Network group.
Alert
First,
you must pass through the share point, so you add up all the Allow
permissions at the share point.
Next,
you subtract away any Deny permissions at the share point.
The
permissions that remain are your effective share permissions.
Then
you must access the file on the NTFS partition, so you add up all the
NTFS Allow permissions on the file.
Next,
you subtract away any NTFS Deny permissions on the file.
The
permissions that remain are your effective NTFS permissions.
Now
you have a share permissions list and an NTFS permissions list.
Whatever permissions the two lists have in common are your effective
Network access permissions for the target file.
Look at the example in Table 4 for determining the effective permissions
for a network user.
User1 is a member of the Managers group, the Production group, and the
Bad Boys group. Because he is a Network user, both share and NTFS
permissions apply to his access.
Table 4. Effective Permissions Through a Share
| | Share
Permissions | Functional
Equivalent |
|---|
| User1 | Allow Full Control | R W X D P O |
| Managers | Allow Change | R W X D |
| Production | No permissions set | |
| Bad Boys | No permissions set | |
| | Allow = | R W X D |
| | Deny = | |
| | Effective Share = | R W X D P O |
| | File1.txt (NTFS) | Functional Equivalent |
| User1 | No permissions set | |
| Managers | Allow Modify | R W X D |
| Production | Allow Read | R X |
| Bad Boys | Deny W, D | -W -D |
| | Allow = | R W X D |
| | Deny = | -W -D |
| | Effective NTFS= | R X |
User1’s effective permissions as a Network user are
what the two lists, Share permissions and NTFS permissions, have in
common. User1 is allowed to read folder content and read and execute
files. That’s it. All other Allow permissions have been stripped away.
In this example, the NTFS
permissions do not have the W, D, P, and O permissions. The only
permissions that the two lists have in common are R and X.